Security has evolved far beyond physical locks and alarm systems. Today, your most critical assets are digital—protected not by metal keys but by access credentials that can unlock entire technological ecosystems. These aren't just passwords; they're the master access points that unlock your critical systems, sensitive data, and core infrastructure.
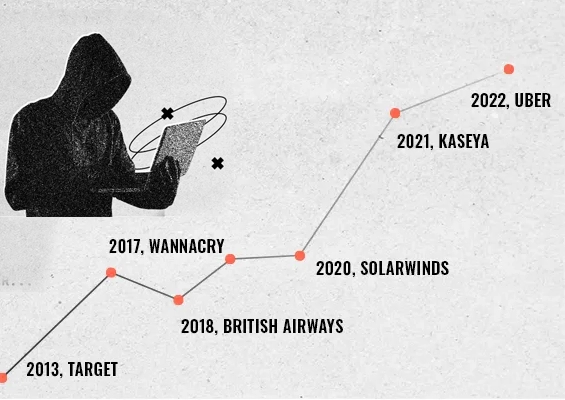
Moreover, cyber attackers are constantly seeking unguarded entry points. A single compromised privileged account can be a goldmine for them. Cybersecurity Ventures’ studies predict that cybercrime will cost businesses USD 10.5 trillion annually by 2025, with costs growing 15% each year.
In these circumstances, Privileged Access Management (PAM) stands out as your reliable guardian, safeguarding your assets and letting only the right accounts access your digital assets at the right time. But, how do you put it to good use?
Here are the top 10 Privileged Access Management use cases that will help you tackle cybersecurity threats and risks.
What is Privileged Access Management?
Privileged Access Management (PAM) is a security approach that regulates and oversees access to an organization's critical IT assets. It specifically governs access for all accounts within your organization, particularly ones with administrative access and other high-level accounts that possess elevated permissions across your IT systems.
PAM solutions work by creating a centralized platform that tracks, manages, and protects powerful privileged accounts. With its centralized approach, PAM solutions help organizations control who can access sensitive systems, when they can access them, and what actions they can take.
Common Challenges Addressed by PAM
Organizations face numerous challenges in managing their privileged users, particularly in complex IT environments like hybrid workspaces. PAM directly addresses these hurdles by offering a streamlined, centralized approach:
- Credential Sprawl: Manages and consolidates numerous privileged accounts across complex IT environments.
- Human Errors: Automated workflows and robust controls reduce the likelihood of accidental misuse or privilege escalation.
- Compliance Complexity: Helps organizations meet strict regulatory requirements and maintain detailed access logs.
- User Accountability: Creates a transparent record of who accessed what and when.
- Shadow IT Control: Provides visibility into hidden or unauthorized system access.
- Insider Threat Mitigation: Limits potential damage from compromised internal accounts.
These challenges can quickly overwhelm your admin and IT security teams. Adopting a reliable PAM solution like Securden’s Unified PAM can transform all these potential vulnerabilities into a well-controlled, secure infrastructure.
PAM goes beyond simple password protection. It provides a comprehensive approach to managing your privileged users and determining how and when they can access sensitive resources in your organization.
With the list of the most common challenges PAM can help you address out of the way, let’s shift our focus to the top 10 PAM use cases that can improve your security posture.
Overwhelmed by Privileged Access Complexity?
Stop drowning in credential management and compliance headaches. Find out how our Unified PAM solution can help you tackle all cybersecurity challenges.
Top 10 Privileged Access Management Use Cases
Whether your organization is protecting sensitive systems or addressing compliance needs, these use cases showcase PAM’s versatility and value in real-world scenarios.
1. Secure Remote Access
Remote work has become the norm but it comes with an entirely new set of security challenges. Privileged access management (PAM) solutions ensure secure remote access to digital assets by tightly controlling privileged account access and monitoring all privileged activities.
Leading PAM solutions, like Securden’s Unified PAM, offer privileged access management controls such as session recording and real-time activity tracking, allowing your administrators to maintain full oversight of privileged user access during remote sessions.
Additionally, advanced PAM features like just-in-time access and detailed audit trails help organizations with a dispersed workforce or third-party vendors requiring access to sensitive resources minimize the risks of unauthorized access.
Key capabilities of PAM for remote access include:
- Comprehensive session monitoring
- Encrypted remote connections
- Detailed access logging
- Immediate threat detection
- Controlled system access for remote workers
For instance, a financial services company could use PAM to manage remote access for offshore development teams. If a developer attempts to access sensitive data or systems outside their approved scope, the PAM solution immediately flags and blocks the attempt, safeguarding critical infrastructure.
