Unified PAM
Product Tour
Screenshot walkthrough of important features. Request a demo
to dive deeper into the functionality of each feature.

Introduction
Go through the important features of Securden Unified PAM in the form of a series of screenshots. Here are a few basics you should know before going on a journey through the product:
What are accounts in Securden?
Any credential or login information that we store in the product is considered an account.
Who are users in Securden?
Anyone who would need access to the product interface is considered a user.
What is the concept of account ownership?
Any user adding an account in PAM is considered its owner and will have full rights over managing the account and modifying its details.
This walkthrough will take you through the administrator interface of the product, end users will have a limited view based on the permissions and accounts allotted to them.
Now that we have a basic understanding, let’s dive into the first section of the product tour – User management.
User Management
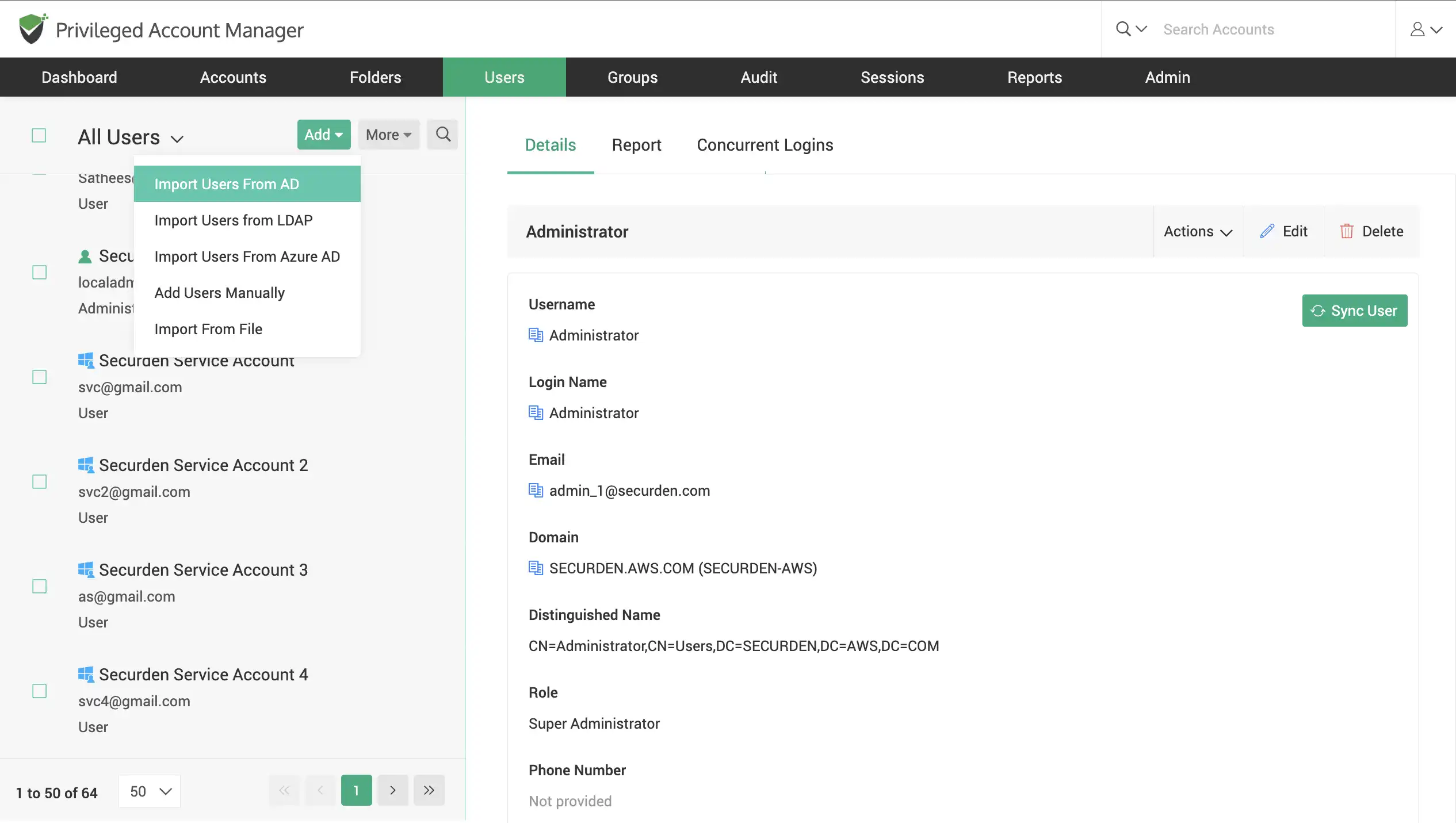
Import your users in PAM
As an administrator, you can add your users into Securden for easy management. This allows you to establish access controls and restrictions for users needing access to privileged accounts and resources.
