Cluttered management of client passwords invites cyberattacks
MSPs deal with several clients across multi-tenant networks to manage their IT and network infrastructure. They constantly need to access servers, databases, network devices and other IT resources. Access to these systems requires login credentials that MSPs need to protect and keep client information secure.
The amount of sensitive customer credentials (including passwords, SSH keys, API keys, Shared TOTPs etc.) to be managed is exponentially larger than a standard organization. Without centralized management, the multitude of passwords that need to be managed results in uncontrolled distribution. Passwords are often stored and managed separately by different teams and maintained using different tools. Ultimately this leads to poor, de-centralized password management.
MSPs need to secure passwords, ensuring that external attackers/malicious insiders don’t get unauthorized access to client systems. Any breach occurring on the MSP side holds them accountable for the leak of client data, resulting in heavy monetary fines and complicated lawsuits.
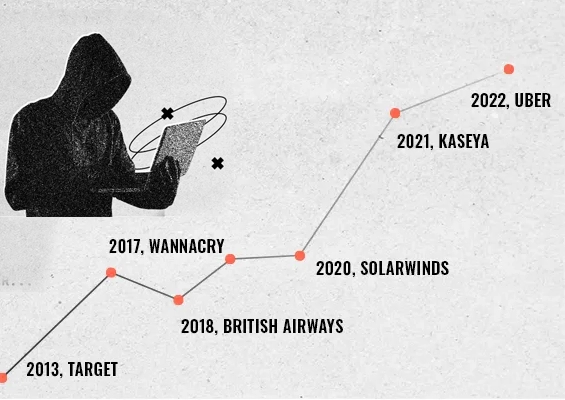
With attackers targeting MSPs for their “breach one, breach all” advantage, managed service providers must work hard to avert weak client password management practices.
Some common flaws observed in the password management practices adopted by managed IT service providers are:
-
Password Reuse by MSP Technicians
MSP technicians frequently need to deal with client passwords to connect to remote systems, assist with IT helpdesk tickets, or carry out technical fixes. And quite often, MSP technicians work with passwords of more than one client at a given time. With multiple customers in play, it becomes difficult to remember several passwords and maintain complexity on all of them. To keep this process uncomplicated, technicians end up using the same strong password for all client accounts/devices. Repeated usage of the same credential increases the susceptibility of cyberattacks, as a successful breach of one client system will lead to the compromise of all others.
Unsafe Password Storage Practices
Commonly adopted password storage methods such as writing them down on a notepad, storing it online apps like excel sheet without encryption etc. are inadequate as they can be easily exploited. Passwords stored in plaintext can be easily viewed, and those stored on notepads or scripts can be misused by anyone who has access to the storage location. Excel is not meant to be used as a password manager, even if it is password protected, excel does not encrypt the passwords within. Unencrypted storage increases the chances of compromise by both malicious insiders and external attackers.
Insecure Sharing of Client Admin Accounts
To enable technicians to access client systems, MSP administrators often set up an admin account on the client domain and share its login credentials and MFA tokens among multiple users. The usage of these credentials lacks monitoring since they are shared across several users and teams. Any mishaps in the sharing and handling of these credentials may result in unauthorized access of client systems and ultimately trigger data breaches.
Bad actors take advantage of the flaws in client password management practices to launch different types of attacks:
Credential Stuffing - Using stolen credentials from one breach to gain access to additional accounts using the same credentials to expand their access within the client network. The attack uses bots for automation and is based on the assumption that many users reuse usernames and passwords across multiple services.
Brute Force Attack - Where attackers repeatedly try several combinations in a trial-and-error method to guess a single password until they hit the jackpot.
To prevent these attacks from being successful, each client password should be unique, complex, periodically rotated, and constantly checked for compromise to improve security and preserve client information.
How can MSPs centralize and streamline client password management?
To streamline management of client passwords and prevent password attacks, certain best practices need to be followed:
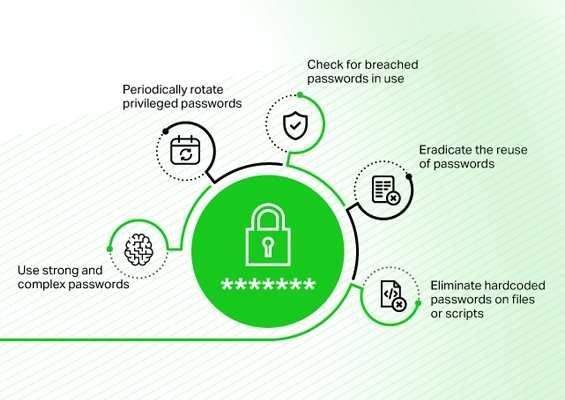
Best Practice #1:Bring all client passwords under the same umbrella – Gather all the client passwords stored in random places (i.e., text files, sticky notes, spreadsheets) and store them in a centralized repository. This practice securely organizes credentials and helps MSP administrators manage access to sensitive information from a single place with appropriate access control mechanisms. It also helps reduce the risk of forgotten passwords and encrypting the password repository boosts overall security.
