Being a chief information security officer, network security manager, or IT manager, if you want to mitigate insider threats, manage complex access permissions, or reduce the risks of excessive access rights, implementing (JIT) just-in-time access becomes essential.
According to a Verizon report, 74% of all breaches involve the human element, with people involved either via Privilege Misuse, use of stolen credentials, Error, or Social Engineering.
Considering the stats from the above reports makes it clear that traditional access controls are no longer enough to protect your information. Just-in-Time JIT access offers a solution by providing temporary and on-demand access to sensitive data only when there is a need.
In this blog, we will explain to you the meaning of just-in-time access, how JIT access works, its benefits, limitations, and best practices. Let’s understand each of the sections in detail.
What is Just-in-Time Access?
Just-in-Time (JIT) access is a core security practice that grants users or systems the minimum level of access to resources or information only when they need it and only for a specific time duration to complete a task. As soon as the task is completed, the access is revoked.
One of the core challenges in traditional access management is the problem of standing privileges, where users or systems have continuous access to sensitive resources. Standing privileges increase the risk of unauthorized access.
As a result, standing privileges lead to privileged account abuse, where attackers exploit these accounts to gain unauthorized access and cause financial or reputational damage to organizations.
By adopting a just-in-time privileged access approach, you can ensure minimal risk of unauthorized access and security breaches. just-in-time privileged access management approach, you can ensure minimal risk of unauthorized access and security breaches. JIT access implementation reduces the time and scope of sensitive and confidential information or systems exposure.
What are the Different Types of Just-in-Time Access?
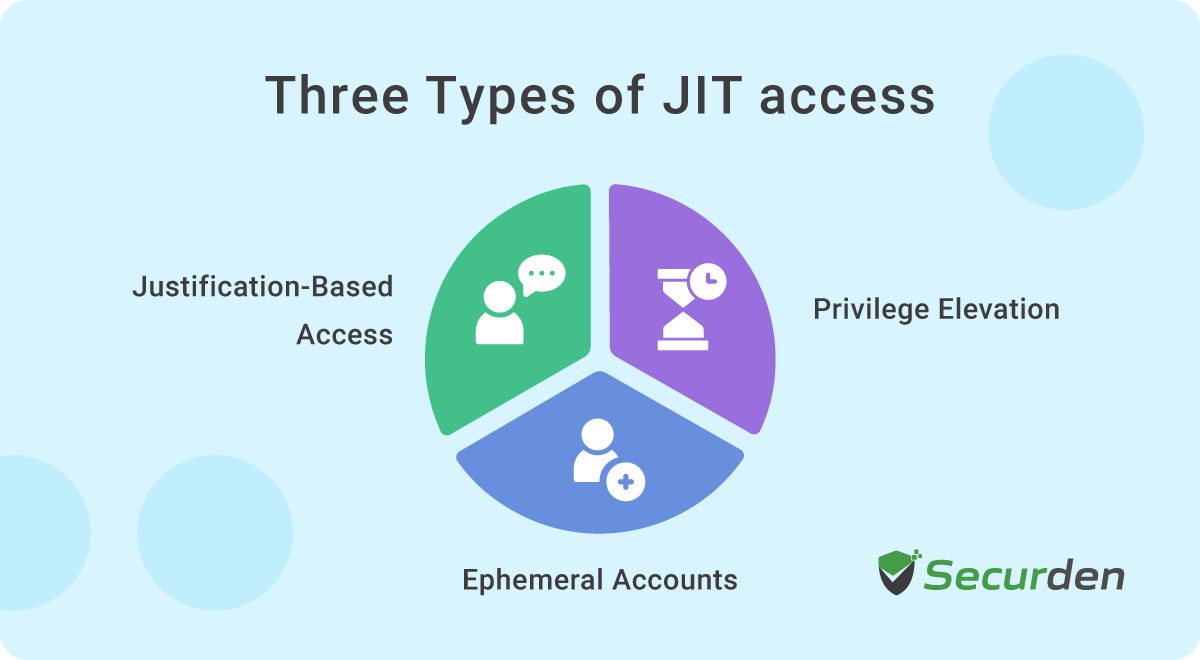
Let’s understand each type of just-in-time access in detail.
1. Justification-based Access
Justification-based access, or broker-and-remove access, requires users to provide a valid reason for accessing specific information from critical systems or resources. This method allows administrators to create policies that require users to provide a valid reason for privileged access and privilege escalation requests as well.
Upon approval, authoritative personnel grant users access for a limited time. The credentials used are managed centrally, typically within a secure vault. While users can access this vault, they need help handling the credentials directly. The credentials are regularly updated and kept hidden from users, which helps to prevent misuse or unauthorized access.
