Cloud PAM (Privileged Access Management) solutions have become ideal for securing privileged accounts and ensuring secure access to important data systems. As organizations move towards cloud-based infrastructure, managing access across distributed environments becomes complex.
That’s where Cloud PAM comes in to resolve your issues. According to ResearchGate, PAM solutions, whether cloud-based or on-premise, play an important role by offering centralized control, real-time monitoring, and scalable security for privileged accounts.
But why should you consider Cloud PAM over traditional on-premise solutions? In this blog, you will learn about the benefits of Cloud PAM, such as flexibility, cost-efficiency, enhanced security features, and ease of deployment.
Let's learn how Cloud PAM can support your organization's IT requirements while ensuring security. Let’s begin by understanding what Cloud PAM is and why it’s important.
What is Cloud Privileged Access Management?
Cloud privileged access management (Cloud PAM) is a security solution for managing and controlling privileged access to critical systems, applications, and data in cloud environments.
The platform ensures that only authorized users can access sensitive resources, information, or data through multi-factor authentication, just-in-time access, session monitoring, and automated tasks related to password management.
Additionally, setting up privileged access management in cloud environments helps eliminate unauthorized access, data breaches, and insider threats while ensuring compliance with HIPPA, GDPR, and PCI-DSS industry regulations.
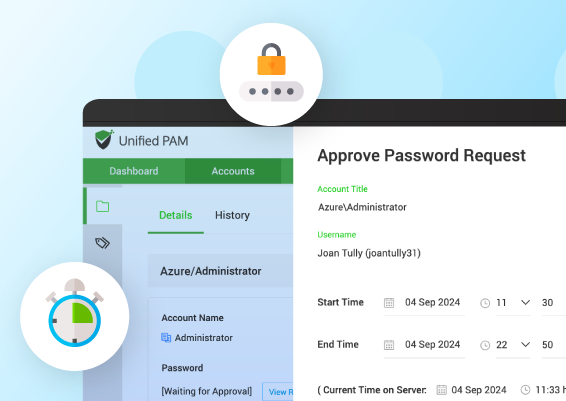
For example, Securden offers a complete cloud-based PAM that provides real-time access control access of privileged accounts, including features like credential vaulting, secure remote access, and detailed session auditing.
Securden’s Cloud PAM ensures that privileged users receive just-in-time access to cloud systems, minimizing the risk of prolonged or unnecessary elevated permissions. The platform also supports compliance by automating the enforcement of least-privilege policies and detailed reporting for security audits.
Why is Migrating to Cloud PAM Important?
Next, let’s discuss the importance of migration to cloud-based privileged access management from traditional PAM solutions.
Scalability for Growing Organizations
Unlike traditional on-premises systems, cloud PAM provides scalability. On-premise PAM requires large hardware investments and can become complex to manage as your organization grows. On the other hand, cloud PAM adjusts easily to your requirements.
Whether you have a few users or thousands, a cloud-based solution can scale up or down without extensive reconfiguration. Cloud PAM offers flexibility that lets you adapt quickly to changes while ensuring access management regardless of your organization’s size.
Reduced Maintenance Burden for IT Teams
Transitioning to cloud PAM leads to cost savings. Traditional PAM solutions involve high upfront costs for hardware and ongoing expenses for maintenance and staffing. In contrast, cloud PAM uses a subscription model, allowing you to pay only for what you use.
Choosing Cloud PAM helps to reduce initial costs and provide predictable budgeting. As your organization grows, you can easily adjust your subscription without the need to acquire new hardware.
Advanced Security Features for Protection
Cloud PAM solutions address modern security challenges by using identity-based security measures instead of relying solely on network controls. As a result, advanced features of cloud PAM make it easy to resolve challenges in dynamic environments.
Organizations can adjust access permissions in real-time based on user identity rather than static credentials, enhancing protection for sensitive data and ensuring compliance with regulatory requirements.
Cost-Effectiveness for Budget Management
Switching to a cloud PAM solution often leads to cost savings. On-premises solutions come with high upfront hardware costs and ongoing maintenance expenses. A cloud privileged account management solution, operating on a subscription model, lets you pay for only what you use.
