Every tech company guards something valuable. For some, it's a century-old recipe like Coca-Cola's. For others, it's cutting-edge technology or revolutionary processes. Instead of secret recipes, industry leaders protect their unique search algorithms, specialized code libraries, or custom encryption methods that keep data secure. When these secrets are exposed, a company risks losing its competitive edge and its customers' trust.
In cybersecurity, secrets take on a slightly different meaning and role. They refer to digital elements like passwords, tokens, and encryption keys that lock down sensitive information. These digital safeguards protect the very innovations and processes that drive a company forward.
In this blog, we’ll simplify the concept of secrets management. In addition to explaining how you can manage these digital locks effectively, we’ll also break down common challenges and share practical tips to secure your IT assets. Read on to learn how securing secrets can in turn secure your company’s future.
What is a Secret?
A secret is any piece of sensitive information that provides access to critical systems or data, like passwords, encryption keys, API tokens, or digital certificates. These items play a major role in protecting digital assets, and when they are not properly guarded, they become easy targets for unauthorized users.
Secrets can be found in many places. They might be stored in configuration files, kept in environment variables, or sometimes even hardcoded in software. Their scattered nature heightens the risk of exposure, making them prime targets for cyber attackers. A leaked secret can lead to breaches, data loss, and significant financial or reputational harm.
Strong protection starts with secret identification. Teams must spot sensitive data points early, limit their exposure, and control who accesses them. Clear secret classification helps create an effective secrets management system, which will keep your valuable assets safe while allowing legitimate work to continue smoothly.
What is Secrets management?
Secrets management is the process of handling sensitive details safely throughout their entire lifecycle. It involves the storage, control, and distribution of information such as passwords, encryption keys, and tokens.
In practice, secrets management means using dedicated tools or secure storage methods that keep this information out of sight from potential intruders. It includes practices like regularly updating and rotating secrets, setting up access rules, and monitoring usage. By adopting a systematic approach, organizations can reduce the risk of accidental exposure and make it harder for attackers to exploit any weak points.
