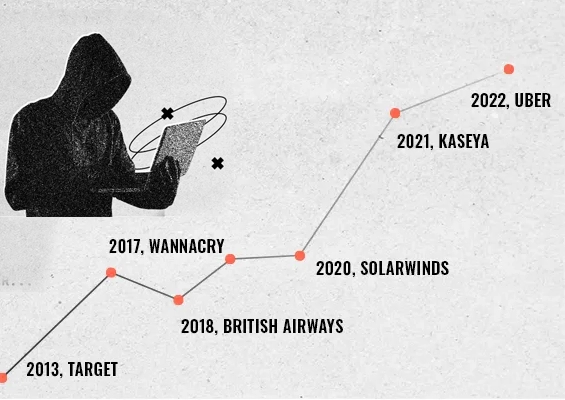
Cybercrime inflicted massive financial damage in 2023, costing companies an estimated $8 trillion worldwide. Forecasts from a U.S. agency suggest this figure may triple to $24 trillion by 2027. This surge in cybercrime reflects the vulnerabilities in modern networks—complex ecosystems of cloud platforms, IoT devices, and privileged accounts that grow with every new connection. To counter these threats, businesses are turning to Privileged Access Management (PAM), a solution that helps them establish control, minimize risks, and protect against an expanding array of cyber threats.
But to reap all those benefits, you need a successful and effective PAM implementation. That’s where things get complicated. PAM implementation isn’t a one-size-fits-all process, and many find it challenging to design, integrate, and manage a solution that fits their unique environment. This guide lays out what every business needs to know, breaking down the essentials of PAM implementation into practical, clear steps.
What is Privileged Access Management (PAM)?
Privileged Access Management (PAM) is a cybersecurity approach that keeps an organization’s sensitive data secure by controlling elevated (“privileged”) access and permissions for identities, users, accounts, processes, and systems across an IT environment.
You can think of PAM as a system of digital checkpoints, controlling who can access what information, when, and under what circumstances. Users with privileged access can access resources, information, or data unavailable to standard users.
PAM frameworks use a combination of advanced tools and policies to manage, monitor, and restrict access to accounts that could, if misused, give hackers or insiders the power to manipulate, steal, or destroy crucial sensitive data.
Why Does Your Business Need Privileged Access Management (PAM)?
Since businesses increasingly adopt various platforms—from cloud services and machine-to-machine accounts to DevOps processes and IoT devices—the attack surface related to privileged access is rapidly expanding. Attackers recognize this trend and often target privileged accounts, as they provide direct access to an organization’s essential assets.
Here’s how implementing a PAM solution can help secure your organization:
- Limit Attack Surface: Control access to critical systems, significantly reducing your organization’s exposure to cyber threats.
- Protect Critical Assets: Secure privileged accounts to prevent unauthorized access, safeguarding sensitive company data from potential breaches.
- Enforce Least Privilege: Implement strict access limits using role-based access control, ensuring users access only the resources necessary for their roles which improves overall security.
- Monitor Privileged Activity: Track and log activities to gain visibility into privileged actions, making it easier to detect and respond to suspicious behavior promptly.
- Reduce Insider Threats: Effectively controlling and monitoring privileged users can mitigate risks associated with internal misuse and foster a more secure environment.
Once implemented, PAM safeguards your business against unauthorized access and lays the groundwork for a robust cybersecurity framework that adapts to modern digital risks.
Get Started with PAM Implementation
Join organizations that have successfully implemented PAM. Connect with our team for a personalized demo today.
5 Prerequisites to Keep in Mind Before You Implement PAM
Here are five prerequisites, or a few foundational steps, if you will, which you should keep in mind before you head off on your PAM implementation journey.
1. Review Existing Access Management Policies
Start by reviewing your existing access management policies. Are they effectively controlling privileged account access? Identify any gaps that could expose your organization to security risks.
A thorough assessment will help you understand how privileged credentials are managed and whether your current controls align with the principle of least privilege.
