In today’s digital era, as information sprawl accelerates and the number of interconnected devices grows, prolonged standing access to critical systems has become a significant security risk for many organizations. With the rise of remote work and dispersed office locations, IT infrastructures have become increasingly fragmented, obscuring visibility and making holistic control more challenging.
In this blog post, we’ll explore why traditional JIT access approaches may no longer be sufficient and how the IT security world is shifting toward more dynamic and stringent methods to achieve zero-standing privileges.
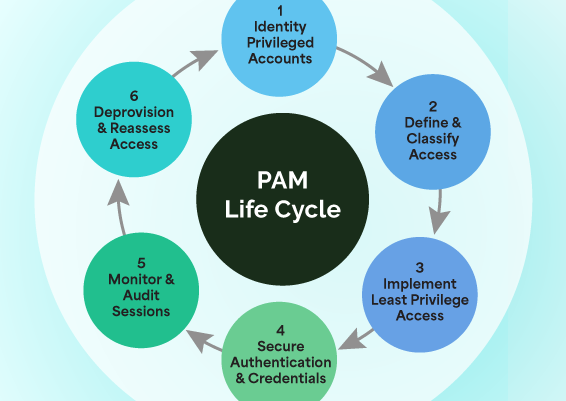
Shortcomings of Conventional JIT Access Approaches
Just-in-Time (JIT) access is typically an effective approach to eliminate standing privileges and reduce the overall attack surface by granting users regulated and controlled access to critical enterprise systems. The overarching concept of JIT access is straightforward: To give authorized users just-enough access for just the required amount of time to complete the assigned task on the target system. In other words, minimizing the exposure of critical corporate accounts and systems unless absolutely necessary for essential operations.
Organizations adopt a wide range of approaches to facilitate JIT access controls. These include approval-based workflows, temporary privilege elevation, policy-based automation for elevation requests and so on. While JIT aims to enhance security and limit standing privileges, its implementation can sometimes present challenges. These may include broad access requests, minimal justification requirements, and manual approval processes that can slow down workflows. In fact, in some cases, lengthy approval times and complex processes may lead users to seek alternative access methods, defeating the whole purpose behind JIT controls.
Traditional JIT access approaches often involve sharing credentials for critical accounts, even if only for a limited time. Without well-defined and automated workflows, there’s a possibility of residual access, which could lead to unintended security gaps.
To close security gaps and move towards Zero Standing Privileges, organizations should adopt a more dynamic and controlled approach—one that enforces precisely scoped permissions and ensures immediate deprovisioning, effectively eliminating lingering access.
Introducing ephemeral accounts—the cornerstone of Zero Trust Network Access (ZTNA)
To address these shortcomings and to enhance the effectiveness of JIT access, organizations are increasingly adopting ephemeral accounts as a key strategy. This approach involves creating short-lived, temporary credentials for accessing critical systems and applications, ensuring that privileged access is granted only when needed. Since these credentials are dynamically generated for each session, there is no need to expose or reuse high-stakes credentials. Once the user completes their task, the ephemeral account is automatically de-provisioned, along with all associated artifacts, eliminating the risk of lingering access.
Here's a typical scenario where a user accesses a remote privileged system using an ephemeral account. When an authorized user submits a remote access request to a sensitive asset, the asset's credentials are not directly shared with them. Instead, a temporary account (ephemeral account) is dynamically created specifically for this user-asset combination just before the user initiates the remote connection. This approach keeps the actual credentials confidential and, in some cases, eliminates the need for permanent credentials altogether. The result is a highly secure, one-time access mechanism that aligns with Zero Trust Network Access (ZTNA) principles.
Ephemeral accounts can be provisioned either automatically based on predefined policies or manually upon a user's access request. Even with policy-based provisioning, it's crucial to ensure that the ephemeral account is created only moments before the remote connection begins. Otherwise, the whole purpose behind JIT access gets compromised.
