An Introduction to Non-Human Identities
All users who handle electronic devices are given an identity. If the name of a human is considered their ‘Identifier’, then the username and password, biometric login, physical authentication key, etc. which they use to authorize and authenticate into systems, applications and other devices are all examples of their ‘identity’. This human identity helps certify anyone who accesses or connects to a machine.
The growth of cloud services, automation, and reliance on digital workflows have introduced the creation of various machine accounts or ‘cyber identities’. They are used to simplify complex and repetitive workflows that would otherwise require continuous human interaction/intervention. They can also streamline certain tasks to increase operational efficiency.
OT and IoT Advancements
Industrial OT leverages service accounts for their controllers and completely automate data collection, machine operations and robotic processes (RPA) with minimal to no human intervention.
IoT aims to create a world where physical utilities seamlessly integrate into the IT environment to participate in the business. This includes both consumer electronics like smart devices, security cameras etc. and industrial devices like embedded sensors and actuators that use NHIs to communicate with one another.
Artificial Intelligence in Play
We have moved far ahead from simple AI agents such as chatbots and co-pilots, these early monolithic systems had low autonomy and heavily relied on human input. ‘Digital AI workers’ or Agents now construct their own instructions, augmenting human input and becoming autonomous to a stage where they can create more non-human identities themselves to creatively carry out their tasks.
What is a non-human Identity (NHI)?
Non-human identities can be defined as the unique cyber identities used by applications, servers, and other devices to certify themselves when connecting to other systems and services. Non-human identities create connections to bridge the gap between business that have multiple disparate environments in the hybrid-cloud era.
Their primary function is to enable machine-to-machine access within a software ecosystem. Non-human identities are also known as ‘non-carbon’ users or ‘machine identities’ to represent their digital presence.
NHIs are vital to mimic actions that a human would have to perform multiple times or actions that are highly complex and cannot afford errors. A few examples of this are ‘consent fatigue’: the need to constantly approve permissions for applications and processes, and ‘data manipulation’: operations like filtering, sorting, merging, aggregating, and transforming data. In both these cases, NHIs are used - Oauth Service for consent automation Accounts and RPAs for data operations.
Are Non-human Identities and Machine Identities Different?
In most cases, research articles and surveys portray machine identities and non-human identities to be one and the same. However, machine identities generally refer to the wide range of identities associated with systems, and software. And non-human identities encompass the overall governance and visibility of these machine identities, CIEM tools, SaaS applications and service accounts and so on.
Where can non-human identities be found?
Non-human identities are spread across the enterprise IT environment to support and enable various operations. In a typical digital ecosystem, they are prevalent across cloud services (Google, Azure, and AWS), Code (CI/CD pipelines), SaaS applications, and a few hosted resources. A representative diagram of the distribution is shown below.
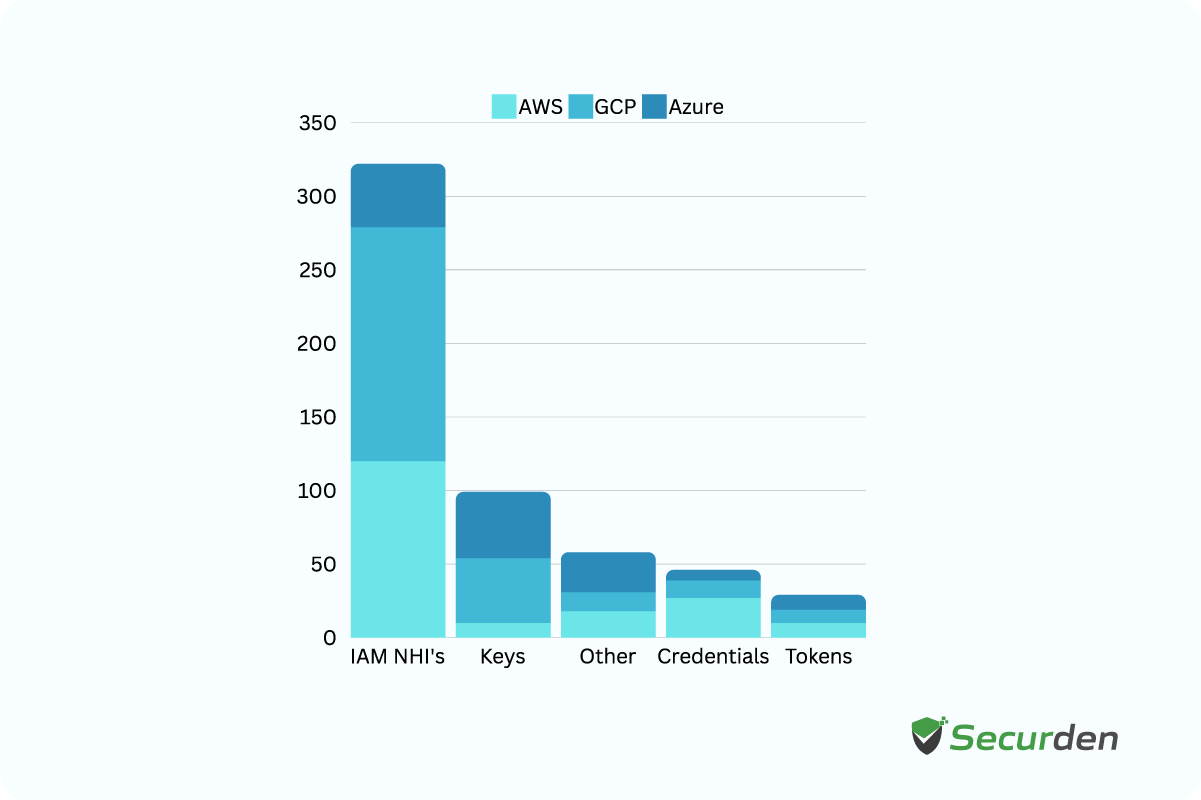
Distribution of NHI’s on Cloud Service Providers
In cloud environments, NHIs are crucial to achieve a solid cybersecurity strategy, helping decrease business risk and security breaches significantly.