2. Ephemeral Accounts
Ephemeral accounts refer to creating one-time accounts with a short lifespan. Ephemeral accounts only provide access to privileged access systems when needed. Ephemeral accounts are not a JIT access solution but a method to implement just-in-time privileged access within an organization.
Ephemeral accounts help mitigate security risks by allowing users to complete specific tasks without the risk associated with long-term access.
Once the tasks are completed, ephemeral accounts are deleted or de-provisioned. Such an approach is practical when providing limited access to low-level or third-party users without risks associated with long-term access to system work.
3. Temporary Elevation
Elevated access allows users to request a temporary elevation of privilege to perform specific tasks. The administrator or manager can approve the request automatically or manually by specifying how long a user will have elevated access.
As soon as the time expires, the user’s access is revoked to ensure that elevated privileges are unavailable longer than necessary. This is the fundamental element of Just-in-Time privileged access, ensuring that a user doesn’t have prolonged and elevated access to critical systems, reducing the risk of unauthorized or excessive access to critical systems.
Explore Securden’s Unified PAM Solution
You can try Securden's Unified PAM solution for 30 days. Sign up for the cloud version or download the on-premise trial.
Next, let’s understand the process of how JIT access works.
How Does Just-in-Time Access Work?
JIT access includes five different stages; let’s understand them in detail below. Here is the process of how just-in-time privileged access works.
- Request Access: When users request access to perform a specific task or access data, they submit a request via a centralized system, like a PAM software solution. Users must specify the resources they need to access during the request process, including critical servers, network devices, databases, or other sensitive systems. Users also provide details about the purpose of the access and the duration for which it is required.
- Verification and Approval: The request is then approved. Depending on your organization’s policies, it might undergo automated checks or manual approval by a manager. The request's legitimacy ensures it aligns with the user’s role and responsibilities during approval.
- Temporary Access Grant: Once approved, the user accounts get temporary access to the requested resource. During this time, they have “just enough access” to perform the required tasks—nothing less.
- Activity Monitoring: The user’s actions are monitored and logged while having access. These detailed logs provide complete audit-privileged security accounts to help with compliance, unauthorized activity detection, and enabling incident response teams to review activities if necessary.
- Automatic Revocation: After the predefined access period ends, just in time cloud access or on-premise access is automatically revoked to ensure that there are no lingering permissions that can exploit information later. This authorization revocation ensures reducing security risks.
What are the Benefits of Just-in-Time Access?
Here are the 5 key benefits of just-in-time access.
1. Reduces External Threat Attack Surface
JIT access reduces organizational risk by limiting critical systems accessibility to minimize attack exposure on privileged accounts. A report from Verizon showcases that 68% of data breaches occur due to a person falling into a social engineering attack, underscoring the importance of just-in-time privileged access in mitigating this risk.
2. Implements Least Privilege Access
JIT access enforces the principle of least privilege by granting employees only the necessary just-in-time permissions for specific tasks and limited time. Advanced PAM solutions like Securden follow the same approach to help businesses prevent unnecessary permissions and unauthorized access to your business's critical systems.
3. Enhances Security Posture
JIT access helps to strengthen the organization’s security by ensuring that information is controlled, monitored and users have time-bound access. Following this approach allows you to close security gaps and makes it easier to comply with your organization's regulatory requirements.
4. Mitigates Inside Security Risks
Due to insider threats, there is a risk of malicious or accidental misuse of privileged accounts. Implementing JIT access within a solid privileged account management (PAM) framework helps mitigate these threats by restricting both the duration and scope of access, automatically revoking standing access when it is no longer necessary.
5. Reduces Administrative Overhead
The automation process of granting and revoking access via just-in-time privileged access reduces manual efforts and IT overhead. You can cut down on administrative tasks but also reduce the errors associated with manual efforts across the entire PAM lifecycle. This way, you improve your IT department's proficiency, efficiency, and productivity in critical tasks.
How to Implement Just-in-Time Access in Your Organization (10 Best Practices)
Let’s learn about how to implement JIT access within your organization. Follow these steps to get started.
- Define detailed policies that govern JIT access, specifying who can request access, under what circumstances, and the approval process involved.
- Require MFA for all just-in-time privileged access requests to enhance security and reduce the risk of unauthorized access.
- Use automated workflows for access requests and approvals to streamline the process, reduce manual errors, and improve efficiency.
- Conduct a thorough risk assessment to prioritize high-risk areas where JIT access can provide the most security benefits.
- Implement logging mechanisms to track all just-in-time privileged access activities for effective monitoring, compliance, and incident response.
- Provide training and resources to ensure users understand the importance of JIT access and how to request access properly.
- Mandate that users provide clear justifications for their access requests to ensure privileges are granted access only when necessary.