Versatile user import from AD, Azure, and LDAP
If your organization utilizes a directory service such as Native AD, Entra ID (Azure AD) or LDAP, Securden lets you import your users, OUs, and user groups directly from the service.
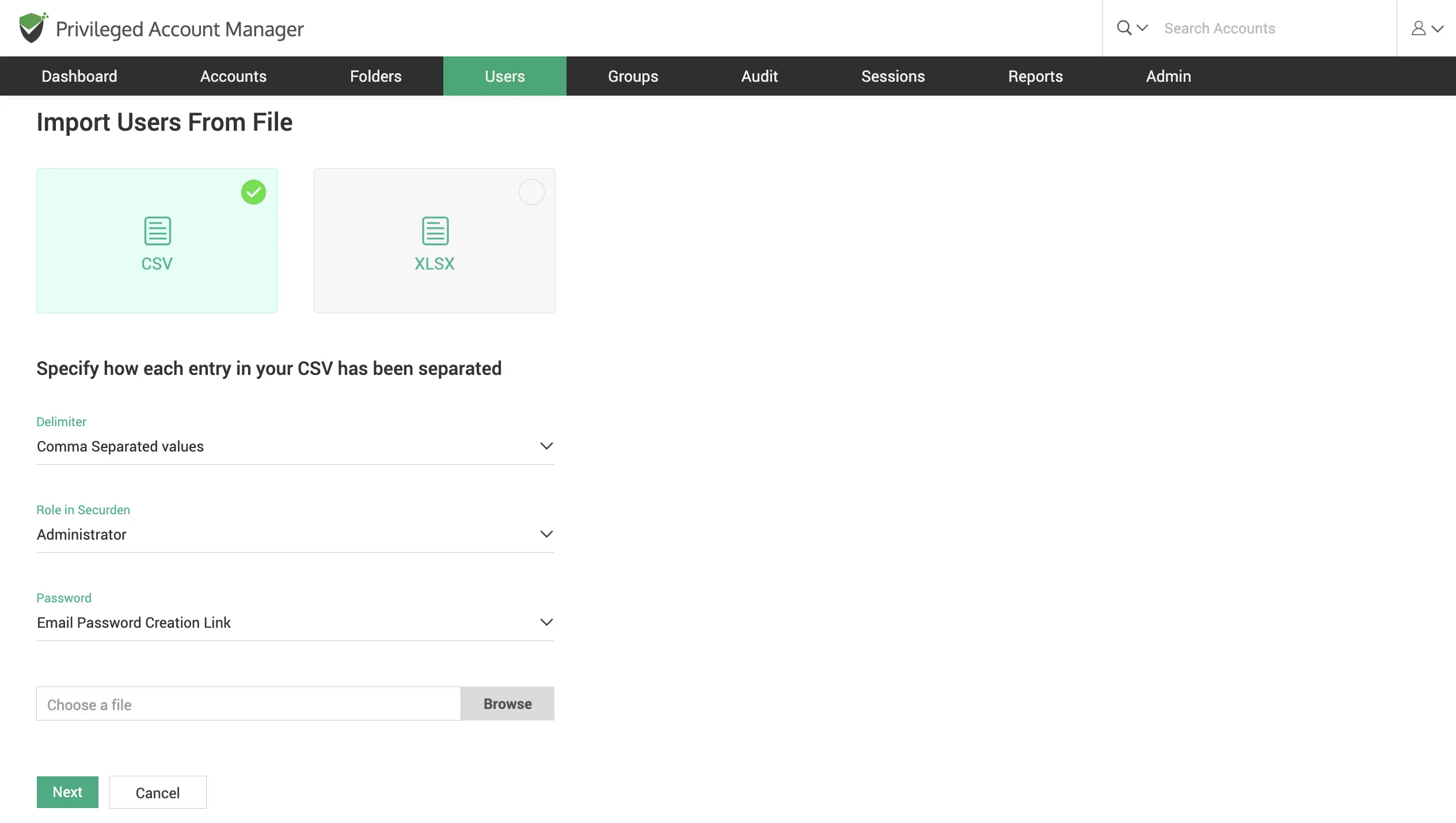
Onboard users from a CSV/XLSX file
Easily import users if you have their information stored on a .csv or .xlsx format file. You have the provision to assign users the role they will take up when onboarded into the solution.