A strong secrets management process protects sensitive data and also supports overall system integrity by preventing unauthorized access.
5 Key Challenges in Enterprise Secrets Management
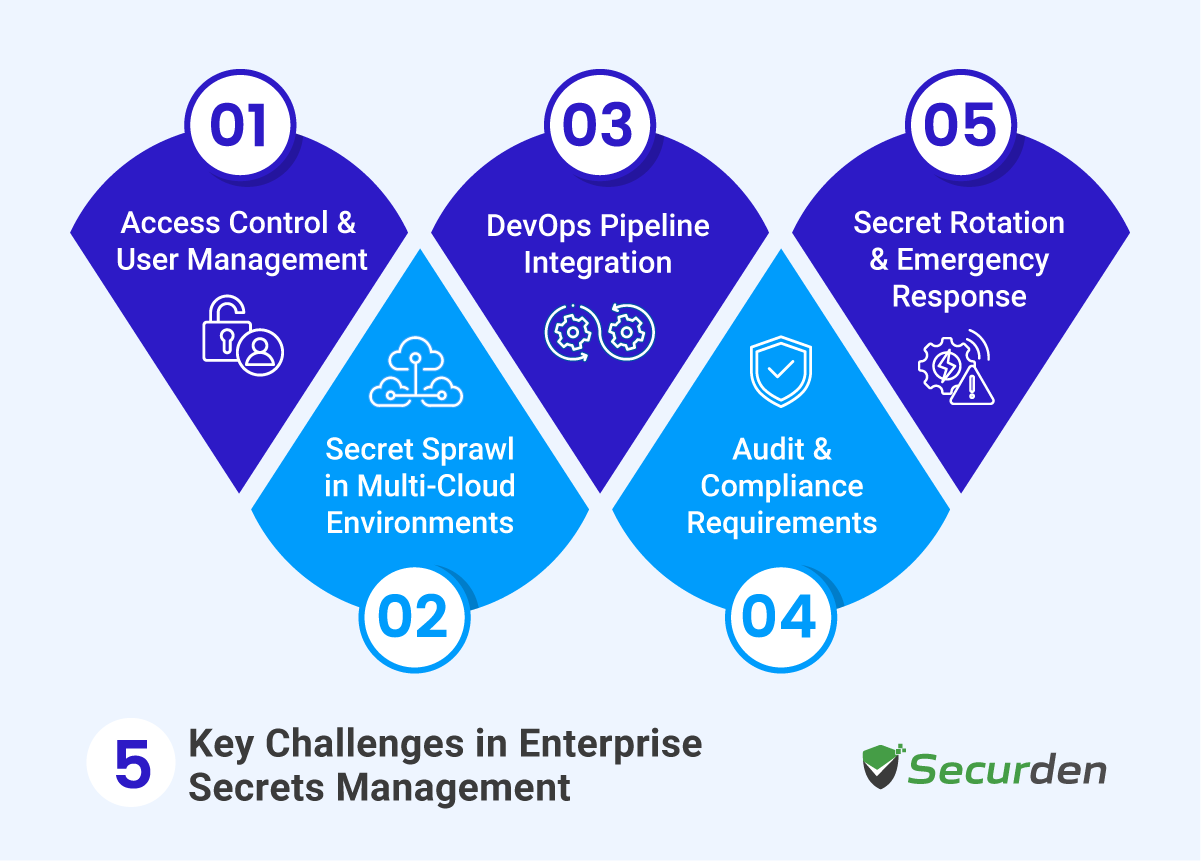
Managing secrets across large organizations brings unique security and operational challenges. Here are the main obstacles companies face when scaling their secrets management:
1. Access Control and User Management
Teams expand, roles change, and permissions need updates. Organizations struggle to track who needs access to which secrets and when that access should expire. For example, when a developer switches projects, their old access rights might linger, creating security gaps. Proper access management means matching secret permissions perfectly with job roles while making updates fast when those roles shift.
2. Secret Sprawl in Multi-Cloud Environments
As companies adopt multiple cloud platforms, secrets multiply across different services. An organization might run workloads on AWS, Azure, and private clouds simultaneously. Each platform brings its own secrets, making it tough to maintain visibility and control. Teams need ways to track and manage secrets across these scattered environments without creating blind spots.
3. DevOps Pipeline Integration
Modern development moves fast, with automated pipelines deploying code many times daily. Building security into these pipelines without slowing them down is tricky. Development teams need instant access to secrets for testing and deployment, but security teams must maintain control. Finding this balance between speed and security often creates friction.
4. Audit and Compliance Requirements
Tracking who accessed which secrets and when becomes complex at scale. When auditors ask for reports, organizations scramble to piece together access logs from different systems. Meeting compliance standards like SOX, HIPAA, or PCI DSS demands detailed secret access records and proof of proper controls - a massive task across distributed systems.
5. Secret Rotation and Emergency Response
Changing secrets regularly helps prevent breaches, but coordinating updates across hundreds of systems is risky. One missed update can break critical services. Plus, when security incidents happen, organizations need ways to quickly revoke and replace compromised secrets without disrupting operations. This demands both careful planning and swift execution capabilities.
With these obstacles laid out, the next step is to turn insights into action. Now, let’s explore best practices that convert these obstacles into strategic advantages for a secure digital environment.
Automate Secret Rotation Without the Risk
Save hours managing credentials across your enterprise. Our password manager handles the complexity while you focus on running your business.
