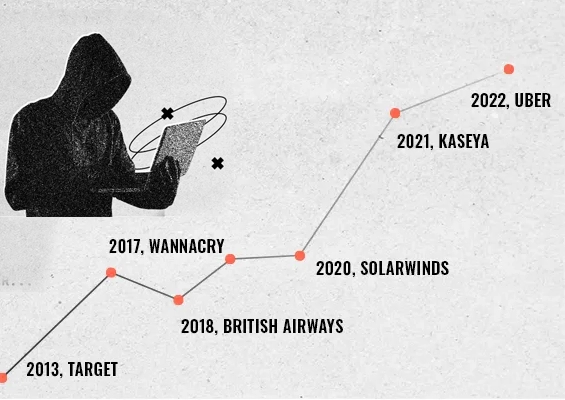
Privileged accounts are the keys to your kingdom. Protecting and managing access to these sensitive accounts is the best way you can protect your organization’s IT infrastructure. To best protect your privileged accounts, a privileged access management solution can help by providing context-based access controls and proactive security measures. Deploying a modern PAM solution and enforcing privileged access management best practices can transform your organization’s cyber security in a single stroke.
What are the 4 Pillars of Privileged Access Management?
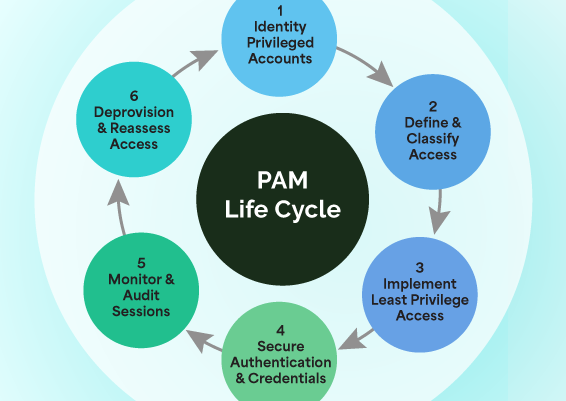
The following is a list of the four pillars of privileged access management:
Discover accounts: Discover and import all privileged accounts in your IT environment, including Active Directory, servers, applications, databases, and network devices.
Secure password management: Store, manage, and share all your passwords, keys, TOTPs, and files in an encrypted centralized vault. Integrating with various MFA solutions adds an additional layer of security to these passwords.
Audit and report: Maintains a track of all users and account activities and generates standard and custom reports for forensic and compliance purposes.
Automate workflows: Reduce laborious tasks and human error by automating policy enforcement, onboarding/offboarding, access approvals, and password rotation.
Why enforce PAM best practices?
A PAM solution is just a tool that helps enforce practices that help you improve your security posture. If you follow privileged access management best practices, you can realize the maximum return on investment and realize the full potential of the solution to provide a positive and secure experience for your employees.
So, how do you realize the full potential of your solution? Here are our top 12 recommended privileged access management best practices for you to follow while rolling out a PAM solution.

PAM Best Practice #1: Learn Everything About your Internal Privileged Access Landscape
Privileged accounts are highly valued entities in every organization. Leaving them sprawled all over the network will leave backdoors for internal users and external threats to sneak into the network without ever being detected. External users might even use privileges to create a new user account for themselves so they can come back anytime they want to.
It is essential to completely know and understand where and how privileged access and privileged accounts are used. Identifying where privileges come into play in your organization is the starting point of a successful privileged access management implementation. Connecting the dots between the privileged accounts and the dependent business functions in the organization. Having this data will help you create workflows and manage privileged access much more efficiently.
Teams within your organization can store privileged account credentials using different methods. These include a spreadsheet, notepad and sticky notes. This siloed approach to managing privileged accounts should be eliminated. Centralized management of privileged credentials will provide a holistic view of how privileged access is used in the organization. That is the next best practice to be followed.
PAM Best Practice #2: Consolidate all Privileged Accounts for Centralized Management
Privileged account discovery is an important step in securing privileged access in any network. Privileged credentials are used and can be found across the network on databases, applications, services, hardware devices, firewalls, routers etc. The type of credential used in these platforms may vary from local user accounts, admin accounts, domain accounts, and service accounts to database accounts, SSH keys, hardcoded credentials in scripts and miscellaneous privileged accounts used by third party vendors and contractors.