2. Credential Management
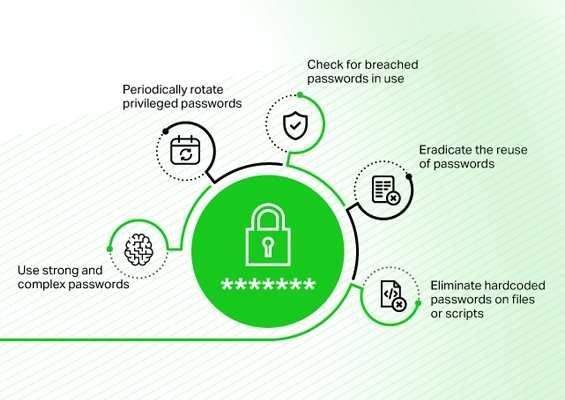
Mismanaged credentials are a ticking time bomb for organizations, especially when dealing with privileged accounts. PAM solutions are loaded with advanced features like automated password rotation and secure storage that’ll protect your organization against credential theft.
With the help of PAM solutions like Unified PAM, you can eliminate the need for your users to know or share static passwords. Administrators can easily enforce strong security policies, implement least privilege access, and track privileged account activity for compliance audits and security oversight.
Key features of PAM solutions for credential management:
- Automated password rotation
- Secure credential storage
- Complex password generation
- Elimination of shared accounts
- Centralized credential management
Consider a large healthcare organization with hundreds of administrative accounts. Manual password management becomes impossible. A PAM solution like Unified PAM can automatically generate complex passwords, store them securely, and rotate them at predefined intervals.
3. Least Privilege Enforcement
The principle of least privilege is straightforward, users should have only the minimum levels of access necessary to complete their work. PAM turns this concept into a security strategy you can bank upon, dramatically reducing potential attack surfaces.
Features like Just-In-Time (JIT) access take this a step further, enabling temporary access for human users and service accounts, with privileges automatically revoked when no longer needed.
Key benefits of Least Privilege Access with PAM:
- Minimized attack surfaces
- Temporary, context-specific access
- Automatic privilege revocation
- Adaptive access controls
- Reduced risk of unauthorized system access
Organizations can implement granular controls, such as granting marketing staff temporary access to project folders or a domain administrator time-limited access to critical infrastructure, ensuring only authorized users handle privileged account credentials securely.
4. User Lifecycle Management
From the moment a new team member joins to their eventual departure, their roles are always changing. It may be due to a promotion, migration to a different project, or assigning them to an entirely different location and role.
PAM solutions provide a dynamic approach to managing user access throughout an employee's journey with an organization. They help you automate critical access management processes, eliminating all possibilities of human error. Network administrators can quickly modify permissions without manual intervention.
Offboarding presents significant security challenges. Securden’s Unified PAM can help you immediately revoke all system access as soon as your employee leaves. Taking immediate action helps prevent potential security gaps that might have occurred during traditional manual offboarding processes.
Key benefits include:
- Automated access provisioning
- Real-time permission updates
- Instant offboarding security
- Reduced manual administrative work
- Consistent access management across organizations
Access Management That Moves at Your Speed
Your workforce is dynamic—your security should be too. Explore a PAM solution that adapts instantly to your organization's evolving access requirements.
5. Privilege Escalation and Anomaly Detection
Privilege escalation represents another dangerous attack vector used by malicious actors. PAM solutions help you put a stop to this threat with their advanced behavioral analytics that can help you detect and prevent unauthorized access attempts.
If ever a privileged account in your organization suddenly attempts to access systems outside its normal operational scope. The PAM solution immediately flags this activity. Machine learning algorithms compare current behavior against established patterns, identifying potential security breaches in real time.
For instance, if a finance team member tries accessing engineering databases during off-hours, it would trigger an immediate alert. Your security teams will receive comprehensive notifications, enabling rapid response to potential security incidents. The system can automatically block suspicious activities or require additional authentication.
6. Cloud Security
Migrating to cloud environments has increased the attack surface of organizations, making it necessary for them to change the way they manage their digital infrastructure. While traditional security models may fall short in managing access across multiple cloud platforms and hybrid environments, cloud PAM provides critical security layers for increasingly complex cloud ecosystems.