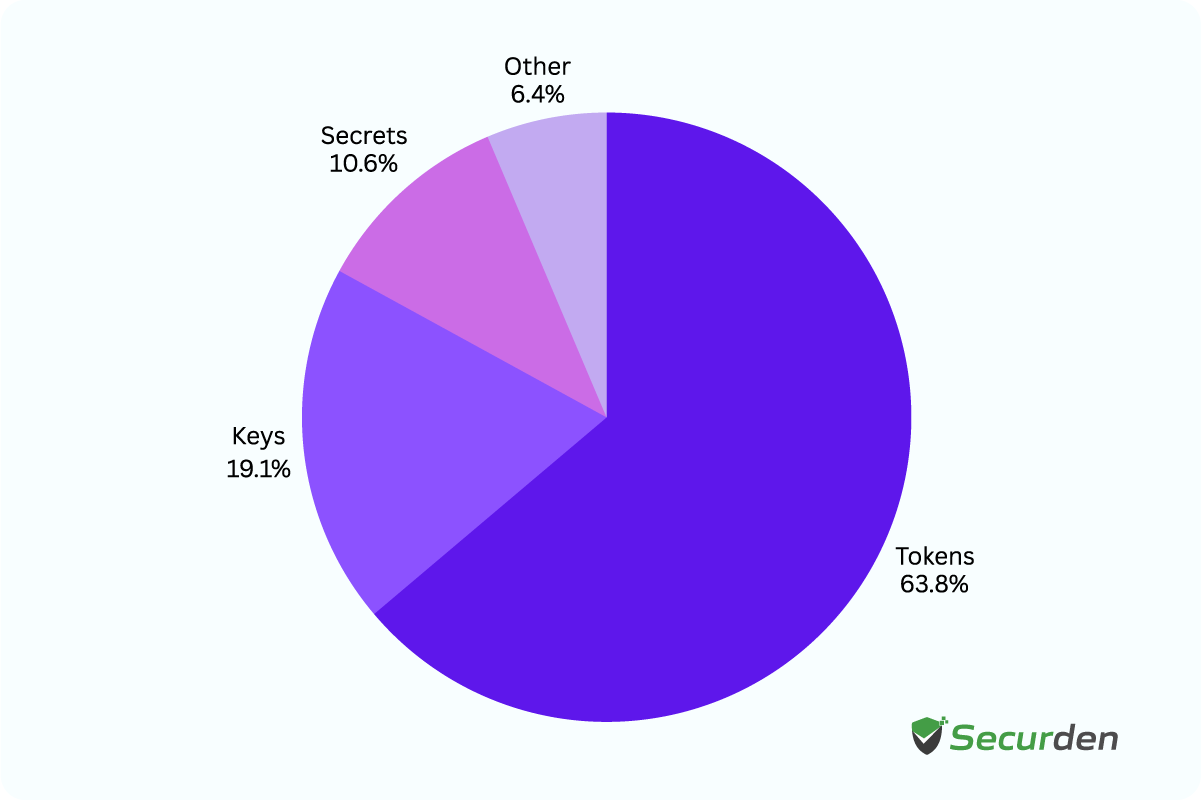
Distribution of NHIs in Code and CI/CD Pipelines
In CI/CD environments, NHIs are generally used to automate data processing and manage critical services. In Kubernetes for example, these NHIs rely on IAM roles, assigned through machine-specific tags and external variables, to retrieve credentials from secret stores. An example of a typical distribution of NHIs is as follows:
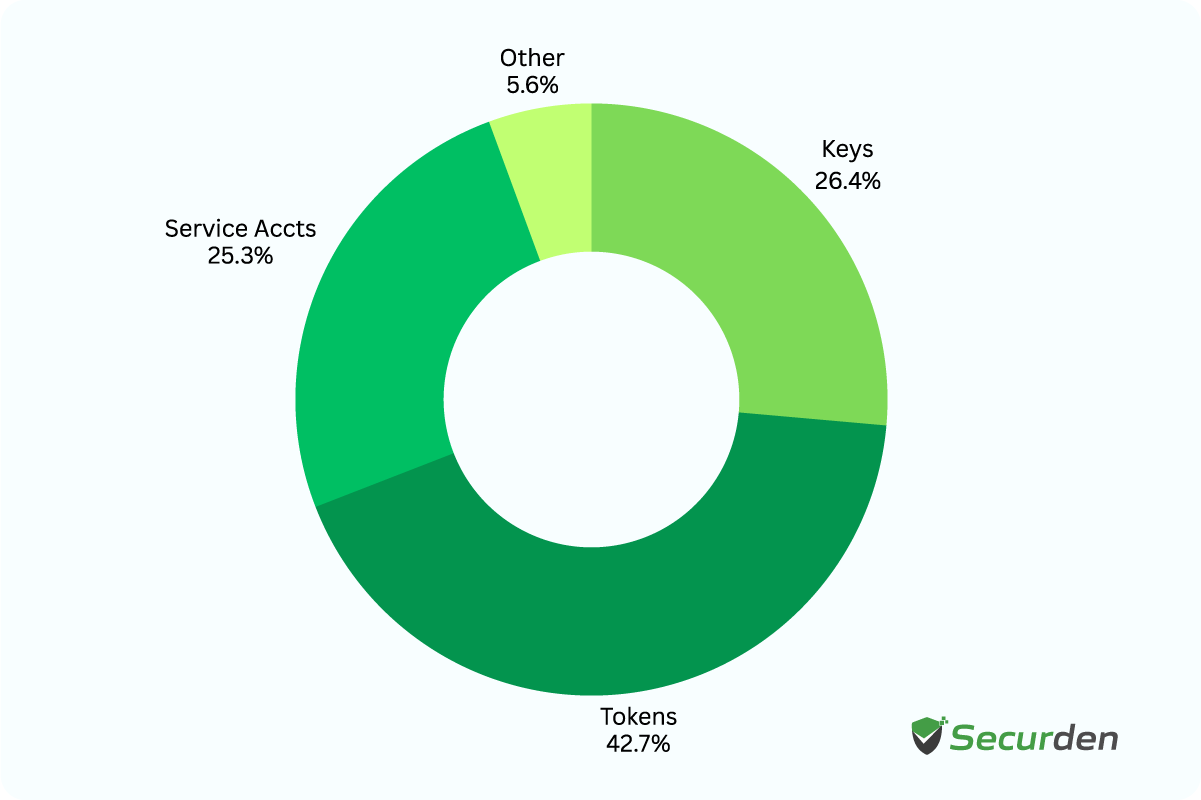
Distribution of NHIs across SaaS Applications
Software applications and APIs are often assigned their own identities to interact with other systems securely. These identities typically use API keys or OAuth tokens for authentication.
What are the challenges in managing non-human identities?
1. Non-human Identity Proliferation
New identities are constantly being created for automation and there is minimal to no governance over them. Engineers and devs also consistently add and create secrets that connect services within the internal infrastructure to enable automated processes. This results in a spill of non-human identities, making it difficult to gain sight of each of them.
The ratio of human identities to machine identities averages from 1:50 to a 1:100 ratio and is only expected to increase with technological advancements in cloud (SaaS) services.
2. Lack of Traceability
With the increasing number of NHIs, companies often lose track of the number of non-human identities being created. This makes it difficult to govern them and creates a new atttack surface – creating gaps for malicious actors to misuse.
If, and rather - when a mishap occurs, it becomes impossible to point out which NHI was responsible for the incident. This lack of transparency and traceability is a huge problem for incident response and forensics operations as they cannot hold anyone accountable or retrace steps to minimize the impact of an attack. They are forced to shut down systems and servers entirely to stop the propagation of damage.
3. Excessive Access Permissions
NHIs, overall, may also have more access permissions than human users. Let's take for example, a service account associated with an application. This service account (an NHI) uses an API key to authenticate into a cloud service like AWS to carry out tasks such as fetching AWS users with the IAM permissions it holds.
