In the previous post, we dealt with the importance of local admin accounts, the associated security risks, and the need for managing them properly. In this part, let us analyze the pros and cons of different approaches to managing the local administrator accounts.
Before getting into the details, let us examine the various efforts made by Microsoft in managing privileged access.
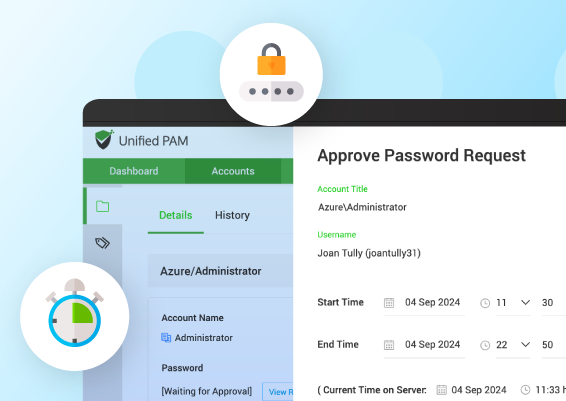
Find out how Securden PAM manages privileged access with video demo
Microsoft’s efforts to managing privileged access
A vast majority of vulnerabilities in Windows environments are related to the local admin accounts. Microsoft was obviously concerned about this fact and made sincere efforts to find a solution. First, they came up with the concept of User Account Control (UAC), which allowed administrators to log on to workstations with standard privilege and then use “Run as” to elevate rights on-demand. UAC, no doubt, was a brilliant concept, but it too was susceptible to pass-the-hash attacks, besides introducing several operational challenges.
Another significant approach was the Privileged Access Workstation (PAW), which involves separating administrative accounts from normal user accounts - physical separation of standard and privileged access. PAW requires users to access privileged accounts from a dedicated, hardened, locked-down device that is only used for privileged activities. PAW is not to be connected with the internet and won’t accept inbound connections. PAW implementation is not something that is simple and straightforward. It also introduced the burden of maintaining a separate infrastructure. User experience was severely constrained.
Of all the attempts by Microsoft, perhaps the most successful one is the introduction of the Local Administrator Password Solution (LAPS). LAPS enables IT organizations to randomize the passwords of domain-joined local administrator accounts at periodic intervals. This ensures that the local admin accounts are assigned with strong, unique passwords that are periodically changed.
Let us now examine the benefits and limitations of Microsoft LAPS
LAPS revolves fully around the Active Directory to manage the passwords of local administrator accounts. The local admin passwords are centrally stored in the Active Directory against the respective machine objects. Authorized users can retrieve the passwords when access is needed.
Through Group Policy, LAPS enforces strong, unique password usage. LAPS automatically identifies password expiration and generates a new password. Even if an attacker gains access to one local admin account, chances of lateral movement become remote. This saves your other endpoints and accounts in your network from attacks.
Simplicity - both a strength and weakness of LAPS
LAPS is very simple. It is tied to the AD and can manage local administrator accounts passwords. Nothing more. So, this simplicity is both a strength and a weakness. Its scope is too narrow.
Some of the limitations are:
- LAPS covers only domain-joined accounts
- True to its name, it covers only local admin accounts. In order to stay ahead, organizations are moving towards increased automation of their services with very little human intervention. In addition to person-user accounts, non-person (Machine accounts) high privilege accounts such as your service, domain, application, or database accounts also need protection as well.
- It doesn’t cover non-Windows environments. Enterprise environments typically have UNIX, MacOSX, and other types of devices that involve privileged access.
While LAPS serves as a great tool to manage only the local admin accounts, it doesn’t fit the needs of most organizations, which are required to secure privileged access in its entirety.
This is where the Privileged Access Management (PAM) solutions come into the picture.
Privileged Access Management (PAM) for holistic security and controls
LAPS is undoubtedly a great solution. But its usage is strictly limited to local admin accounts. It cannot offer holistic privileged access security much needed by the enterprises. A comprehensive PAM solution can help you take total control of privileged access, including local admin access across the organization. PAM solutions deal with all aspects of privileged access - centrally controlling, auditing, monitoring, and recording all access to critical IT assets.
Some of the significant advantages of PAM solutions include:
- Automatic network scans and accounts discovery
- Discover all the privileged accounts on disparate systems and devices. It will unearth even long-forgotten accounts, accounts not in use, etc.
- Consolidate all privileged accounts in a secure repository for centralized management and controls
- Manage domain admin, service accounts
- Manage the all-important domain admin accounts.
- Track and manage the Windows domain accounts are used to run services, processes, scheduled tasks, and IIS app pools.
- Manage non-human accounts and machine identities
- Manage SSH keys, DevOps secrets
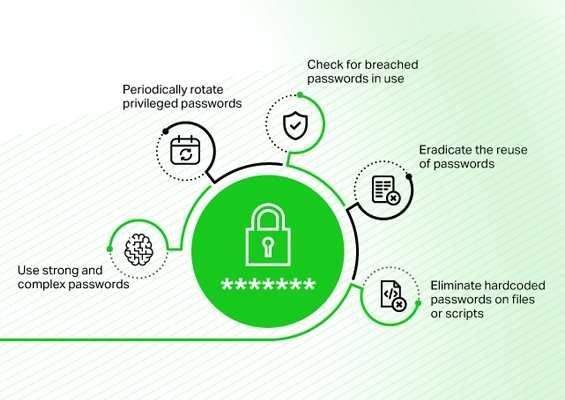
- Randomize passwords periodically
- Randomize passwords of local, domain, service, and application accounts periodically. Ensure strong, unique passwords.
-
Just-in-time access
- Ensure just-in-time access to devices and applications through automated workflows
- Grant remote access to devices and applications without showing the passwords to users, third-parties.
- Monitor activities, record sessions
- Monitor privileged sessions in real-time. Terminate session if malicious activity is found.
- Record sessions, playback whenever required.
- Maintain audit trails, generate actionable reports
- Maintain a complete trail of activities and trace ‘who’ did ‘what’ and ‘when’.
- Gain organization-wide visibility and actionable security insights on IT access through analytical reports.
From the foregoing, it is clear that organizations require a comprehensive PAM solution like Securden Unified PAM for holistic security.
In this part, we have discussed how to automate the best practices when you decide to retain the local admin accounts. Another approach to mitigate the security risks is to eliminate the local admin accounts altogether.
Let us discuss the merits and demerits of this approach in the next post.










![What is Cloud PAM? [Definition, Features, Benefits, and Factors to Choose the Right One]](/images/cloud-pam/cloud-pam-blog-image.webp)