Modern PAM tools like Unified PAM come with the capabilities to seamlessly integrate with your cloud directories, SIEM solutions, ticketing systems, and multi-factor authentication apps offering a unified access control for your cloud resources. Whether your organization uses AWS, Azure, or Google Cloud, a comprehensive PAM solution provides centralized management. Administrators can set granular permissions, monitor cloud sessions, and prevent unauthorized access across different cloud platforms.
Key advantages of managing cloud security with PAM include:
- Unified cloud access management
- Multi-platform permission controls
- Comprehensive session monitoring
- Detailed cloud activity tracking
- Enhanced security for hybrid environments
A global marketing firm might use PAM to manage access to cloud-based design tools, ensuring that only approved team members can view or modify sensitive creative assets. The solution tracks every interaction, creating detailed audit trails that comply with stringent security requirements.
7. Third-Party Risk Management
External vendors play a crucial role in modern business operations. However, they also introduce significant security risks. PAM solutions help organizations manage and mitigate the potential vulnerabilities associated with third-party access to sensitive systems.
Controlling vendor access becomes more complex as businesses rely on multiple external partners. Securden's Unified PAM provides granular control over third-party permissions. Organizations can create time-limited access profiles, restrict specific system interactions, and monitor vendor activities in real time. This way, the external contractors can only access precisely what they need to complete their work.
A healthcare technology company might use PAM to manage access for software development partners. The solution allows temporary access to specific development environments, tracks every action, and automatically revokes permissions once the project concludes. Security teams can review detailed logs, ensuring compliance and preventing potential data breaches through vendor connections.
8. Incident Response and Forensics
Security incidents demand rapid, precise responses. PAM solutions wield the power to transform how your organizations detect, investigate, and mitigate potential breaches by providing comprehensive activity logs and forensic capabilities.
When a security event occurs, every detail matters. PAM tools like the Unified PAM capture intricate session recordings, user actions, and system interactions with forensic-level precision. Security teams can reconstruct exactly what happened, who was involved, and identify the potential impact of a security incident.
Key advantages of PAM solutions include:
- Detailed session recording
- Comprehensive activity logging
- Forensic-level investigation support
- Precise breach reconstruction
- Evidence collection for compliance
For example, if an unauthorized access attempt is detected, investigators can review complete session logs. These logs show precise timestamps, accessed resources, and user actions. A financial institution might use these forensic capabilities to investigate a potential data breach, providing concrete evidence for internal investigations or regulatory compliance with standards like HIPAA.
9. Compliance Audits and Reporting
Regulatory requirements continue to grow more complex for organizations across industries. PAM solutions simplify the challenging process of maintaining compliance and preparing for security audits.
Automated reporting becomes a game-changer for compliance teams. PAM tools generate detailed logs that track every privileged account action, creating comprehensive audit trails. Organizations can quickly pull reports demonstrating user access, system interactions, and security controls. This capability proves critical for industries with strict regulatory requirements, such as healthcare, finance, and government sectors.
A large hospital network might use PAM to track and report on every interaction with patient records. During a HIPAA audit, the hospital's security team can instantly generate detailed reports. For instance, a nurse accessing a patient's records during their shift can be clearly distinguished from unauthorized access attempts.
10. DevSecOps Integration
Software development moves fast. Security can't afford to lag behind. DevSecOps represents a critical shift in how organizations approach security throughout the software development lifecycle.
PAM solutions bridge the gap between development speed and robust security protocols. Traditional workflows often create friction between development teams and security professionals. A PAM approach integrated with DevSecOps changes this dynamic, embedding security directly into the development process.
Consider a software company building a complex enterprise application. Developers need access to multiple environments – development, staging, and production. Each environment requires different levels of system privileges. PAM tools provide granular access controls that automatically adjust as code moves through different stages.
For example, a junior developer might receive limited access to development environments. As code progresses to staging, access permissions dynamically expand. Production environments receive the most restrictive controls, with only senior developers and release managers granted elevated privileges.
Access Management That Moves at Your Speed
Your workforce is dynamic—your security should be too. Explore a PAM solution that adapts instantly to your organization's evolving access requirements.
5 Best Practices for PAM Implementation
Security isn't a checkbox—it's a continuous journey of strategic refinement. How can you transform all the information from these use cases into actionable strategies and adopt them? The answer lies in disciplined, strategic PAM best practices. Here are five best practices for PAM implementation to help you make the most of this technology.