The access provisioned to this service account may be more permissive than a human identity as the access is often permanent owing to the continuous and autonomous operating nature of the NHI.
4. Loopholes in AI Threat Detection
Traditional AI anomaly detection tools help stop cyberattacks by analyzing user behavior. Human behavior is predictable to an extent, and a deviation can be derived from simple variables such as a user having an extended access timeframe.
When it comes to non-human identities however, a more advanced approach is required for risk detection. NHI’s are dynamic when compared to their human counterparts, meaning that they might have frequent changes in their access requirements. This creates difficulties in defining the scope of NHI access that AI will leverage to detect anomalies. Additional factors such as - data retrieval outside the set schedule, privileged access beyond NHI responsibilities etc. need to be taken into consideration.
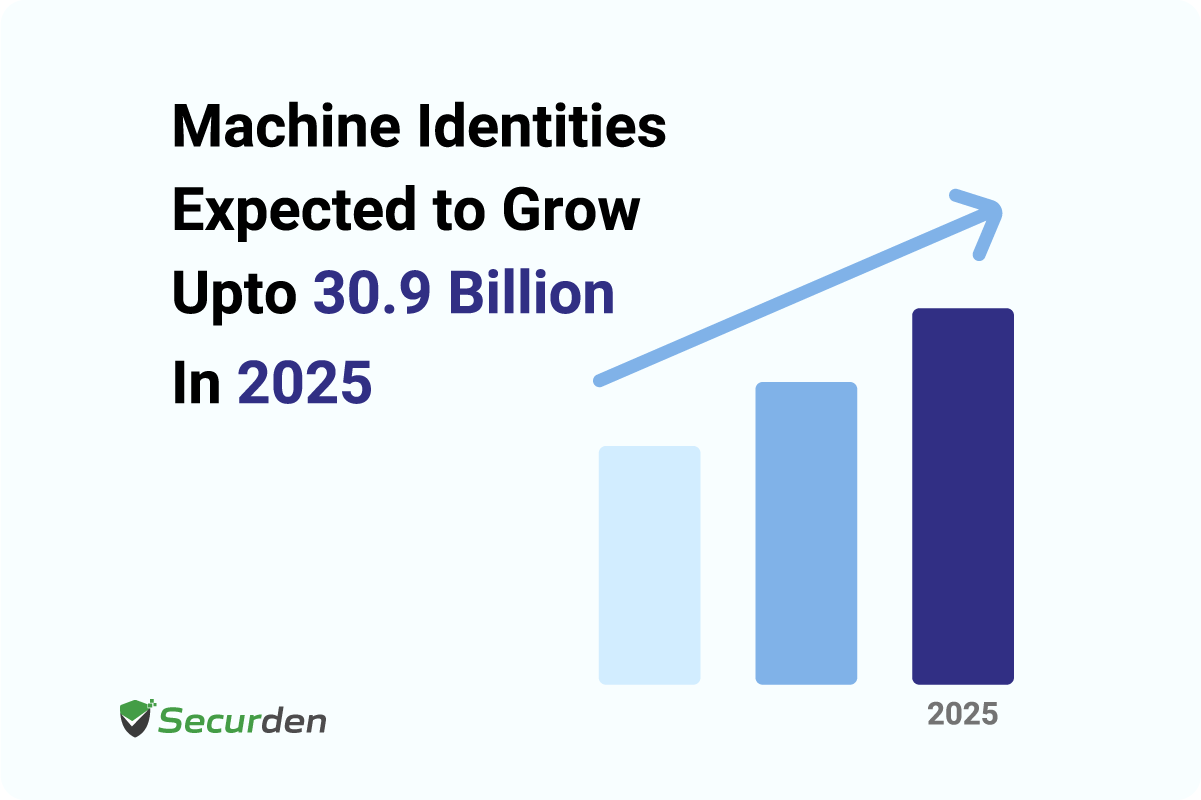
Ultimately, the scale and complexity of these new entities results in an identity explosion and non-human identities may replace humans to be the weakest link in the security chain if they are not handled properly.
What is non-human Identity management (NHIM)?
With the expansion of non-human identities, a strong requirement arises to manage them. With NHI’s constantly interacting with an enterprise’s most critical data and systems, they also need to be properly tracked and secured. Without proper tracking and management, hackers may exploit the large and ungoverned attack surface and utilize permissions that NHIs carry to carry out cyberattacks.
Non-human identity management (NHIM) - A Definition
Non-human identity management (NHIM) involves identifying the number of NHIs within the software ecosystem, the various types of NHIs involved, permissions they carry and then holistically managing them.