Automation-Driven Dynamic Provisioning
To streamline the provisioning of ephemeral accounts, organizations can leverage automated processes to create and manage temporary accounts on target systems. For example, a PAM solution often utilizes privileged credentials to perform operations like password resets on remote devices. These credentials, known as remote operation credentials, are securely stored and managed within the PAM system and are never exposed to standard users. These protected credentials enable the automated provisioning of ephemeral accounts, ensuring strict access control while eliminating the need for manual intervention.
This automated approach significantly reduces operational complexity while ensuring that users have access only to ephemeral accounts created specifically for their sessions. Once the session ends, these accounts and any associated credentials are automatically deprovisioned. If a user needs to reconnect, new credentials are generated, preventing the risk of persistent access or hidden backdoors.
Optional Approval Workflows for Enhanced Security
This is another method for provisioning ephemeral accounts. While some manual intervention is required, organizations opt for this approach to add an extra layer of security. With this control, users must submit access requests, which require administrative approval before remote connections are initiated. This ensures that sensitive assets are accessed only with explicit authorization, enhancing both security and accountability.
Organizations often make this approval workflow optional. Approval can be enforced for critical accounts, while for others, ephemeral accounts can be provisioned directly after policy-based auto-approval. This adaptive approach enables administrators to enforce security policies based on business needs, while maintaining tight control over privileged access.
Practical Use Cases of Ephemeral Accounts
DevOps
In a DevOps environment, consider a scenario where a developer Bob needs to access production systems to deploy a new feature but must avoid using permanent credentials for security reasons. These systems hold sensitive data such as repository clones, API keys, and database credentials, which require strict access controls to prevent unauthorized access or misuse.
With ephemeral access, the developer requests access to the production machine or system, and a temporary, task-specific account is dynamically created. This account has precisely scoped permissions—allowing access only to the necessary resources, such as the code repository or specific API keys required for the task. The developer can initiate the deployment or perform the necessary actions without ever needing permanent credentials, which significantly reduces the risk of credential exposure.
Once the task is completed, the ephemeral account is automatically de-provisioned, and all access to sensitive systems is terminated. This approach not only ensures that credentials are never exposed or stored permanently but also allows for a streamlined, secure workflow that integrates seamlessly into DevOps automation, enhancing both agility and security in the development process.
Manufacturing
In a manufacturing plant, consider a scenario where a maintenance technician Alice needs to access a programmable logic controller (PLC) to troubleshoot an issue on the production floor. Using traditional access methods, the technician might be given permanent access credentials, which could pose a security risk if misused or left active after the work is done.
With ephemeral access, the technician is granted temporary, task-specific access. Once the issue is identified, the technician requests access, and an ephemeral account is dynamically created on the PLC with the precise permissions needed for troubleshooting. This account is only active for the duration of the task—after which it is automatically de-provisioned, ensuring that no lingering credentials remain. Additionally, if the technician needs to access another system or device in the future, a new ephemeral account is generated with the necessary permissions.
This approach ensures that the technician only has access when needed, significantly reducing the risk of unauthorized access, credential misuse, or potential cyberattacks. Moreover, it simplifies compliance and auditing by maintaining a clear record of who accessed what system, when, and for what purpose.
With its latest release, Securden Unified PAM has introduced robust enhancements to its JIT capabilities through the addition of ephemeral accounts. This new feature, building on its comprehensive PAM offerings, helps organizations take key steps toward achieving Zero Standing Privileges.
How Securden Unified PAM Operationalizes Ephemeral Access
Implementing ephemeral access at scale without adding complexity is often a challenge for most organizations. Securden Unified PAM closes this gap by creating session-scoped, short-lived user profiles that are spun up the moment a remote connection begins and removed the instant the task is complete, keeping workflows seamless and secure. This approach prevents credential reuse, eliminates lingering access, and enforces least privilege by design — all while easing the operational burden on IT teams. With policies that define who can request access, at what privilege level, and for how long, combined with a secure remote gateway and comprehensive audit trails, Securden delivers isolation, visibility, and compliance without compromise.
Policy-driven user profile creation
Administrators can centrally configure the creation ephemeral profiles that are spun up on demand and removed instantly once a session ends. Furthermore, administrators can define granular password policies and audit rules, ensuring that every short-lived identity adheres to organizational standards while eliminating the operational overhead of manual account management.