The pay-as-you-go model reduces initial capital expenditures and provides predictable budgeting. As your organization grows, adjusting your subscription is specific by eliminating the need for new hardware.
Enhanced Accessibility for a Distributed Workforce
A cloud PAM solution improves accessibility by allowing authorized users to manage privileged access from anywhere with an internet connection. Accessibility is useful in today’s remote work environment, where teams may be spread across various locations. Remote access streamlines operations and fosters collaboration without compromising security.
Integration with Existing Systems
Cloud PAM solutions integrate with existing cloud services and applications. This compatibility simplifies privileged access management across diverse environments, including hybrid setups that mix on-premises and cloud resources. A cloud-native approach ensures that your PAM solution works harmoniously within your overall IT infrastructure.
Achieve Total Control Over Your Cloud Access
Secure your sensitive data today with Securden's advanced Cloud PAM, utilizing AES-256 encryption to protect your privileged accounts.
Next, you will learn the difference between traditional PAM vs cloud PAM.
Cloud PAM vs On-premise PAM: A Comparison
Here is a table that provides a head-to-head comparison of PAM for the cloud and on-premise PAM.
| Aspect | Cloud PAM | On-Premise PAM |
|---|---|---|
| Flexibility | Offers access from anywhere with the internet. Easily adapts to changing user needs. | Limited to physical infrastructure. Changes require significant effort. |
| Scalability | Scales quickly to accommodate varying user demands without performance loss. | Scaling requires additional hardware and time, often leading to delays. |
| Deployment | Rapid setup with minimal configuration. Provider manages updates and maintenance. | Slower deployment due to hardware requirements and manual updates. |
| Management | Automated tools reduce administrative workload. Allows for real-time adjustments and monitoring. | Manual management can be time-consuming and may delay responses to issues. |
| Cost Efficiency | Lower costs through pay-as-you-go models. Reduces the need for extensive hardware investment. | Higher initial costs for hardware and ongoing maintenance expenses. |
| Security | Features like automatic updates and multi-factor authentication enhance security. | Static security measures require frequent manual updates to address vulnerabilities. |
| Compliance | Simplifies compliance with automated reporting and monitoring capabilities. | Compliance management can be labor-intensive and prone to errors without automation. |
What are the Key Features of Cloud PAM?
Here are the key features of the cloud PAM.
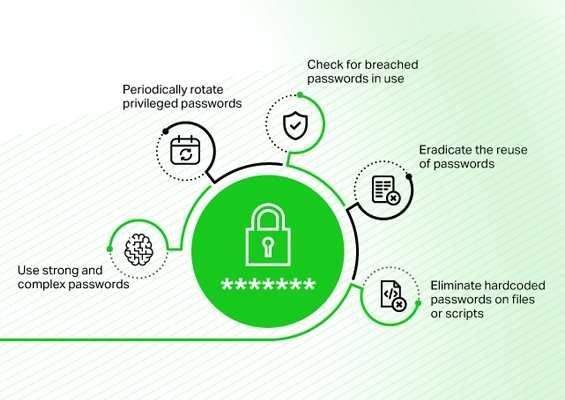
- Credential vaulting: Store privileged credentials to prevent unauthorized access and reduce the risk of credential theft. Credential vaulting includes automated password management functions, such as generation, rotation, and approval workflows, ensuring compliance with security policies.
- Session management: Monitor and control privileged sessions to record activities and audit sessions to detect suspicious actions to ensure accountability and compliance.
- Just-In-Time (JIT) access: Grant privileged access only when necessary and for a limited duration. This approach minimizes risks of missing controlled access by reducing the time-sensitive credentials that are active.
- Multi-factor authentication (MFA): Implement additional authentication layers to enhance security beyond passwords, ensuring that only authorized users can access privileged accounts.
- Access controls and policies: Define granular access policies based on user roles. The feature enables users to have the minimum necessary access and supports the principle of least privilege for maintaining security.