The management lifecycle of non-human identities typically involves:
- Gaining visibility through thorough discovery
- Classification and segregation
- Provisioning permissions and assigning an owner
- Safely storing in an encrypted repository
- Scheduling periodic credential rotation
- Constant monitoring, and auditing for compliance
- Decommissioning NHI’s that are no longer in use
What are the types of non-human identities?
The classification of these identities as simply ‘machine’ identities make the approach to handling them very complex. A more intricate, well-defined split up will help with classification to understand security needs and curated management of these identities. This is especially beneficial as each NHI may have a different lifecycle, permissions, and associated attributes.
- Devices - Physical Machines like Mobiles, Laptops, Desktops, Servers, and Virtual Machines (VMs).
- Automation tools and scripts - Code & Algorithms - Some automation tools and scripts will require high levels of privileged access to perform tasks such as performing updates across an entire computer infrastructure.
- DevOps Tools - DevOps tools usually require a greater level of privileged access to carry out tasks. If CI/CD pipelines or other DevOps tools are compromised, they would be able to discover and exploit more privileged credentials.
- Cloud Services (CSP created accounts) - IAM NHIs, containers and Images
- RPA’s - Robotic Process Automation (RPA) uses virtual bots to automate manual, repetitive tasks.
- Applications: Network Applications, Home-built applications, SaaS marketplace applications
- API’s and Microservices
- Application Extensions
- Service Accounts
- IoT Device Accounts
- Routers
Attributes associated with non-human identities
Non-human identity data models often extend beyond traditional Identity and Access Management (IAM) schemas. They often have attributes such as:
- A Distinct Identifier
- Entity Type
- Assigned Owner
- Date of Creation and Expiry
- Associated Permissions and Roles
- Certs and Cryptographic keys
What are the major differences between human and non-human identities?
Breaking down the major differences between ‘carbon’ and ‘non-carbon’ identities helps implement a solid identity management strategy that addresses the complexities in handling them.