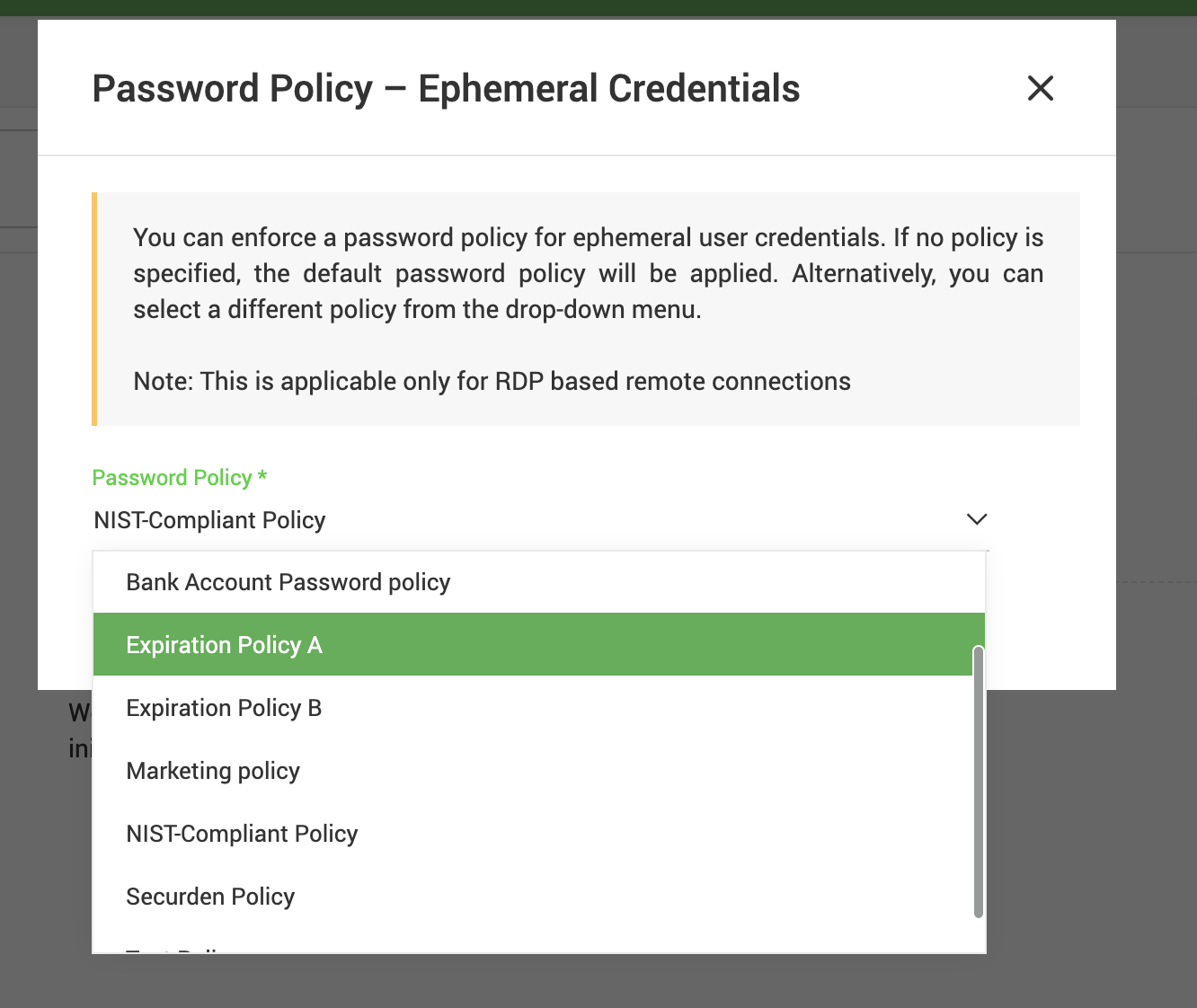
Granular, temporary access for every user-asset combination
From there, policies map ephemeral access not just to specific users, but to unique user–asset combinations, delivering a level of precision that static models can’t match. Administrators can even specify the user groups the ephemeral profile should join by simply adding the group names as comma-separated values, ensuring the account has exactly the right permissions for that session. When a user associated with a particular user-asset combination initiates a remote connection, a brand-new ephemeral profile is created on the target asset during connection initiation, aligned to the defined privilege level (standard or administrator). The account is then automatically deprovisioned when the session ends. This granular, automated control ensures that every ephemeral account is purpose-built, fully aligned with least-privilege principles, and leaves no room for lingering permissions.
