Weak passwords, password reuse, password sharing, hard-coded credentials, lax measures to storing credentials are rampant even in big enterprises leading to massive breaches.
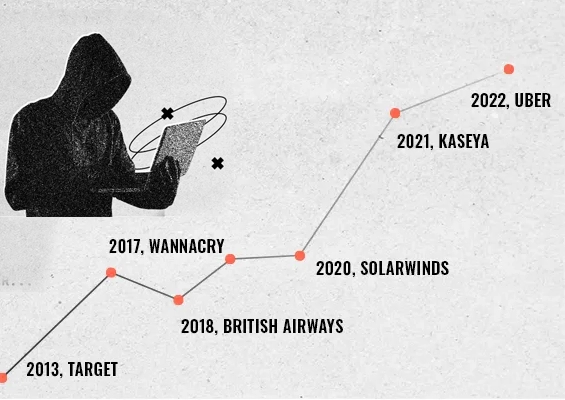
- Massive breach suffered by Verkada, Inc. a cloud-based surveillance camera provider exposing live feeds of cameras inside hospitals, companies, prisons, and schools, has its root in the exposure of hardcoded credentials.
- The likes of solarwinds123 as passwords are not isolated cases. Quite common across industries, including Fortune 1000 companies.
I happened to read a fascinating research titled “2021 Credential Stuffing Report” by F5 Labs. The report revolves around all aspects of stolen credentials, including theft, sale, and fraudulent usage. It throws light on the supply and demand sides of the market for stolen credentials in great detail and also captures the different stages of credential abuse by cybercriminals.
Among the many interesting findings, two things grabbed my attention – on the supply side of the credential spill:
- Industry behavior around password storage and management is poor
- Organizations remain weak at detecting and discovering intrusions and data exfiltration
These findings are not surprising. While many cybersecurity practices have changed or evolved over the years, the way organizations and IT teams handle sensitive passwords remains the same across the globe!
While I was going through the F5 report, another headline in social media grabbed my attention:
A hacker group has claimed that they breached a massive trove of security-camera data collected by Silicon Valley startup Verkada Inc., gaining access to live feeds of 150,000 surveillance cameras inside hospitals, companies, police departments, prisons, and schools. Hackers were able to view videos from carmaker Tesla Inc., inside women’s health clinics, psychiatric hospitals, and the offices of Verkada itself.
Quoting the hackers, media reports say that the hack was quite an ‘unsophisticated’ one: Verkada apparently exposed an unprotected internal development system to the Internet. It contained credentials for an account that had super admin rights to the Verkada network. From there, they were able to access the entire company’s network, including root access to the cameras themselves, which, in turn, allowed the group to access the footage of some of Verkada’s customers.
If media reports about the cause of the incident are correct, this is a classic case of a breach happening due to the lack of adoption of password security best practices for super admin level accounts. Hardcoding of credentials is a dangerous practice and all it requires is an accidental exposure to suffer a shocking breach.
This is just a single case in point. Sometime back, Uber suffered a similar breach. An Uber employee had hardcoded the credentials in source code. A hacker found it on GitHub and used them to gain administrative access to Uber's AWS instances resulting in the exposure of information belonging to 57 million customers.
Recently, an intern at Solarwinds was blamed of using “solarwinds123” as the password for a file server and it was discovered as being available on the internet by a researcher. Industry behavior around password storage and management remains poor and continues to result in breaches.
It is too common to see the same passwords assigned to multiple IT assets; developers reusing passwords across their personal and work accounts; passwords on spreadsheets circulated across departments; a departing IT staff exiting with a copy of all the credentials, and similar practices.
The F5 report reveals another shocking truth. When it comes to storing customer data, many organizations are still storing sensitive data like passwords in plain-text. A few others were found to be using weak hashing algorithms like MD5 or SHA-1. No wonder plain-text storage was responsible for the majority of credential spill incidents in 2020.
This won’t happen to us mindset
Industry analysts repeatedly point out that more than 80% of data breaches involve stolen credentials. Yet, IT divisions and security departments concentrate more on deploying advanced security systems and technologies but tend to overlook the basics like password security mainly due to the belief that they won’t fall under the radar of hackers. This leads to a sort of complacency with respect to adopting the security basics. Almost all of the victim organizations too believed ‘this won’t happen to us’ and eventually faced the attack.
3.2 Billion stolen passwords dump is up for grabs
Credential spill incidents have become too common nowadays and have been happening quite for some time. A total of 3.2 Billion such breached credentials (username and password combinations) are freely available on the web today. This includes over 25 million passwords belonging to the employees of Fortune 1000 companies, states a study by SpyCloud. About 133,000 passwords of C-Level executives of many organizations have also been exposed.
As most of the users have the habit of reusing the same credentials across multiple sites (including their work accounts), not just their personal accounts, but also corporate accounts face the risk of cyberattacks. Many business establishments face cyberattacks simply due to the password reuse practices of their employees.