Best Practices for Effective Enterprise Secrets Management
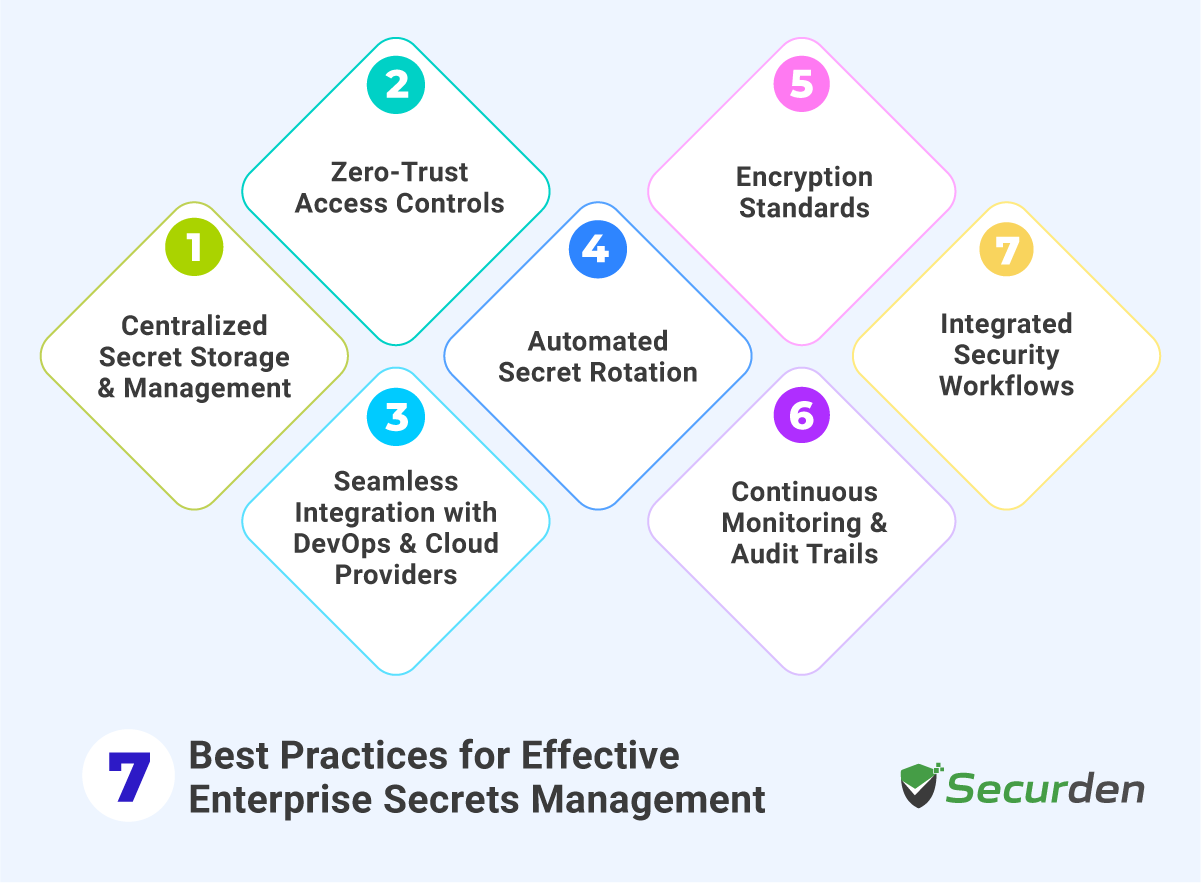
Strong secrets management forms the backbone of enterprise security. Many organizations struggle with manually sharing credentials, hardcoded secrets in applications, and uncontrolled access to sensitive data. Here are seven best practices and strategies that blend security with operational efficiency.
1. Centralized Secret Storage and Management
Organizations need a unified repository for storing and managing secrets. A centralized approach eliminates scattered credentials across various systems and allows strict monitoring of access patterns. Smart secret storage prevents database credentials from being exposed through configuration files or environment variables.
2. Zero-Trust Access Controls
Implementing granular access controls based on roles prevents unauthorized access to protected resources. Organizations should map specific resources to organizational units and enforce strict verification for both human and non-human identities requesting access to sensitive data.
3. Seamless Integration with DevOps and Cloud Providers
Ensure the solution integrates effortlessly with your existing DevOps tools and cloud platforms like AWS Secrets Manager. Such integration supports smooth control access across auto-scale environments while managing non-human identities and privileged access effectively.