Regardless of the type, all privileged accounts should be identified and consolidated into the encrypted repository for centralized management. Once all privileged accounts are brought under the same umbrella, managing access to them becomes infinitely easier. One benefit of running an account discovery process is stale privileged accounts which carry a lot of risk that can be identified and managed centrally.
Centralized storage of privileged accounts presents a unique opportunity to gain complete visibility of who has access to what, gives complete control over the accounts and reduces the threat of an insider attack significantly.
PAM Best Practice #3: Enforce Password Security Best Practices
Passwords are not going anywhere in the near future. Even though many continuously try to swap passwords with biometrics like facial recognition and fingerprint, passwords have proven to be the most trustworthy and reliable. Any organization would benefit a lot from creating a competent password policy as it is often mandated in most compliance requirements. Even though the regulations keep evolving, the basic password management best practices remain the same.
Define password policies
Password policies help in making passwords used are regulated and secure. It helps set a standard that all users should adhere to when creating new passwords. The password policy designed for machine identities should be different from the policy designed for human identities.
- The passwords created for employees should be easy to remember and at the same time strong and unique.
- The passwords assigned for machine identities can be randomly generated and can include a sizeable quantity of special characters to make it long, complex, and strong.
Complex passwords with special characters and numbers are often very hard to remember and it might even go the extra mile in protecting your machine identities from insider threats.
Fun Fact: The password ‘HeLl0!!!!!!!!!!!!!!!!!!!!!’ is stronger than ‘Il@90shnj&h*’ simply because the number of exclamation marks in the first password makes it longer. Even though the first password is easier to recognize, it is stronger than the latter.
The takeaway from the above fun fact is that the passwords used by users to login to the centralized repository should ideally be a long passphrase. It should be easy to remember and strong. Periodic password resets should not be mandated for human identities as it directly and indirectly results in password reuse. Even if systems are put in place to eliminate password reuse, users often find ingenious methods to reuse the same passwords extensively. To manage human identities optimally, a suitable password policy should be designed mandating long passphrases with a long password life.
On the contrary, machine identities should be assigned a complex password, containing special characters and numbers. Complex passwords protect against dictionary-based attacks launched by cybercriminals. The passwords should be reset every 30 days (about 4 and a half weeks) and the process should ideally be automated. A limited password life will protect against credential stuffing and spraying attacks.
Change default usernames and passwords in network devices
Network devices, applications and other IT assets often come with a pair of credentials by default. The same credentials are used for all devices produced by the manufacturer and are publicly known. These credentials are intended for use during installation and testing purposes only. As soon as the devices are deployed successfully, it is highly advisable to change the default username and password. Ideally, the password used for such IT assets should be in concert with the password policy in place.
Eliminate password reuse
Password reuse is widely rampant in organizations across the world and threat actors know it. Once attackers breach an account, they try using the same password to access other related accounts in hopes of getting lucky. To limit the fallout of such breaches, password reuse should be completely eliminated. Once all your privileged accounts are onboarded on the centralized repository, you can assign unique passwords to all the accounts and curb password reuse almost completely.
Secure off-boarding of ex-employees
When an employee is relieved of their duties, it is the responsibility of the organization to rescind all access and ensure that the credentials used by the ex-employees are reset as soon as they are offboarded. There is absolutely zero-control over what a user will do, especially if the employee and the organization didn’t part ways under good terms. Enforcing password reset on all credentials that were accessible to ex-employees is the prudent thing to do. Additionally, ownership of the accounts owned by the departing user should be transferred to another user or an administrator.
PAM Best Practice #4: Enforce Multi-Factor Authentication
Once the privileged passwords are made secure with a robust policy, the assets will be safe when subjected to credential-based attacks like password spraying and stuffing attacks. However, cybercriminals have started using methods like phishing and social engineering to gain access to accounts.
To protect against such sophisticated attacks where the strongest password possible will not offer complete protection, enforcing secondary layer of authentication is recommended. Even if the attackers possess the usernames and passwords, they will not be able to gain access unless it is explicitly approved by the user. In addition to enforcing multi-factor authentication, all employees should be provided adequate training on how to handle phishing attacks. Appropriate training will make a difference when dealing with advanced social engineering attacks and MFA fatigue-based attacks.