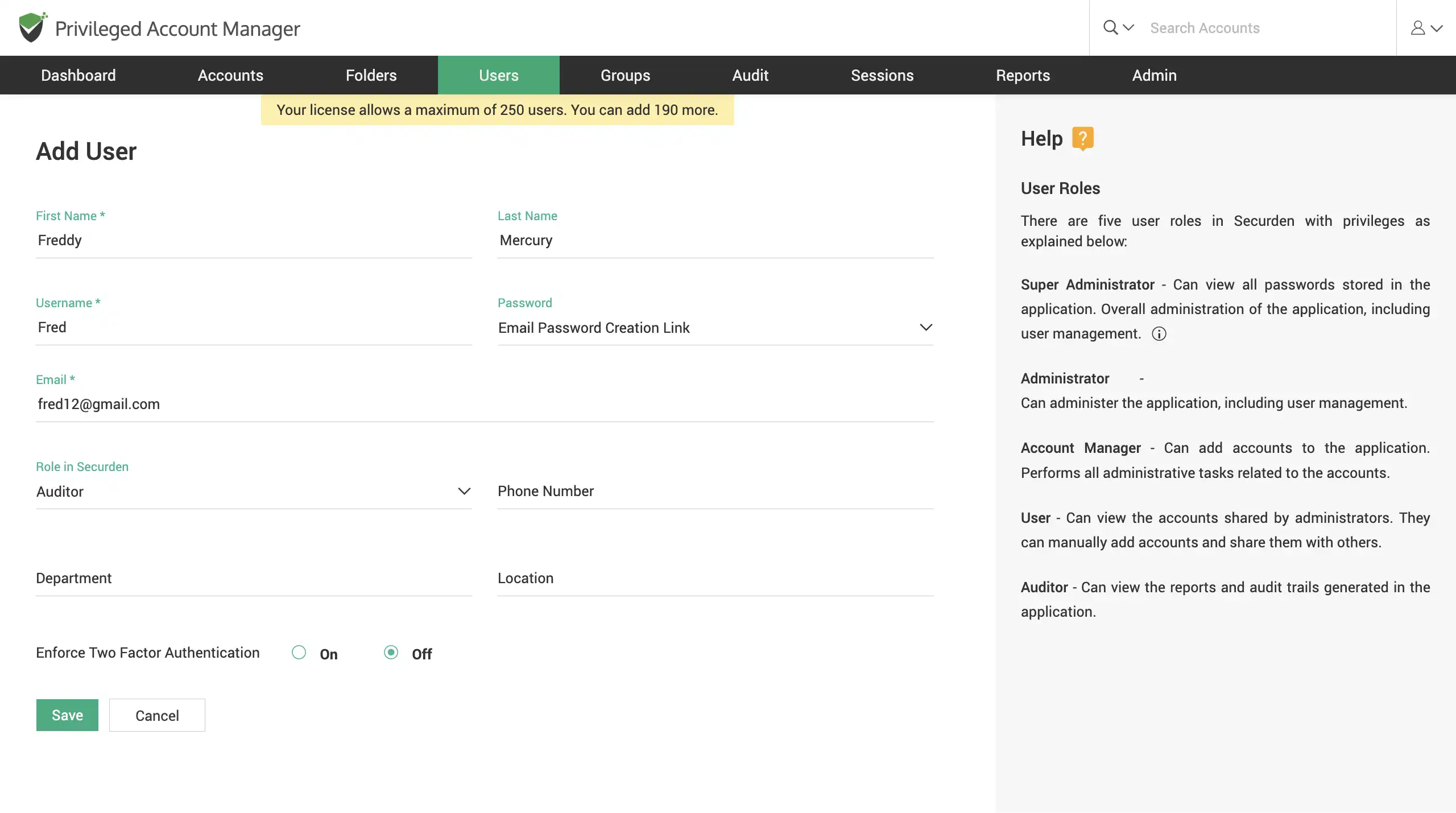
Onboard users manually
Locally create accounts, making use of the native authentication. (Typically creating a username and password for the users to login). Once you add the user, you need to assign them a particular user role.