4. Automated Secret Rotation
Regular rotation of privileged passwords reduces risks from compromised credentials. Auto-scaling environments demand automated processes for secret creation and updates. Setting up automated rotation cycles for API keys, SSH keys, and private certificates minimizes exposure windows.
5. Encryption Standards
Securing secrets at rest and in transit requires robust encryption. Organizations should encrypt data using industry-standard algorithms and protect encryption keys through hardware security modules. Strong encryption prevents attackers from gaining unauthorized access even if they breach the storage layer.
6. Continuous Monitoring and Audit Trails
Maintaining detailed logs of who accessed what secrets and when helps track potential security issues. Monitoring systems should flag unusual access patterns and integrate with existing security tools for seamless operation across the IT infrastructure.
7. Integrated Security Workflows
Embed secrets management into daily operational and development practices. Integrating these measures with existing processes reduces manual errors and helps maintain a continuous security posture.
Building strong secrets management takes time and dedication. Start small, measure consistently, and scale your approach as your security needs evolve. When done right, it becomes a competitive advantage - keeping your assets secure while helping teams move faster.
Deploy Smart Security for Modern Development
Balance development speed with robust security. Securden’s Enterprise Password Manager integrates with your tools while maintaining strict access controls and comprehensive audit trails.
How to Choose the Right Secrets Management Solution
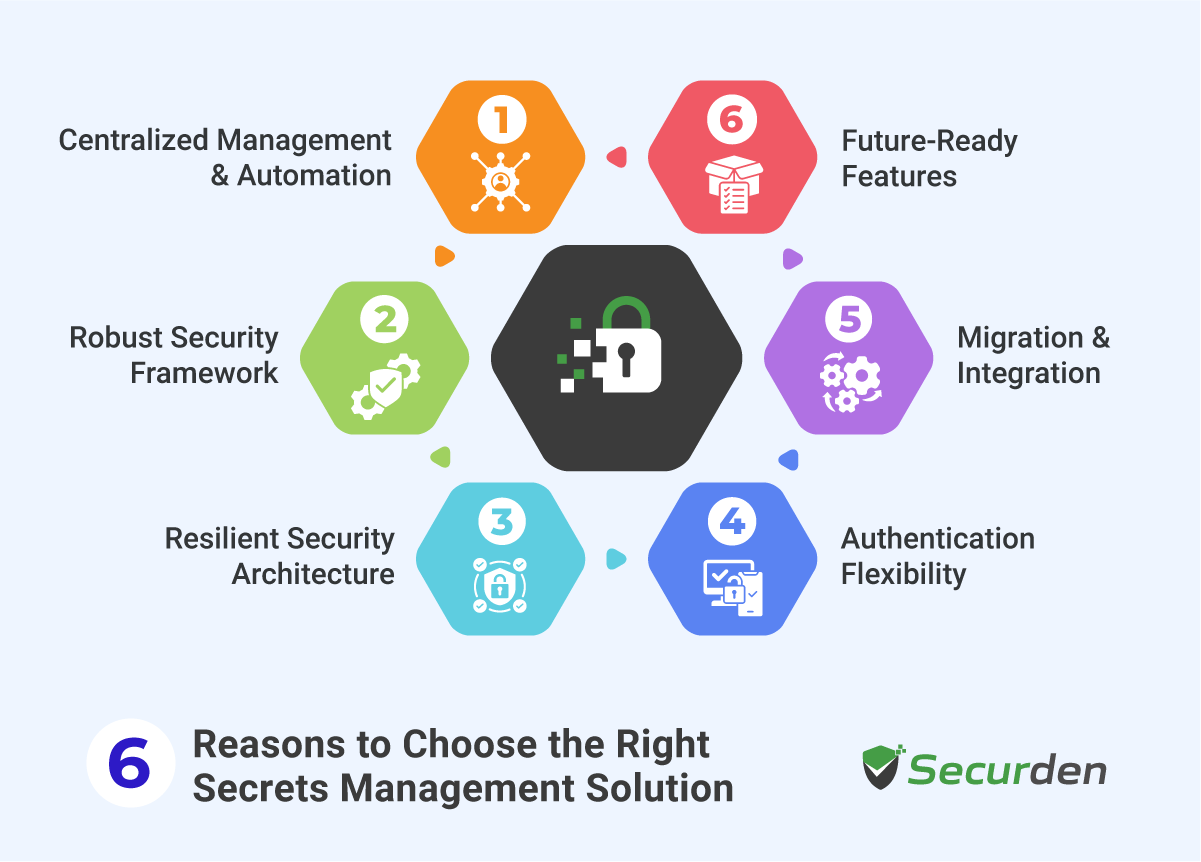
Organizations need reliable tools to manage their growing volume of digital credentials. When evaluating secrets management platforms, several key factors determine long-term success:
1. Centralized Management and Automation
A centralized repository for secrets management is vital, especially in dynamic cloud environments. Look for automation tools that support regular rotation and audit trails, reducing human error and eliminating manual sharing of hard-coded secrets.