- Real-time auditing and reporting: Track access and activities using logging capabilities. Get compliance and forensic analysis with real-time auditing and reports, allowing you to generate reports that assess user behavior and identify potential security incidents.
- Integration with existing infrastructure: Integration of cloud PAM tools with Active Directory, Single Sign-On solutions, and other IT management systems. This integration enhances overall security by centralizing the management of user identities and access policies.
- Emergency access controls: Take immediate access in emergencies that include "break glass" scenarios without standard approval processes, while logging these actions for accountability.
- Automated governance: Combine PAM with Identity Governance Administration (IGA) to manage user and service accounts across platforms, leveraging AI for risk insights.
- Visibility into privileged activities: Increase visibility into user actions during privileged sessions. Features like session termination capabilities allow for immediate responses to unauthorized activities.
What are the Challenges of Implementing Cloud PAM?
Here are the core challenges that cloud PAM solutions help to resolve.
1. Integration Complexity
Integrating Cloud PAM with existing systems and workflows can be tough, especially with legacy infrastructure. PAM solutions often need to support both cloud-native and on-prem applications, making alignment of permissions across environments challenging.
Solution: Start with a full audit of current systems, then select a PAM solution that supports extensive APIs and offers compatibility with both cloud and legacy systems. This simplifies integration and minimizes disruptions.
2. Compliance Requirements
Many industries demand strict data protection and access controls, with frameworks like GDPR, HIPAA, and SOC 2 requiring detailed data control and audit capabilities. Implementing these standards can complicate PAM deployments.
Solution: Use a PAM provider that’s fully compliant with regulatory frameworks by providing reporting, auditing, and access monitoring. This way, you can keep compliance straightforward and help maintain audit readiness.
3. Managing Hybrid and Multi-Cloud Environments
With hybrid and multi-cloud models, maintaining consistent access controls is challenging since each cloud provider has unique security protocols. Misaligned access policies can result in security gaps.
Solution: Choose a Cloud PAM solution that provides centralized policy management and visibility across providers. Automation for enforcing policies and synchronizing identities helps keep access controls consistent across all environments.
Next, let’s learn about the benefits of using cloud PAM.
What are the Benefits of Cloud PAM?
Go through these core benefits that Cloud PAM offers to organizations compared to traditional PAM solutions available in the market.
- Enhanced security: Cloud PAM offers robust security features, including real-time monitoring, automated session recording, and advanced threat detection. These tools protect your sensitive information and help you maintain compliance with regulatory standards by ensuring that only authorized personnel access critical assets.
- Centralized privileged access management: With Cloud PAM, you can centralize privileged access controls across remote and multi-cloud environments. This approach simplifies the management of access rights, reducing complexity and ensuring a consistent security posture.
- Cost efficiency: By transitioning to Cloud PAM, you eliminate the need for on-premises infrastructure, reducing maintenance and operational costs. You also benefit from predictable subscription-based pricing, making it easier to manage your budget.
- Improved user experience: Cloud PAM enhances the user experience through features like single sign-on (SSO) and multi-factor authentication (MFA). These features provide secure yet convenient access to resources, boosting overall productivity.
- Rapid deployment and minimal downtime: You can deploy Cloud PAM solutions quickly and integrate them with your existing IT environment. This agility allows you to implement essential security measures without significant downtime or disruption.
- Auditing and reporting: Cloud PAM provides detailed logging and reporting capabilities, enabling you to easily track access activities and generate compliance reports. This transparency helps you identify potential security breaches and supports forensic investigations.
How to Choose the Right Cloud PAM in 8 Steps
Selecting a cloud-privileged access management (PAM) solution is important to enhance your organization's cybersecurity. With the rise of cloud services, choosing the right PAM tool involves evaluating key factors. Here is a structured approach to help you make an informed decision.
1. Assess Your Organization's Needs
Begin by identifying your organization’s specific requirements. Consider the number of users, the types of privileged accounts you need to manage, and your compliance obligations. Engage stakeholders from different departments to gather insights on their needs and expectations from a PAM solution.