A) How they are created: Human identities are generally manually created by a human user – the IT or security team and do not drastically grow. Meanwhile, NHIs are created in multiple ways, across multiple platforms by various users and applications – proliferating quickly with code and cloud adoption.
B) How they are managed: Human users are manually provisioned, and HR systems can be used to manage them. NHIs are sporadically and continuously created by developers and systems to enable automation and are almost never managed properly.
C) How they are tracked: Human users often have accounts tied to them, generally associated with their ‘username’. This makes it easy to track and trace the activities they carry out. Therefore, each human user is held accountable for their actions. Unlike human identities, NHIs are not associated with specific users, thus getting away from scrutiny by regulations and often used by multiple admins or applications.
D) How they are authenticated: Authentication of human identities relies on these three factors to be secure
- Something you know (4 letter PIN, for example)
- Something you are (Biometrics like thumbprints for example)
- Something you have (MFA through a mobile device that a user owns)
NHIs support multiple authentication methods, reflecting technological evolution. Various systems may employ different authentication methods, leading to a wide range of approaches in use.
With NHIs, the only protection is the secret that the user (in most cases a developer) gave to the machine - there is no SSO or MFA in the middle. This means that if attackers get hold of a service account and the secret there isn’t anything else that can stop them.
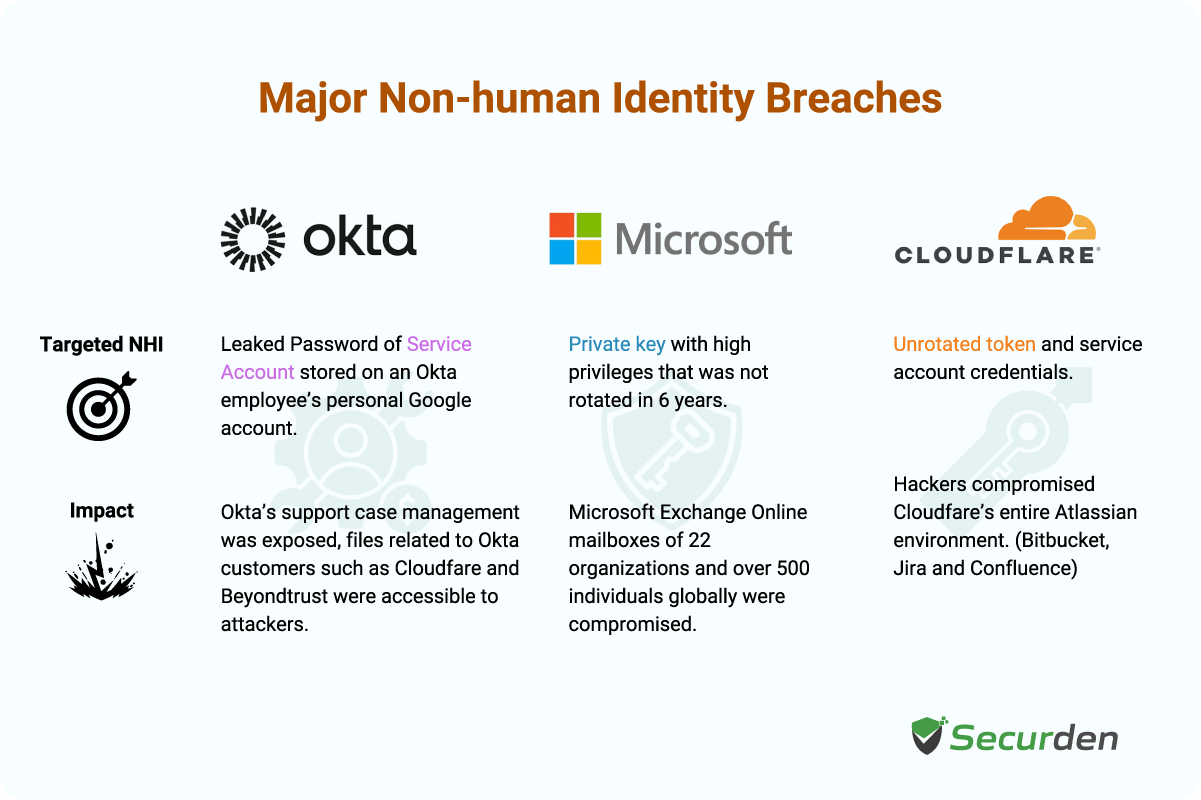
What is the impact of compromised NHIs?
The compromise of a single NHI can precipitate widespread disruptions, which leads to outages for all applications that rely on them. Unlike human accounts, which typically affect access of an individual user, NHIs have inordinate access rights that can incapacitate multiple devices all at once. This amplifies the potential damage and convolutes recovery efforts following a security incident, thereby necessitating heightened security protocols and protective measures for NHIs.
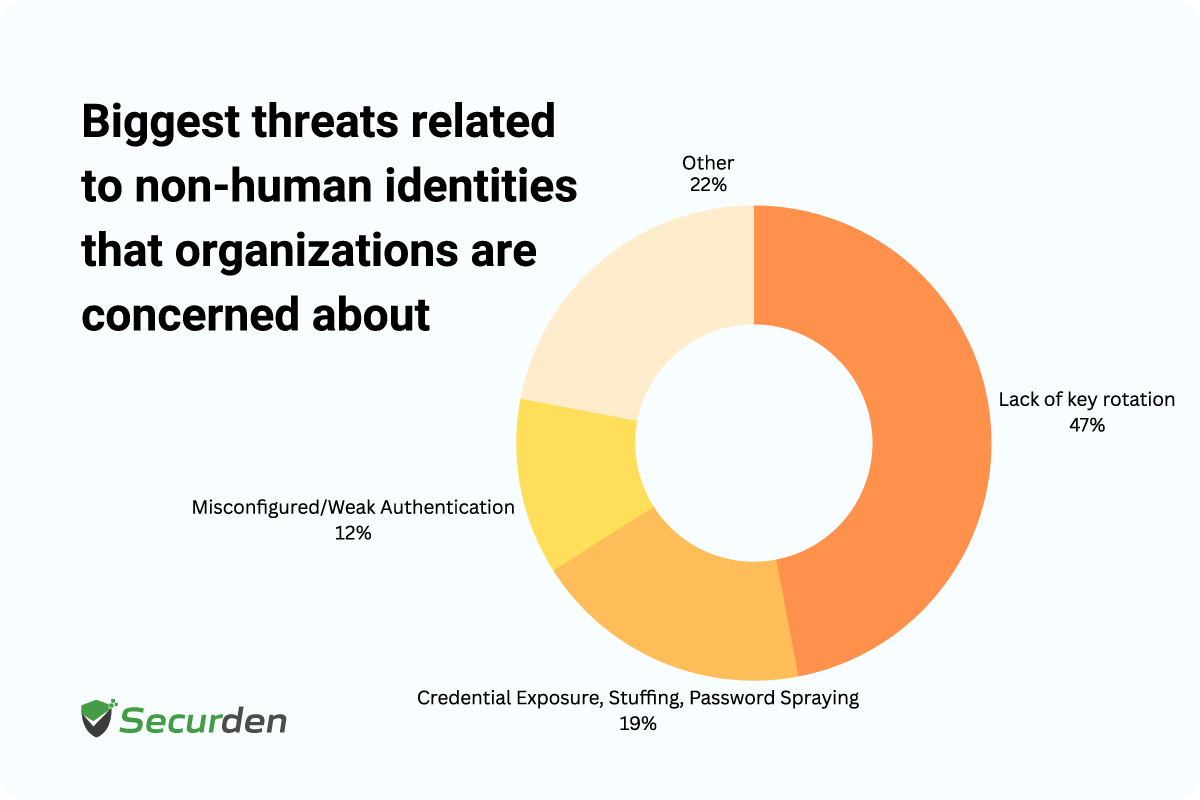
What is the impact of compromised NHIs?