2. Robust Security Framework
Opt for a solution that offers a strong security model and strict access controls to mitigate risks from unauthorized access. It guarantees that digital secrets—ranging from API keys to user passwords—are stored securely and monitored continuously.
3. Resilient Security Architecture
Strong encryption forms just one part of the security puzzle. Look for solutions built on zero-knowledge architecture, backed by recognized certifications like SOC2 and ISO 27001. Third-party security validations provide extra confidence in the platform's security claims.
4. Authentication Flexibility
Modern environments need diverse authentication options. Solutions should support various MFA methods - from basic email OTPs to advanced hardware keys. Teams work differently; your platform should adapt to their security preferences.
5. Migration and Integration
Switching platforms causes headaches unless handled properly. Pick solutions offering migration assistance and clear documentation. Check if the platform integrates with your existing IT stack and supports remote access management for various assets.
6. Future-Ready Features
As organizations grow, their needs evolve from basic password management to privileged access management (PAM). Choose platforms that offer clear upgrade paths to advanced features like just-in-time access and session monitoring.
Given these criteria, Securden's Password Vault emerges as the obvious choice. Enterprise Password Vault delivers on these requirements while keeping implementation simple, you must check out. With its free tier supporting up to five users, built-in PAM capabilities, and comprehensive security features, it offers a clear path from basic password management to advanced access control.
Designed for modern enterprises, it combines military-grade security with user-friendly design. With Securden’s Enterprise Password Vault, you can start protecting your secrets within minutes, thanks to its straightforward approach and comprehensive feature set.
Secure Your Credentials with Confidence
Protect API keys, user passwords, and digital certificates under a robust security framework. Experience unmatched security and peace of mind with Securden’s Enterprise Password Vault.
Keep Your Secrets Safe With Securden
Proactive secrets management lays the groundwork for a resilient security framework. Securing sensitive digital secrets can be viewed as the first and most crucial step to safeguarding your foundational IT infrastructure.
Whether dealing with API tokens, encryption keys, or user credentials, maintaining tight control over these assets ensures operational continuity and protects against cyber threats. Incorporating effective privilege access governance further reinforces your security posture by limiting access strictly to authorized users.
But where do you begin?
Our Enterprise Password Vault stands out in this space, earning recognition as an outperformer and market leader in the GigaOm Radar report. Built on zero-knowledge architecture with AES-256 encryption, it offers comprehensive protection while remaining surprisingly simple to use.
Some of its standout features include granular access, automated password rotation, smooth PAM integration paths, and flexible authentication options—from hardware keys to RADIUS systems.
Looking to strengthen your secrets management strategy? Start with Securden's Enterprise Password Vault today. Sign up for a free trial and see how five minutes of setup can transform your security posture. Our team stands ready to guide you through each step of securing your organization's digital keys.
Want To See Enterprise-Grade Secrets Management in Action?
Book a personalized demo of Securden's Enterprise Password Vault and discover why leading organizations trust us with their digital keys.