2. Evaluate Features and Functionality
Look for key features that enhance security and usability:
- Access controls: Ensure the PAM solution provides granular control, enabling you to manage permissions.
- Session management: Check for features that allow you to monitor and record sessions for auditing and compliance purposes.
- Password management: A PAM should offer secure password storage, automatic password rotation, and secure sharing options.
- Integration capabilities: Ensure compatibility with your existing IT environment, including cloud services, on-premises applications, and identity management solutions.
3. Security Standards and Compliance
Select a PAM solution that adheres to industry-standard security protocols and compliance frameworks. Look for certifications such as ISO 27001 or SOC 2, which indicate that the provider meets rigorous security and data protection standards. Assess how the solution handles data encryption, both in transit and at rest, to secure sensitive information.
4. Scalability and Flexibility
Choose a solution that can scale with your organization’s growth. As your business expands, your PAM needs will evolve. Ensure the solution can accommodate increased users, and applications, and extend compliance requirements without a complete overhaul.
5. User Experience
A user-friendly interface simplifies the onboarding process and promotes user adoption. Evaluate the ease of use for both administrators and end-users. An intuitive dashboard can enhance visibility and streamline management tasks, reducing the time spent on training and support.
6. Cost Considerations
Consider the total cost of ownership, including licensing fees, implementation costs, and ongoing maintenance. Request a detailed breakdown of pricing models and evaluate them against your budget. Look for solutions that offer flexibility in payment options, such as subscription models or pay-as-you-go pricing.
7. Vendor Reputation and Support
Research potential vendors by reviewing customer feedback and industry analyses. Choose a vendor with a solid reputation for delivering reliable support and regular updates. Assess their customer service responsiveness and the availability of resources, such as training materials and documentation.
8. Conduct a Free Trail
Before committing to a full deployment, conduct a free trial test with a select group of users. Monitor their experiences, gather feedback, and assess the PAM solution’s effectiveness in addressing your organization’s needs. By conducting free trials, identify any potential issues before a broader rollout.
Secure Your Sensitive Information Today with PAM
With Securden's Cloud PAM, protect your passwords and sensitive information using AES-256 encryption. Experience seamless access control from anywhere.
Securden: The Smart Choice for Cloud PAM to Secure Your Business
In conclusion, cloud-privileged access management (PAM) is important for businesses looking for security and flexibility in cloud environments. You can centralize access control and implement advanced security features to enhance protection against unauthorized access and ensure compliance with industry regulations.
When choosing a PAM for cloud-native infrastructures, assess your organization’s specific needs and evaluate essential features like scalability, integration, and cost. A thoughtful selection helps businesses manage privileged access efficiently while improving overall security.
FAQs About Cloud PAM
1. What are the best practices to optimize Cloud PAM deployment?
Conduct a thorough assessment of your current access management processes and requirements. Define clear roles and responsibilities, enforcing least privilege access for all users.
Implement multi-factor authentication (MFA) to enhance security. Regularly review and update access permissions to reflect organizational changes. Automation is used to monitor and audit access activities to streamline operations and improve visibility.
2. Can Cloud PAM be used in hybrid or multi-cloud environments?
Yes, Cloud PAM is designed to function effectively in hybrid and multi-cloud environments. It provides centralized access management across different cloud platforms, ensuring consistent security policies and practices. This enables you to maintain control over privileged access regardless of where your resources are hosted.
3. How does Cloud PAM help securely manage third-party and vendor access?
Cloud PAM allows you to create granular access controls tailored to specific roles or tasks. You can set time-limited access permissions, ensuring vendors have access only when needed. Session monitoring and recording features track vendor activities in real time, providing accountability and reducing the risk of unauthorized actions. By enforcing strict access protocols, Cloud PAM helps you maintain control over sensitive information while collaborating with external partners.










![What is Cloud PAM? [Definition, Features, Benefits, and Factors to Choose the Right One]](/images/cloud-pam/cloud-pam-blog-image.webp)