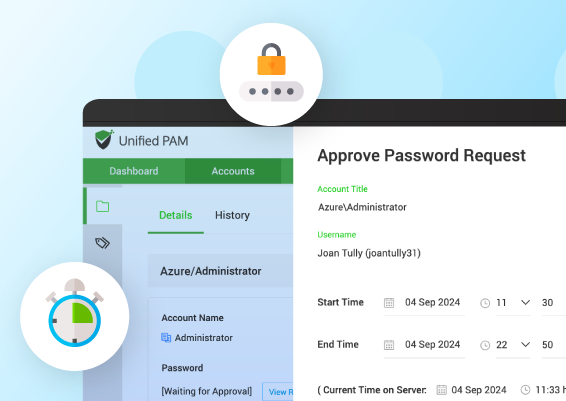
PAM Best Practice #5: Grant Just-In-Time Access
Access to sensitive assets should not be permanent for any user. Permanent access is unfettered and cannot be easily controlled, monitored, or audited. Privileged IT assets store sensitive information such as employee and customer details, payment-related information etc. Access to these sensitive accounts should only be granted when required. It may be controlled by employing a request release workflow.
The user would place an access request for the asset and will only be able to access it after an administrator reviews the request and approves it. Such a context based just-in-time workflow would provide complete control over ‘who’ gets access to ‘what’, ‘when’ and exactly ‘how’ long.
PAM Best Practice #6: Monitor Remote Sessions
Employees require access to sensitive IT assets on a daily basis. As a best practice, all privileged accounts should be adequately protected with session recording, monitoring, and auditing. Enable privileged session monitoring and management for all sensitive IT assets. Whenever a user launches a remote session to one of these privileged assets, all their activities should be recorded for security purposes.
Set up provisions for an administrator to be able to shadow such sessions. The administrator should be able to monitor the live sessions without the knowledge of the user utilizing the privileged asset.
Track and record all privileged activities for better visibility on how privileged access is used in your organization. It also helps regulate privileged activities and keep in check whether users operate within the scope of their responsibilities.
PAM Best Practice #7: Manage Shared Accounts
Hold administrators responsible for their actions. Sharing administrator accounts has traditionally been risky owing to the lack of accountability for actions and the sensitivity of the account and the privileges it carries. Enforce strict auditing and record all privileged activities to securely manage shared administrator accounts. Knowing ‘who’ had access to the administrator account at any given time will provide much needed visibility with sharing administrator accounts.
PAM Best Practice #8: Deploy Privileged Task Automation Workflows
Application to Application communication is often sensitive and involves privileged credentials for authentication. These credentials are often hardcoded into the scripts and processes for the purpose of task automation. Hardcoding credentials is a security risk as threat actors can see privileged credentials in plain text if they get their hands on the scripts of these applications.
Application to application password management best practices often involves using APIs to access privileged credentials from the centralized repository. Enforce dynamic token-based authentication for these APIs to access the repository as a security measure.
PAM Best Practice #9: Role Based Access Controls
Overprivileged users are hot targets for threat actors. They carry a plethora of permissions to access sensitive information and manage access to many other IT assets. As a best practice, it is highly advisable to revoke unnecessary privileges from users and only grant the bare minimum for performing their duties. A commonly encountered scenario in organizations is their users do not need permissions to manage access to IT assets. Only administrators need such permissions to fulfill their responsibilities.
Deploy access controls of granular nature to grant just the required amount of access to assets. Most users might need access to assets but have no business knowing the credentials that are required to access them. Granting access to IT assets without revealing the underlying credentials is highly recommended for reducing the risks associated with internal threats significantly.
PAM Best Practice #10: Enforce Least Privilege Based Access
Zero trust network access (ZTNA) focuses on authenticating each user on multiple levels before granting any access to the network assets. To enforce the principle of zero-trust, we employ credential vaulting and multi-factor authentication wherein we only grant to users after authenticating their identity through multiple checks.
Deploying measures to enforce the principle of least privilege across the network will help condense the threat surface significantly and contribute to enforcing the principle of zero-trust. The Principle of Least Privilege (POLP) works by removing basic access privileges for all users and granting access only to specific assets. In case a breach occurs, the attacker will be restricted to the surface level of the network. The lack of access privileges will prevent the attacker from reaching the deeper levels of the network and accessing the most sensitive IT assets in the network.
Deploying principles of zero-trust and least privilege in tandem will reduce the threat surface across all dimensions and place defense in depth at the very core of your cyber-defense strategy. You can enforce the principle of least privilege in four easy steps.
Eliminate admin rights on endpoints - Local accounts with administrator privileges are one of the most common entry points for attackers in any IT network. Eliminating such accounts and replacing them with standard accounts help minimize the threat surface.
Remove all unnecessary privileges - It is highly advisable to remove all unnecessary privileges through application control. Grant granular access for running, installing, and removing applications, processes, and commands.