Comprehensive Discovery and Asset Mapping
Identify every potential access point, categorize systems by risk level, and establish a comprehensive baseline for your security strategy. Asset mapping, when done properly, reveals hidden vulnerabilities, ensuring no critical system escapes security scrutiny.
Implement Granular Access Controls
Create permission models that reflect exact job requirements, minimizing unnecessary access privileges and potential security risks. Organizations can dramatically reduce potential attack surfaces while maintaining operational flexibility by designing microscopic access controls using PAM solutions like Unified PAM.
Automate Credential Management
Implement tools like Unified PAM that generate, rotate, and manage credentials without manual intervention, reducing human-related security risks. Manual credential handling is a security vulnerability waiting to happen. Automated systems eliminate human error by generating complex passwords, enforcing regular rotations, and removing shared administrative accounts.
Continuous Monitoring and Real-Time Alerting
Build a monitoring ecosystem that provides instant insights, risk scoring, and proactive threat detection across all privileged access points. Deploy PAM solutions and gain access to comprehensive, real-time visibility into every privileged session. With these tools, you’ll get instant anomaly detection, comprehensive session recording, and immediate threat notifications.
Regular Policy Review and Optimization
Schedule systematic reviews analyzing user access patterns, compliance requirements, and technological transformations to maintain a dynamic security posture. Your PAM strategies must be living frameworks that adapt to organizational changes, emerging threats, and technological shifts. Quarterly policy reviews ensure your security approach remains cutting-edge and responsive.
These best practices and the use cases mentioned earlier can help you draft a roadmap to incorporating privileged access management in your organization. Whether dealing with remote access, third-party partners, compliance with regulatory standards, or the plain old requirement of keeping your trade secrets under wraps, PAM solutions can help you achieve all of it and make your security systems more efficient.
Improve Your Security Posture with Securden Solutions
While we tried to cover the most useful and common use cases, we might have missed out on a few niche-specific use cases of PAM, like industrial control systems and application password management. Irrespective of your industry, these use cases and best practices must have laid a solid foundation for applying PAM in your organization.
As a leader in privileged access governance, Securden has dedicated solutions for service providers (Unified PAM MSP edition) with advanced features like endpoint privilege management, automatic password rotation, automated workflows, AD integration, and privileged session recordings.
Don't leave your organization's security to chance. Take action today by exploring how Securden's Unified PAM can transform your approach to privileged access management. Contact us now for a personalized demo and see how our solutions can fortify your security infrastructure while enhancing productivity.
Secure your privileged access today.
Access Management That Moves at Your Speed
Your workforce is dynamic—your security should be too. Explore a PAM solution that adapts instantly to your organization's evolving access requirements.
FAQs About Privileged Access Management Use Cases
What are the key components of a Privileged Access Management (PAM) solution?
A PAM solution typically includes features for managing privileged accounts, controlling access to sensitive resources, and monitoring privileged activities. Key components often involve secure credential storage, session management, and robust authentication mechanisms to ensure that only authorized users can access sensitive data.
What is the role of PAM in securing cloud environments?
PAM plays a crucial role in cloud security by managing privileged access to cloud-native security tools and resources. It helps organizations protect sensitive data by enforcing the least privilege principle, ensuring that users have only the necessary levels of access to perform their tasks without exposing the system to internal and external threats.
Can PAM be integrated with other security tools?
Absolutely! PAM solutions like the Unified PAM can be seamlessly integrated with other security tools such as SIEM systems, identity management solutions, and multi-factor authentication platforms. It enhances overall security posture by providing a comprehensive view of privileged access and enabling better management of privileged passwords and accounts.
What are the risks of not implementing PAM in an organization?
Without PAM, organizations face significant risks like credential theft, privilege abuse, and unauthorized access to sensitive data. This lack of control can lead to data breaches, compliance violations, and potential damage from both internal and external threats, ultimately compromising the organization’s security posture.
How can organizations measure the success of their PAM implementation?
Organizations can measure PAM success by tracking metrics such as reduced incidents of privilege abuse, improved compliance audit results, and decreased time spent on administrative tasks. Additionally, monitoring the effectiveness of access controls and identifying malicious activities can provide insights into how well the PAM solution is functioning in protecting sensitive resources.













![What is Cloud PAM? [Definition, Features, Benefits, and Factors to Choose the Right One]](/images/cloud-pam/cloud-pam-blog-image.webp)