


An unintentional clicking of a link, downloading an email attachment, or installation of unapproved personal software could introduce malware and make your organization prone to data thefts and ransomware attacks.
Malware propagation is among the biggest threats faced by organizations of all types and sizes.
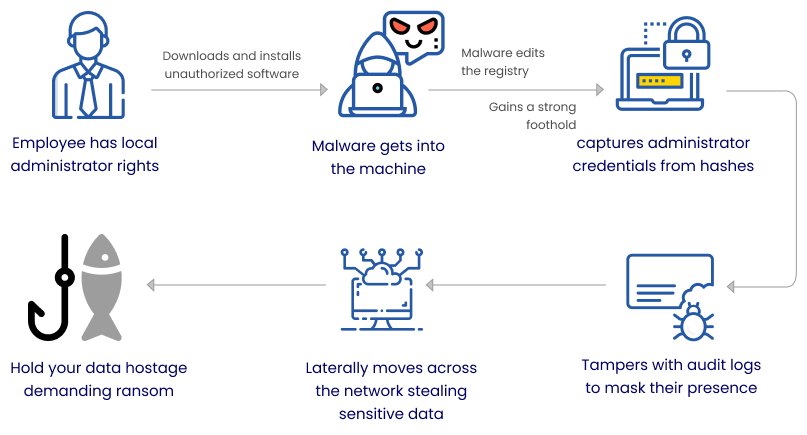
Malware quickly and easily spreads through the installation of unapproved software, pirated tools, opening malicious email attachments, clicking malicious URLs, visiting harmful pages (drive-by downloads), and so on. Even tech-savvy end-users can unintentionally fall prey to any of these attacks and malware would gain a strong foothold.
Most of these attacks happen mainly because end-users possess local administrator rights. When your employees work from home, quite unintentionally, they tend to do all these.
After getting on to a computer, the malware goes about editing the registry gaining a strong foothold, captures credentials, tampers audit logs, and moves laterally across the network stealing sensitive data.
The best practice approach to prevent security issues is to enforce least privileges across the organization by removing local administrator rights from all endpoints. But this could lead to productivity issues and frustration as employees will have to approach the system administration team even for trivial needs.
To avoid that, administrator rights removal should be combined with robust endpoint application control. Define and control which applications can be run by standard users. Allowlist trusted applications and prevent unapproved and malicious applications. This empowers standard users to seamlessly run approved applications (that would otherwise require admin rights) whenever needed. When specific users require broader privileges, you can grant them time-limited, fully controlled, and comprehensively audited temporary administrator access on a need basis. This is controlled by a well-defined workflow, which takes care of automatically revoking access once the predefined time has elapsed.
Securden Endpoint Privilege Manager helps you to precisely manage privileges without impacting productivity. It seamlessly elevates individual applications and processes for standard users. Through robust workflows and policy-based controls, end-user experience remains the same even after administrator rights are removed.