Enforce Rule based privilege elevation - Create control policies to automate privilege elevation. Allow trusted applications to be elevated through whitelisting and block applications through blacklisting.
Just in time application control (ZSP) - Privileged access should always be granted for human users on a temporary basis. Standing privileges are granted on the basis of trust and go against the principle of zero-trust. Enforce just-in-time privilege elevation to elevate applications and process only for the required amount of time.
PAM Best Practice #11: Enforce Separation of Duties
Limit the number of privileges for a specific administrator account. No single administrator should be able to perform more than a few privileged activities. Separation of privileges will help you enforce separation of duties. Privilege separation includes separating administrator accounts from standard accounts and separating administrator accounts with different sets of privileges like auditing and reporting, account creation and deletion, provisioning access controls etc.
Each privileged account should only possess a set of privileges required to perform its designated tasks. If an attacker gains access to the privileged account, the exposure will be limited to a large extent
PAM Best Practice #12: Enforce Segmentation of Systems and Network
Users and processes that require different sets of privileges should be isolated from one another. Systems that are more on the sensitive end of the spectrum should have robust and tighter security controls. Segmenting systems based on privileges helps contain breaches within the segment. Isolating groups of systems within the network prevents lateral movement and prevents sensitive parts of the network from getting infected with malware and ransomware.
Moving best practices for Privileged Access Management to the cloud
The new trend in the PAM concept is the shift to cloud environment. The agility, scalability, and visibility needed in dynamic environments are not adequately provided by traditional on-premises PAM approaches as businesses embrace cloud-first strategies. Integrates with identity providers, enforces just-in-time access, and provides real-time session monitoring, cloud-based PAM enables centralized control over privileged identities across cloud and on-prem systems. Organizations can simplify compliance and operational overhead while mitigating evolving threats by aligning PAM best practices with cloud-native tools and zero trust principles.
Securden Unified PAM helps you enforce privileged access management best practices on your IT infrastructure by centralizing credential vaulting and policy enforcement. Powerful discovery engines help bring all your privileged accounts, even your orphaned accounts, into a centralized vault from where you can administer best practices for privileged access management as required.
Try it out for yourself now with a 30-day free trial!.
Explore Securden’s Unified PAM Solution
You can try Securden's Unified PAM solution for 30 days. Sign up for the Cloud version or download the On-premise trial.
FAQs About PAM Best Practices
1) What are best practices for securing privileged credentials?
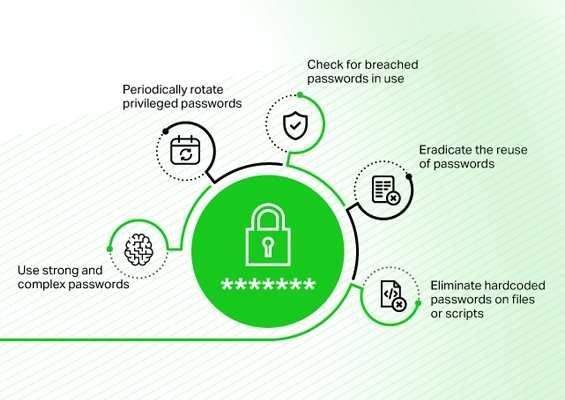
Privileged credentials are the keys to the kingdom. Best practices should be followed to secure these credentials. Some of them are listed below:
- Use centralized encrypted vaults to store, manage, and share credentials.
- Enforce multi-factor authentication (MFA) to add an extra layer of security to the credentials.
- Periodically rotate and update passwords.
- Eliminate the practice of hardcoding credentials in scripts and applications.
2) How does PAM protect against insider threats?
The privileged access management system reduces insider threats by enforcing role-based and granular access rules, and just-in-time access which minimizes unauthorized access and strengthens security controls.
3) Why is Multi-Factor Authentication (MFA) critical for PAM?
Multi-Factor Authentication is essential for PAM because it connects with a variety of MFA tools and provides an additional layer of security to privileged accounts by preventing unauthorized access.
4) How often should privileged passwords be rotated?
Privileged accounts should be rotated once every 30 days, or even after each use, depending on their sensitivity. Standard account passwords can be changed once every 60 to 90 days.



















![What is Cloud PAM? [Definition, Features, Benefits, and Factors to Choose the Right One]](/images/cloud-pam/cloud-pam-blog-image.webp)