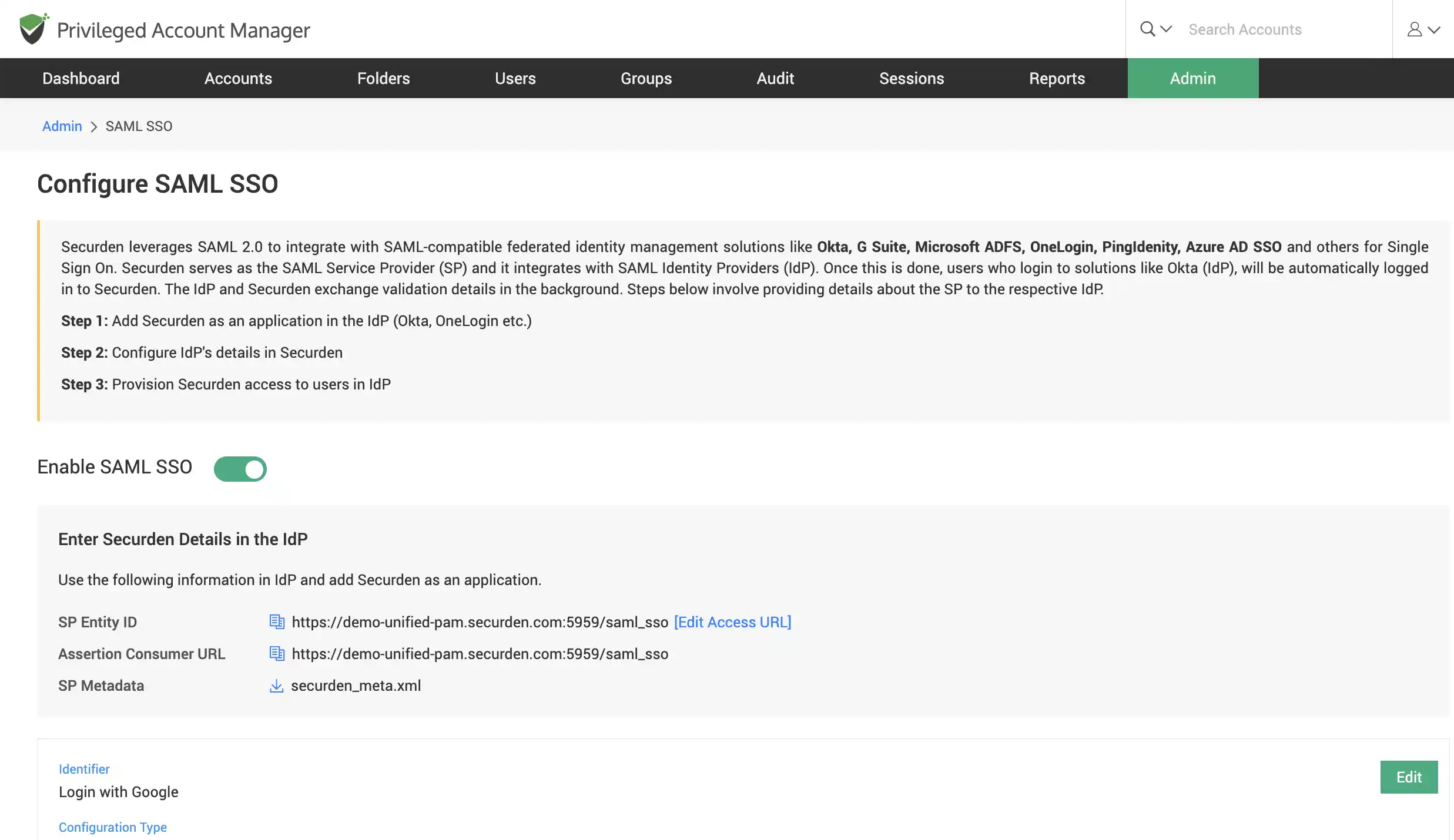
Leverage Single-sign on capabilities (SSO)
Integrate with SAML-compatible federated identity management solutions like Okta, G Suite, Microsoft ADFS, OneLogin, PingIdenity, Entra ID (Azure AD) SSO and others to provide a seamless Single Sign On experience for your users. Users who login into these SSO solutions can log into Securden with a single-click.