2. Check Your Infrastructure Readiness
Your IT environment must be ready to support a PAM solution. Organizations should verify that their IT environment can support critical PAM functions, such as multi-factor authentication, privileged session management, and monitoring privileged account activity.
Aligning on-premise or cloud PAM with the organization’s incident response plan, disaster recovery plan, and data protection goals reinforces its effectiveness against security breaches and minimizes security risks.
3. Ensure Stakeholder Alignment
Aligning IT, compliance, security, and business stakeholders is essential for a smooth PAM implementation. When all key stakeholders understand privileged access management's goals, benefits, and requirements, it promotes the seamless integration of privileged accounts across departments.
Each stakeholder’s commitment improves the organization’s security posture, particularly in controlling privileged access, user, and service accounts.
4. Implementation Team Readiness
Assemble a skilled team to lead your PAM implementation. With expertise in PAM and cybersecurity, this team will manage privileged account activity, secure privileged credentials, and apply ongoing visibility over critical systems.
Defining roles like PAM system administrator, asset owner, compliance officer, and training coordinator helps your team handle privileged access issues effectively, address user behavior, and maintain consistent monitoring permissions to secure access across the organization.
5. Foster a Culture of Security Awareness
Training staff on the importance of PAM is vital. Employees should understand how to manage privileged passwords, monitor permission changes, and recognize the implications of compromised user accounts. Regular training sessions can help foster a culture of security awareness, ensuring that everyone understands their role in protecting sensitive information.
Establishing these prerequisites helps tighten control over privileged access and reduces the attack surface across cloud environments, hybrid networks, and local infrastructures.
For a comprehensive understanding of the prerequisites needed for implementing PAM, including detailed infrastructural requirements, refer to Securden's PAM Implementation Guide.
With these prerequisites checked out, you're now ready to dive into the details of PAM implementation.
Your 10-Step Blueprint for PAM Implementation
Step 1: Define and Classify Privileged Accounts
Identify and categorize all privileged access accounts, such as user accounts, service accounts, and admin access. Performing this classification helps establish distinct security measures for each account type, ensuring optimal control and protection.
Step 2: Discover and Inventory Privileged Accounts
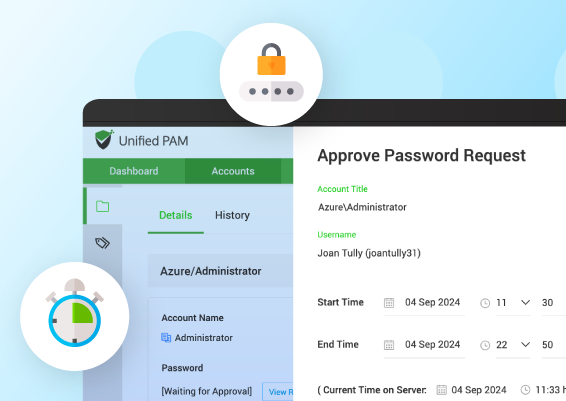
Conduct a thorough scan of your network to uncover all privileged accounts, including those in hybrid and cloud environments. This discovery step reduces privileged account sprawl (unnecessary accumulation of access privileges) and keeps your privileged access landscape visible. With Securden’s Unified PAM automated discovery, you can simplify this process, ensuring no account is overlooked and enhancing overall visibility into your privileged account landscape.
Step 3: Establish Secure Access Controls
Define strict access controls to regulate how privileged accounts gain access to critical systems. Securden’s privileged access management tools like Just-in-Time access or JIT access can help you enforce policies such as least privilege to limit unnecessary elevated privileges.
Step 4: Manage and Protect Privileged Credentials
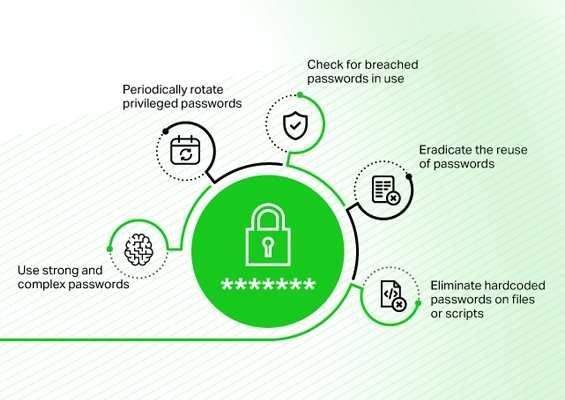
Safeguard and rotate privileged passwords with Securden’s password management tool to prevent unauthorized access. Regular updates to privileged credentials maintain security and minimize exposure to potential data breaches.