Securden is a market leader and an outperformer in Enterprise Password Management
Get the ReportPoor password security practices --> Credential spill --> Credential abuse: A vicious cycle
The credential spill is just one part of the attack equation. Credential abuse, which follows the credential spill has far more serious consequences and could affect hundreds of thousands of businesses. Hackers could use the credentials to gain unauthorized access to various networks. But poor password security practices give rise to credential spill in the first place.
It is a vicious cycle – ignoring password storage and management best practices leads to credential spills, which in turn leads to credential abuse.

Enterprises should wake up to basic password security hygiene
Credential spill is posing a grave threat to businesses of all types and sizes. Ignoring the very basic principles of password security often lands organizations in trouble.
What are the basic measures enterprises should be taking?
Organizations should take various measures to avoid becoming a victim of a credential spill on the one hand; on the other side, they need measures to combat hackers who are using compromised credentials to perpetrate attacks. Here is a summary of some important action items.
Storing customer data
When storing credentials in the database, mere hashing of passwords is not enough. A strong hash function should be used in combination with a salt as part of the hashing process. The hash should then be encrypted. This way even if a credential spill happens, hackers will have a tough time deciphering the data.
Enforcing password management best practices at all levels
-
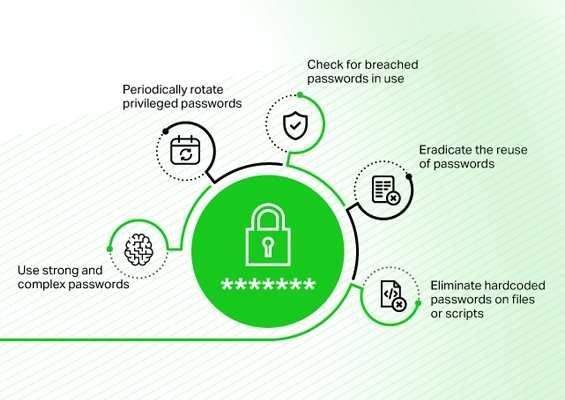
Perils of password reuse
Users should be warned about the perils of reusing the same password across multiple accounts. Passwords used on personal accounts should never be used on any of the corporate accounts.
-
Strong, unique passwords
Every single corporate login account should have a strong, unique password. The most common weak passwords like ‘password123’, ‘qwerty123’, ‘123456’ etc. should not be used even for testing purposes.
-
Eliminate the dangerous practice of hardcoding credentials
To meet various business needs, programmatic access of various IT resources and databases is required. Developers normally tend to hardcode the passwords on applications, scripts, and configuration files. Hardcoding should be avoided; instead, the passwords should be securely stored in a digital vault and the applications could programmatically access the credentials using APIs.
-
Check against compromised credentials
Periodically review the password usage across the organization and verify if any of the passwords used by employees matches the list of compromised credentials available on the web.
-
Frequent password randomization
Passwords of corporate accounts should be randomized at periodic intervals – ideally once in 45 days or 90 days. It is reported that it takes a few months for hackers to exploit the stolen credentials. Periodic password randomization helps avoid credential abuse.
-
Strong access controls
Access to the passwords should be controlled strictly based on job roles and responsibilities. For sensitive assets, just-in-time access should be enforced.
-
Monitor critical metrics
Failed login attempts, number of password reset requests are some critical factors that should be continuously monitored. Abnormal patterns on these key activities might be an indicator of an ongoing attack.
These are just the basic security measures. Though organizations certainly require advanced technologies and a variety of cybersecurity arsenals, losing sight of the security basics often leads to attacks. Password security is the foundation of information security. Internalizing this fact is critical.
Manual approaches to enforcing best practices are cumbersome and error-prone. They can be automated by using Password Manager / Privileged Access Management solutions like Securden.
Explore Securden’s Enterprise Password Vault
You can try Securden's Enterprise Password Vault for 30 days. Sign up for the cloud version or download the on-premise trial.













![What is Cloud PAM? [Definition, Features, Benefits, and Factors to Choose the Right One]](/images/cloud-pam/cloud-pam-blog-image.webp)