Within IT supply chain, NHI compromise has led to several cyberattacks, including:
Okta Support System Breach (October 2023)
With the help of stolen credentials, Okta’s customer portal was infiltrated and sensitive HAR files uploaded by Okta’s customers were accessed. The HAR files had session tokens and cookies, which the attackers exploited to navigate through privileged sessions of Okta’s customers. Further, attackers took advantage of inactive or dormant accounts, tampered with MFA settings. NHIs like service accounts and tokens were leveraged for massive intrusion.
CloudFlare Breach Linked to Okta Compromise
With help of above discussed service accounts and tokens (NHIs), the attackers gained access to CloudFlare’s internal Atlassian server. With lateral movement, they established persistent access and infiltrated through code repositories and viewed sensitive documentation. One access token and three service account credentials which have not been rotated have been hijacked, revealing the risk of unmonitored or stale NHIs.
What are some best practices for securely managing non-human identities (NHIs)?
While organizations partially understand the risk of NHIs, they have not fully committed to securing them. Protecting these identities begins with staying in line with security best practices. At a high level, NHIs can be secured by following these best practices.
- Manage credentials and secrets securely: Using a secure encrypted vault to protect credentials, secrets, and keys. To prevent hard-coding passwords into applications, utilize APIs to deliver passwords dynamically.
- Enforce the principle of least privilege: Give NHIs the least amount of permissions they need to carry out their tasks. Often, overprivileged service accounts are exploited to hack into organizations. Keep a regular check on privileges assigned to these identities and reduce privileges when required.
- Continuously monitor and audit: Keeping a keen eye on all the activity carried out by NHIs in real-time helps detect any anomalies and mitigate potential risks. Having a detailed audit logs not only helps with compliance but also helps in analyzing security incidents in post-mortem.
- Set up notifications and alert systems: To respond immediately to possible threats, set up notifications for all privileged events related to non-human identities. Integration with your SIEM tools can also help correlate critical activities and generate alerts.
- Use temporary certificates: Utilize ephemeral certificates in place of static credentials for authentication. This mitigates the risk of credential compromise and limits the attack surface for cybercriminals.
- Firewalls and Network Segmentation: For NHIs utilized by internal programs, implementing firewalls and network segmentation can significantly reduce the risk of external attacks. Configuring firewalls to block external access to services that leverage NHIs ensures that only authorized internal traffic is permitted, thereby limiting the attack surface and preventing unauthorized external exploitation.
- Access Control Lists (ACLs) and Security Groups: Defining precise ACLs and security group policies ensures that only authorized IP addresses and networks can access services utilizing NHIs. This practice further confines NHIs to trusted environments, mitigating the likelihood of external threats exploiting these identities.
- Limiting Exposure: By restricting NHIs to internal networks, organizations can significantly reduce their potential attack surfaces, thereby minimizing the likelihood of external threats exploiting these identities. This strategic limitation is crucial for safeguarding NHIs from external adversaries.
- NIST Guidelines: Follow the Digital Identity Guidelines published by NIST: https://pages.nist.gov/800-63-3/sp800-63-3.html
What are steps involved in managing non-human identities?
1) Identifying and gaining visibility over non-human identities
To have an overview of all NHI’s, the primary approach would be to have a secure inventory of all digital identities within the IT infrastructure. This serves as the base layer for understanding the scope of non-human identities and managing them. Regularly scanning for secrets helps with having a bird's eye view over them and detect anomalies.
2) Managing sensitive non-human secrets
To holistically manage NHIs, sensitive secrets need to be handled from the secure inventory. They need to be monitored from creation to expiry and assigned an owner for better accountability and tracking.
3) Applying security and credential best practices
Keeping the security policies consistent across all identities is crucial for enterprise security. Policies must be enforced to frequently rotate credentials, regularly monitor them and de-provision them when no longer in use
What are the benefits of implementing granular access controls for non-human identities?
As businesses begin to manage modern digital ecosystem, enforcing granular access control for non-human identities entails them several advantages, including:
#1 Augmented Security and Reduced Attack Surface
Granular access controls help businesses enforce the least principle of privilege to NHI management. That means, every NHI has access only to the specific resources or assets needed for their continual functioning. Some merits include curtailing unauthorized access, data breaches, and lateral movement in the wake of a cyberattack. By this way, attackers can’t take advantage of over-privileged accounts to access sensitive systems and data.