Step 5: Monitor and Record Privileged Sessions
Continuously monitor all activities associated with privileged accounts. Recording sessions aid in auditing and provide a clear trail for forensic analysis should any suspicious activity arise. Securden’s session management features allow continuous visibility, helping to monitor access and manage privileged account activity for added security.
Step 6: Detect Abnormal Usage and Respond to Security Incidents
Establish baseline behavior for privileged account usage to identify anomalies. Following this, you can set up automated alerts for unusual behavior across privileged accounts. Develop a clear incident response plan tailored to privileged access scenarios. Swift response protocols for privileged access incidents reduce risks and enhance your organization’s security posture.
Step 7: Audit and Analyze Privileged Account Activity
Regularly review privileged account activities to identify trends and potential risks. Advanced auditing capabilities from Securden’s Unified PAM can simplify this process, making it easier to ensure compliance with security policies.
Step 8: Establish Workflow Approvals for Access Requests
Implement a structured workflow for granting access to privileged accounts, requiring approvals from relevant stakeholders. Performing this step helps ensure that access is granted only when necessary and justified. To top it off, you can automate your workflows with the help of solutions like Securden’s Unified PAM, which takes a huge chunk of load off your hands.
Step 9: Integrate with Existing Security Solutions
Ensure that your PAM solution works in harmony with current security infrastructure, such as SIEM systems. Integrating your PAM solution with your existing solutions provides a comprehensive view of privileged access across your organization.
Keeping this in mind, Securden’s Unified Privileged Access Management seamlessly integrates with popular SIEM tools like Splunk, ArcSight, and others, ensuring a comprehensive view of privileged access across your organization.
Step 10: Continuously Improve and Adapt
Regularly assess and refine your PAM policies based on audit findings and emerging threats. Staying proactive ensures that your security measures remain effective over time, adapting to new challenges as they arise while maintaining compliance with industry regulations.
Follow these steps to implement a PAM solution like Unified PAM that will effectively manage privileged access in your organization while minimizing risks associated with sensitive information and safeguarding your organization from external threats.
Streamline Your PAM Implementation
Dive into the robust capabilities of Securden’s Unified PAM solution with a no-obligation 30-day trial. Start optimizing your security measures now!
PAM Implementation: Common Pitfalls and How to Solve Them
Implementing PAM isn’t without its challenges. Here are five major challenges along with proposed solutions for each, explaining how you can overcome them.
Challenge 1: Legacy System Integration
Integrating a PAM solution with legacy systems can be challenging. Many older systems lack compatibility with modern PAM solutions, often requiring extensive customizations and workarounds. These complexities may increase implementation costs and delay timelines, and without proper integration, legacy systems can create security gaps that compromise the organization’s security posture.
Solution: Conduct a thorough compatibility assessment of legacy systems and engage experts in privileged access security to develop custom solutions. Consider going for Securden’s Unified PAM, which is designed to integrate seamlessly with various environments, reducing the complexity of integration.
Challenge 2: Resistance from Stakeholders
Stakeholders, particularly those with established access privileges, may resist PAM implementation due to concerns over losing control or facing restrictions. This resistance can slow adoption and create friction within teams. Without stakeholder buy-in, enforcing policies becomes challenging and could undermine the program’s success.
Solution: Communicate the value of PAM clearly to all stakeholders, highlighting benefits like security and streamlined access, and involve them early in the planning phase to ease adoption.
Challenge 3: Managing Large Volumes of Privileged Credentials
Handling a large volume of privileged credentials is one of the most intricate parts of PAM. Without proper organization, tracking, and monitoring, these credentials can easily be mismanaged or forgotten, increasing the risk of unauthorized access and potential breaches.