- Use existing security tools or implement, such as Privileged Access Management (PAM) solutions like Securden, to enhance the effectiveness of JIT access implementation.
- Continuously evaluate and update access policies based on changing security threats, compliance requirements, and organizational needs.
- Ensure that users are granted the minimum necessary privileges for the shortest time required to complete their tasks, aligning with the principle of least privilege and zero trust security.
What are the Limitations of Just-in-Time Access?
Let’s learn about the 5 core limitations of JIT access.
1. Operational Delays Due to Access Approval Requirements
JIT access can introduce delays in operations, as users must wait for access approvals before they can proceed with their tasks. In situations where immediate access is needed, delays can impact productivity and efficiency.
2. Complexities in Integration with Legacy and Existing Systems
Enabling JIT access in environments with legacy systems or complex existing infrastructures can be challenging. Integrating JIT mechanisms into older or incompatible systems may require significant customization, which can be time-consuming and costly.
3. Limitations in Coverage for Rapidly Changing Environments
In dynamic environments where systems or software require instant access to perform specific tasks, JIT access might struggle to keep up. Considering such information provides insights that immediate access or instant access to controls would reduce efficiency, productivity, and struggles to access the information.
4. Risks Associated with Misconfiguration and Excessive Permissions
Not providing sufficient access or misconfiguration of JIT access might result in insufficient or excess permissions. If JIT access is not managed correctly, there are chances of unauthorized or create vulnerabilities within your organization.
5. Complexity in Establishing and Managing Access Policies
In large organizations or companies, setting up the JIT access policies could be complex and challenging to achieve tasks, as organizations have diverse roles and responsibilities. This is why ensuring policies should be comprehensive and consistently enforced with constant efforts and careful oversight.
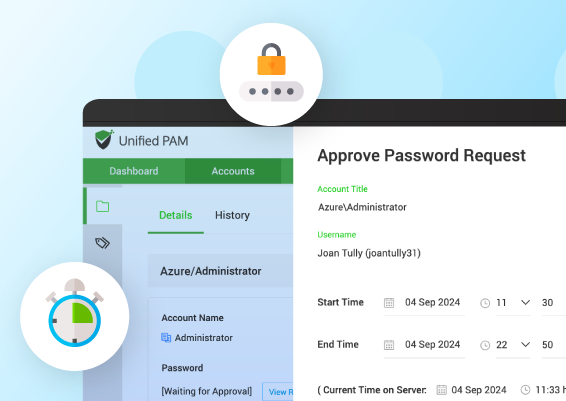
How Securden Facilitates Just-In-Time Access for Your Business
Securden’s Unified Privileged Access Management (PAM) solution offers a just-in-time access solution that improves your organization's security posture. By granting time-limited access based on need, organizations can enforce stronger security measures and minimize attack surfaces.
With Securden, users can request temporary access to critical systems, which undergo automated or manual approval. Once approved, users perform their activities with complete visibility of the session. Access is automatically revoked upon task completion, and the password is rotated according to the organization's policy. This establishes complete visibility and helps thwart unauthorized access.
Key features of Securden’s JIT access
- Grant temporary access to critical systems: Securden allows administrators to grant users limited access to critical systems based on their job roles for a specific time. This approach fulfills users’ business needs without compromising security.
- Automated workflow and access management: Users must get approval from a business authority before accessing critical systems. Access is provided for a limited time, and it is automatically revoked. Passwords are reset.
- Generate one-time or disposable passwords: Users access IT assets with one-time or temporary passwords that change automatically after use.
- On-demand and advance access requests: Users can justify their requirements and request access on-demand or in advance for planned activities.
- Self-service requests: Automated approvals can be set for senior users, bypassing wait times when approvers are unavailable.
- Fully controlled access and session recordings: Admins can monitor and control sessions in real time, terminate suspicious activity, and record sessions for review.
- Trace activities with audit trails: All privileged activities are logged as audit trails, which aid governance and compliance by detailing access, actions, and approvals with searchable filters.
By integrating Securden’s JIT access as a key component of your PAM implementation, you can reduce the attack surface, mitigate insider threats, and guarantee that access to critical systems remains tightly controlled and time-bound.
Secure Organizational Access with Securden
Start your 30-day free trial of Unified privileged access management. Choose cloud or on-premise and manage access securely.