#2 Improved Compliance and Auditing Capabilities
By strictly defining what NHIs can access and simultaneously monitoring them, organizations can comply to standards like PCI DSS, HIPAA, and GDPR. Granular controls often provide detailed audits that uncover unusual access patterns seamlessly.
#3 Reduced Administrative Overhead
Effective tracking and adjusting permissions with the help of granular access controls reduces manual errors and administrative overhead. Fine-grained policies make it easier to revoke or adjust access as systems change and NHIs are decommissioned.
What are the challenges in implementing granular access controls for non-human identities?
The primary battles of implementing granular access control for non-human identities arise from their massive volume and invisibility. Managing access permissions in complex IT environments is an uphill battle for CISOs and IT admins. Non-human identities largely outnumber human identities and are thereby challenging to be tracked, monitored, and secured. Lack of centralized management and oversight give rise to shadow NHIs. Shadow NHIs are those that exist without proper governance and tracking. These eventually lead to overprovisioning and privilege creep.
Credential management and NHI lifecycle management also pose major challenges. NHIs depend on secrets like APIs and certificates which are often mishandled or hardcoded. This gives rise to credential sprawling and increases attack surface. Furthermore, without automated provisioning, rotation, and deprovisioning, orphaned NHIs can persist for longer times, opening security loopholes/ hidden entry points for attackers.
How does just-in-time (JIT) access help in securing non-human identities?
JIT access secures NHIs by granting access only when required for the specific duration to accomplish a task. This eliminates the risks accompanying standing privileges. JIT access helps in enforcing the principle of least privilege dynamically, in that NHIs get the necessary time-bound permissions. This aspect helps with reducing the potential damage of NHI compromises. When a NHI get compromised, attackers make use of persistent or overprivileged accounts to move laterally or escalate within the IT ecosystem.
In modern cloud and DevOps environments, NHIs like service accounts, automation scripts, and APIs are plentiful. JIT access helps with automated, policy-driven control that scale with dynamic workload and complex architectures.
How do legacy PAM solutions struggle to keep up with NHI management?
| Challenge | Description |
|---|---|
| How Are Legacy PAM Solutions Designed? |
Designed for human-users like IT administrators and employees, and are provisioned centrally through AD/HR systems. |
| What Does NHI Management Demand or How Legacy PAM Falls Short? |
NHIs (service accounts, API tokens, and workload identities) are developed by developers on-demand across digital cloud environments. Lack of centralized source and workflows result in fragmented governance for legacy PAM tools. |
| Scale and Ephemeral Nature of NHIs |
Traditional PAM solutions support only static credential vaulting and periodic reviews. In cloud-native ecosystems, NHIs vastly outnumber human identities. They are short-lived, swiftly created and destroyed as part of DevOps pipelines, containers, or serverless functions. The transient or dynamic nature of NHIs need modern PAM solutions. |
| Lack of Fine-Grained Access in Legacy PAM |
Traditional PAM solutions lack context sensitivity and give rise to over-permissioned NHIs, ultimately increasing attack surface. NHIs require just-in-time authentication and highly context-aware granular access control. |
How Securden Unified PAM can help effectively secure NHIs?
While organizations have fortified human user access with robust security measures, the management and security of non-human access like RPA bots, service accounts, API keys and tokens have not received the same level of scrutiny. NHIM brings a paradigm shift in privileged access management (PAM). While identity has become the new security perimeter, maintaining focus on human identities is no longer enough. Organizations need specialized solutions designed specifically for the unique requirements of non-human entities to address fundamental requirements. Unified PAM helps secure NHIs by:
1) Providing holistic visibility: PAM helps provide visibility into NHIs and service accounts spread across hybrid cloud environments, including AWS, Azure, and Google Cloud.
2) Vaulting and secure NHIs: PAM provides a secure way to store DevOps secrets, keys and certs in an encrypted vault. It also allows developers to leverage APIs to support automation in developer environments.
3) Assessing security: Unified PAM can actively assess the security posture of non-human identities, check for compliance and provide reports.
4) Managing the NHI lifecycle: PAM can track the creation and expiration dates of SSH keys, and certificates, enhancing operational efficiency and security.
What’s In the coming era? Mostly AI-powered NHIs?
AI systems are ingrained in enterprise environments and gave rise to a new set of NHIs called AI-powered identities. Some common examples include machine learning models, chatbots, recommendation engines, and autonomous agents. The notable characteristics of these AI-powered identities include autonomous decision-making and dynamic access permissions. These give rise to implications like expanding attack surface, accountability issues, and auditing complexities. By implementing least privilege access, continuous monitoring, and defined ownership structures, these digital identities can be safeguarded.