Solution: Use a centralized PAM tool like Securden’s Unified PAM to automate credential management, including secure storage, rotation, and access tracking, reducing human error and boosting security.
Challenge 4: Compliance and Regulatory Constraints
Meeting regulatory requirements with PAM can be challenging, especially as different industries have unique compliance standards. Failing to align PAM practices with these standards can lead to audits, fines, or other penalties, putting the organization at risk.
Solution: Work closely with compliance officers to tailor PAM settings to regulatory requirements, ensuring that access logs, audit trails, and reporting align with industry standards like HIPAA, NIST, PCI DSS, and NERC. Securden’s comprehensive audit capabilities facilitate compliance reporting and help maintain regulatory adherence.
Challenge 5: High Initial Costs and Resource Allocation
Implementing a PAM system often involves significant upfront costs and resources, from software and hardware expenses to employee training. For organizations on tight budgets, these expenses can feel prohibitive, making it harder to justify the investment.
Solution: Adopt a phased PAM rollout, starting with high-risk or critical privileged accounts and gradually expanding. Securden’s licensing model is based on the number of users rather than connections or managed passwords, making it a cost-effective choice for scalable growth.
Protect What Matters with Securden’s Comprehensive PAM Solution
Everything your organization holds dear—trade secrets, customer databases, or financial reports—is only as secure as the weakest link in its cybersecurity defenses. Privileged access management (PAM) solutions are crucial in safeguarding these assets by monitoring privileged users and enforcing the principle of least privilege across the organization.
Securden’s Unified PAM is a comprehensive solution for privileged access governance, designed to streamline and strengthen access management. It seamlessly integrates with existing IT infrastructure, offers customizable access policies, and operates on a self-hosted platform without the need for additional hardware.
In the next part of this blog, we’ll explore how Securden simplifies implementation and stands out from competitors in the market.
Take the first step toward a fortified security framework and improved cybersecurity resilience—contact our team today to see how Securden’s Unified PAM can improve your organization’s security strategy.
FAQs About PAM Implementation
1) How can you identify privileged accounts in their organization?
Identifying privileged accounts involves scanning for accounts with elevated access to data, sensitive information, or the ability to perform actions, such as those with admin privileges or emergency accounts used in critical situations. Look for accounts that can install software, access sensitive files, or modify group memberships.
Securden’s Unified PAM has automated discovery features to help organizations effectively catalog and manage privileged accounts.
2) How can Securden’s Unified PAM solution simplify PAM implementation?
Securden’s Unified PAM simplifies implementation by offering a single platform that manages privileged accounts, enforces password management policies, and provides real-time monitoring. Its intuitive design and built-in discovery tools make tracking admin accounts, managing group memberships, and updating credentials easier without additional software.
3) Can Securden’s Unified PAM integrate with existing IT and cloud infrastructure?
Yes, Securden’s Unified PAM integrates seamlessly with both on-premises IT setups and cloud infrastructures, offering compatibility with various environments. With options for PostgreSQL and MS SQL, it adapts to different setups without requiring major modifications, making it a flexible fit for diverse IT landscapes.
4) How does a PAM solution reduce the risk of insider threats?
PAM solutions enforce the principle of least privilege by allowing only necessary access to privileged accounts and monitoring all activities. They also require privileged users to update their credentials regularly and track access to sensitive data, reducing potential misuse. Securden’s Unified PAM offers real-time alerts and logs, making detecting and mitigating insider threats easier.
5) What ongoing maintenance is required after PAM implementation?
Post-implementation, PAM systems require regular monitoring and updates. Maintenance tasks include updating privileged credentials, managing access permissions, and conducting continuous discovery of new privileged accounts. Securden’s PAM automates many of these processes, ensuring consistent security with minimal manual oversight.










![What is Cloud PAM? [Definition, Features, Benefits, and Factors to Choose the Right One]](/images/cloud-pam/cloud-pam-blog-image.webp)