Industry-Specific Applications of Just-in-Time Access
Let’s now learn about the application of JIT access in the different industries.
| Sector | JIT Access Importance | Specific Applications |
|---|---|---|
| Healthcare | Protects sensitive patient data and ensures compliance with regulations like HIPAA. | Medical professionals only get short-time access to electronic health records during a patient’s treatment. |
| Financial Services | Secures customer data and prevents fraud in financial institutions. | Employees only get limited-time access to financial systems or transaction records when performing specific tasks. |
| Government and Defense | Controls access to classified information, preventing data leaks and unauthorized access. | Personnel are granted access only when needed for specific missions or projects. |
| Manufacturing | Secures production environments during maintenance or operational changes. | Limits access to critical systems like SCADA, reducing the risk of sabotage or accidental disruptions. |
| Energy and Utilities | Protects critical infrastructure by controlling access to control systems. | Engineers and operations staff can only access specific operations or emergencies when necessary. |
| Technology and IT Services | Minimizes the risk of unauthorized changes or data breaches in software development and IT operations. | Developers and IT staff are granted temporary access to production environments or customer data only when necessary. |
Concluding Notes on Just-in-Time (JIT) Access
In this blog, you have learned that just-in-time access is a powerful tool in IT security. It helps secure permissions and access to critical business information or systems. While JIT access has limitations like complexity in managing access, misconfiguration with permissions, and operations delays, best practices can help you resolve the challenges in standing privileges access.
Securden is a leading privileged access management solution provider in the USA. We offer multiple IT security solutions, such as UPAM, Enterprise Password Manager, Endpoint Privilege Manager, and PAM for MSPs.Download the trial of our PAM solution to get started today only.
Frequently Asked Questions on Just-in-Time Access
1. How does the JIT access model contribute to a zero-trust security model?
The just-in-time access model is a core component of the zero-trust security model. This approach allows temporary access to limit access to privileged accounts only when required. It aligns with the zero-trust principle of “never trust, always verify.”
This model reduces the attack surface and the risk of lateral movement by attackers who have compromised an end-user account. By implementing just-in-time access, you apply the zero-trust “use least privilege access” principle by providing users with “just enough access” for a particular duration to perform a task.
2. What are the advantages of using JIT access in a PAM software solution?
Here are the core advantages of using just-in-time access in a PAM solution.
- Improved security: Limits privileged access to reduce the risk of exploitation by malicious actors.
- Reduced insider threats: Restricts access to sensitive data, ensuring it's only available for a specific time.
- Streamlined audits: This feature facilitates easier monitoring and auditing of access events, tracking when, why, and by whom access was granted.
- Operational efficiency: Automates access management to reduce IT workload and align permissions with current needs.
3. How does JIT access improve the cybersecurity of an organization compared to traditional approaches?
The traditional approach to privileged access often includes standing privileges where users get broad, long-term access to systems and data. This model increases the attack surface and the potential for misuse of sensitive information.
However, just-in-time access offers dynamic access with just enough privileges for the time required, reducing the exposure window. By continuously verifying access requests and applying the principle of least privilege, just-in-time access aligns with the zero-trust philosophy of “never trust, always verify.”
4. Is it possible to integrate JIT access into existing PAM solutions?
Yes, PAM solutions like Securden, CyberArk, BeyondTrust, and Delinea offer just-in-time (JIT) access as part of their capabilities. These solutions provide APIs and integration points to implement just-in-time access policies and controls. By using just-in-time access within a PAM solution, as an organization, you can enhance security posture without the need for a complete overhaul of the existing infrastructure.
5. What is the average duration to implement JIT access within your organization?
On average, a phased implementation of JIT access within a PAM solution can be done within 3 to 6 months. However, the actual duration of implementation of JIT access within an organization varies depending on factors.
- The complexity of existing infrastructure
- The number of privileged accounts and systems
- The scope of the deployment
6. What is the return on investments of implementing JIT access?
The ROI of implementing JIT access includes improved security, reduced risk of data breaches, lower compliance costs, and increased operational efficiency. Studies show that the price of a single data breach is 4.88 million.
Such a significant number shows that organizations must adopt and implement a Zero-Trust security policy. By reducing the risks of data breaches and privileged account misuse, JIT helps organizations to avoid the costly consequences of security incidents.
7. How does Just-in-Time access enhance security for organizations using cloud services?
Here are the reasons why JIT access implementation helps to enhance the security of cloud environments.
- Dynamic access controls: Providing context-aware access controls to cloud resources based on user identity, device, and risk factors.
- Reduce digital attack surface: Limiting standing privileges and access to cloud services, infrastructure, codes, and applications to reduce data breaches.
- Just-in-time privileges: Enable the elevation of privileges for specific cloud-based tasks just in time, which reduces the risk of privilege abuse.
- Visibility and control: Improve visibility and control access to privileged accounts activities in the cloud through centralized logging and reporting.




















![What is Cloud PAM? [Definition, Features, Benefits, and Factors to Choose the Right One]](/images/cloud-pam/cloud-pam-blog-image.webp)