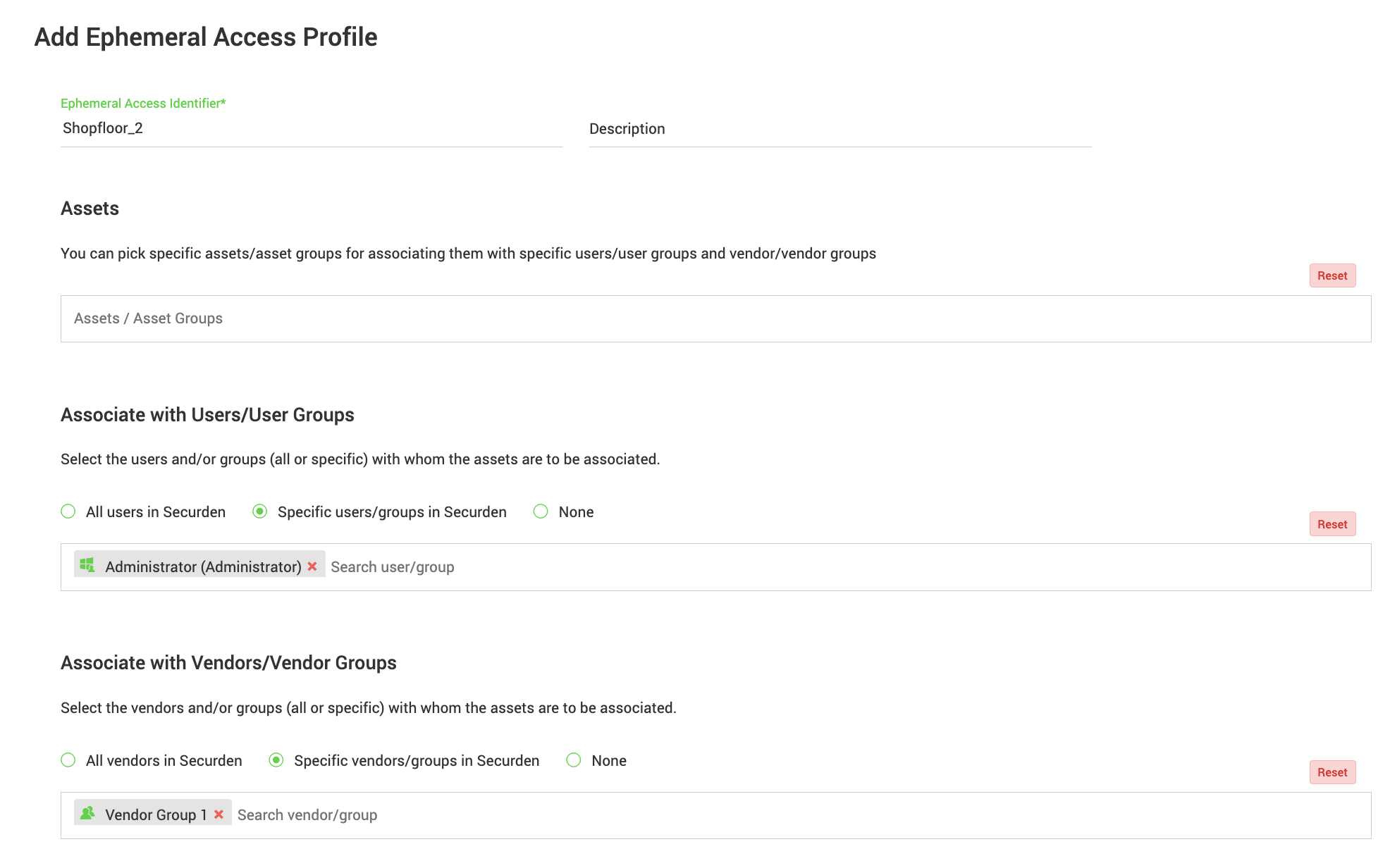
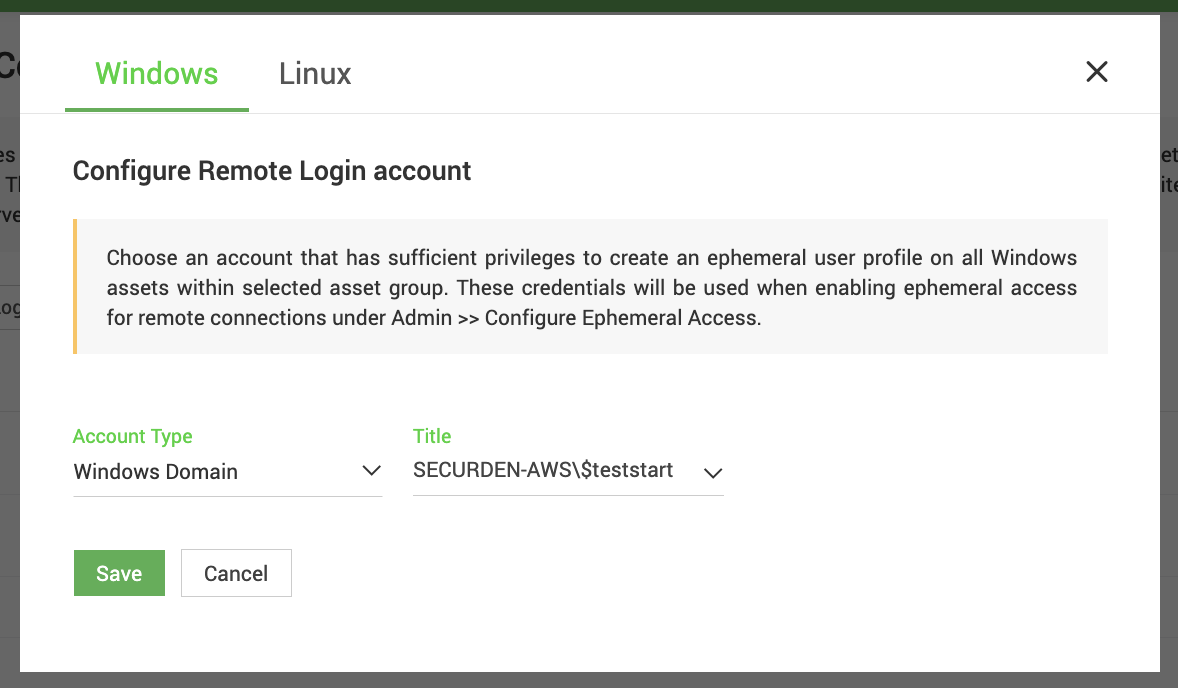
Seamless Automation, Zero Residual Access
Finally, Securden validates and secures the automation process behind the scenes. Once you’ve chosen the asset groups where ephemeral access is enabled, administrators simply configure remote operation credentials for each group — selecting an account with sufficient privileges to create and remove ephemeral profiles on all associated target machines. With this one-time setup, the platform seamlessly creates, manages, and retires these temporary accounts every time a session starts and ends. This ensures that every connection launches with a unique, isolated identity and closes without leaving any trace of persistent access.
By combining automation, policy-driven controls, and full auditability, Securden turns ephemeral access into an operational advantage. Every privileged session — whether for internal teams, vendors, or third-party contractors — is fully isolated, logged, and follows least privilege by design.
To learn more about provisioning time-limited, ephemeral access with Securden Unified PAM, click here to schedule a free, personalized demo with our product experts.



















![What is Cloud PAM? [Definition, Features, Benefits, and Factors to Choose the Right One]](/images/cloud-pam/cloud-pam-blog-image.webp)