Best Practice #2:Periodically rotate all passwords – Passwords should be updated/changed regularly to mitigate the risk of unauthorized access, making it difficult for attackers to utilize compromise stolen or leaked credentials. To improve security, make each password strong and unique, using a combination of letters, numbers, and special characters. Implementing frequent password rotation reduces the chance of password reuse while also protecting sensitive information from threats.
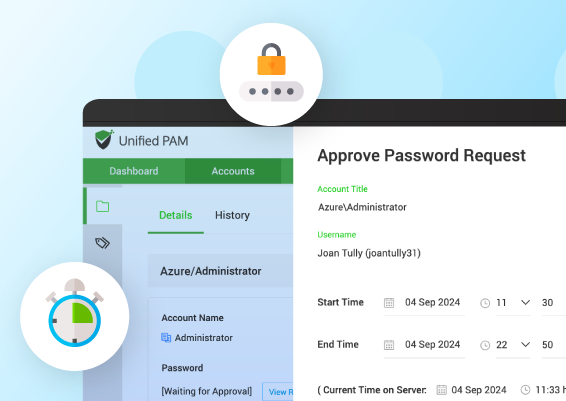
Best Practice #3:Share passwords securely and audit all access – While sharing passwords with technicians, provide access to the passwords with appropriate access control based on their job roles and responsibilities. For example, an MSP administrator can grant full password access to their expert T3 technicians and time-limited, restricted password access to their T1/T2 support technicians. This granular access provides just enough privileges for technicians for the appropriate amount of time averting the risk of unauthorized access.
Best Practice #4:Avoid sharing passwords via insecure channels – Sharing passwords in plain text via channels like email, chat or shared excel sheets should be avoided. Moreover, all password activities like addition, deletion, rotation etc. should be completely captured and recorded as tamper-proof audit trails. This helps establish complete visibility and accountability and comes in handy during security and forensic audits.
Enforcing these best practices requires consistent, rigorous effort by MSP administrators. MSP password managers alleviate the time-consuming labor required to securely manage client credentials and help automate the entire process.
How Securden Password Vault Helps MSPs Enforce Password Security Best Practices
Securden Password Vault is a password management solution that helps MSPs centrally manage client passwords, provision time-limited access to credentials and securely share client admin accounts within the MSP environment.
- Securely Store Client Passwords with Complete Data Segregation – Securden Password Vault provides a folder hierarchy that helps MSP administrators completely isolate passwords belonging to various client organizations. By grouping different client passwords into different folders, and providing the right level of control to technicians accessing the passwords, MSP administrators can prevent password sprawl and achieve centralized visibility and control.
- Enforce Multi-factor Authentication to Sensitive Client Accounts – Securden helps MSPs enforce multi-factor authentication for client password access by integrating with a wide range of MFA solutions such as Mail OTP, Google/Microsoft/TOTP Authenticator, RADIUS Authentication, Email to SMS Gateway, Duo Security, YubiKey and more.
- Automate Periodic Rotation of Passwords – Through automated password rotation and randomization, Securden improves security by lowering the likelihood of unauthorized access and increasing adherence to security standards by ensuring that credentials are changed at regular intervals with complex, unpredictable passwords. This greatly reduces the security threats posed by identity theft.
- Achieve Granular Access Control – Securden helps establish account ownership and enforce granular access control. MSP administrators can make sure that technicians only have access to data associated with the clients they manage. Securden also provides another layer of restriction by facilitating one-click remote connections with servers, databases, devices, and applications on client systems (RDP, SSH, and SQL connections) without revealing the underlying passwords to the technicians.
- Help Clients Demonstrate Regulatory Compliance – With good password policies and practices in place, MSPs can help their clients demonstrate compliance with various industrial and government regulations. Furthermore, it’s necessary for MSPs themselves to adhere to various compliance mandates depending on the customer base they cater to. For example, MSPs managing healthcare organizations must also be HIPAA compliant. Securden Password Vault for Enterprises can help clients with compliance by providing comprehensive reports on which technicians accessed what client passwords and what actions they took with them.
- Versatile Solution for all MSP Operating Models – Securden Password Vault provides complete operational flexibility and caters to all types of MSP IT models including fully managed, co-managed, and hybrid set ups. It offers provisions to securely share passwords with client end-users and IT personnel in multi-tenant networks. Clients can be granted granular control over the accounts and passwords belonging to their organization. Customization capabilities allow defining separate password rules and policies to cater to individual customer requirements.
If you are a managed service provider (MSP) or a managed security service provider (MSSP) looking to automate and orchestrate client password management, feel free to take a look at Securden Password Vault for MSPs.
If you wish to learn more, you can schedule a free technical consultation/demo with our product experts.










![What is Cloud PAM? [Definition, Features, Benefits, and Factors to Choose the Right One]](/images/cloud-pam/cloud-pam-blog-image.webp)