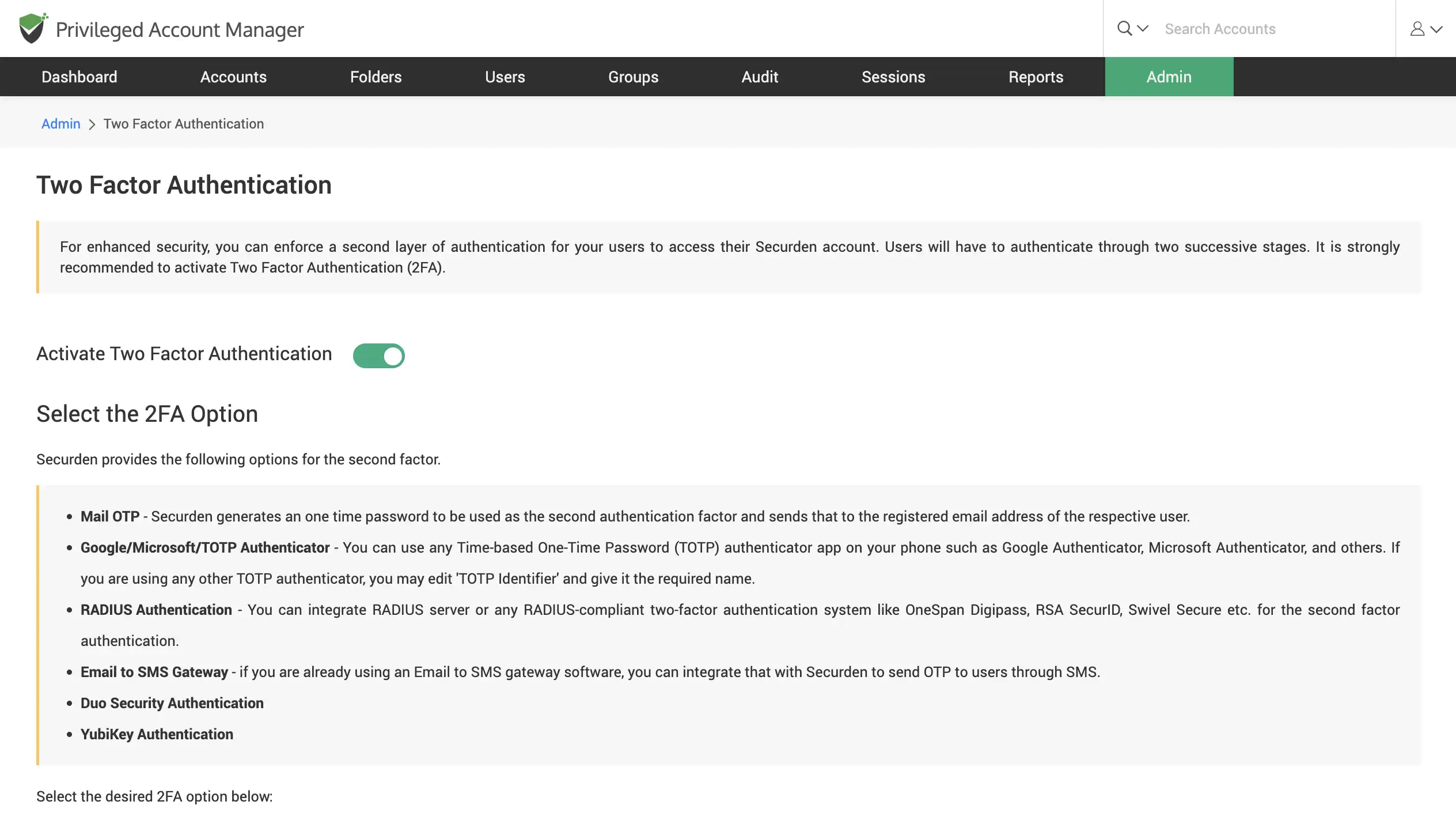
Set-up multi-factor authentication (MFA)
Set-up 2FA to let onboard users securely login into Securden with multiple levels of authentication. Readily integrate with industry tools like RADIUS, YubiKey, Duo, Mail OTP, and others.

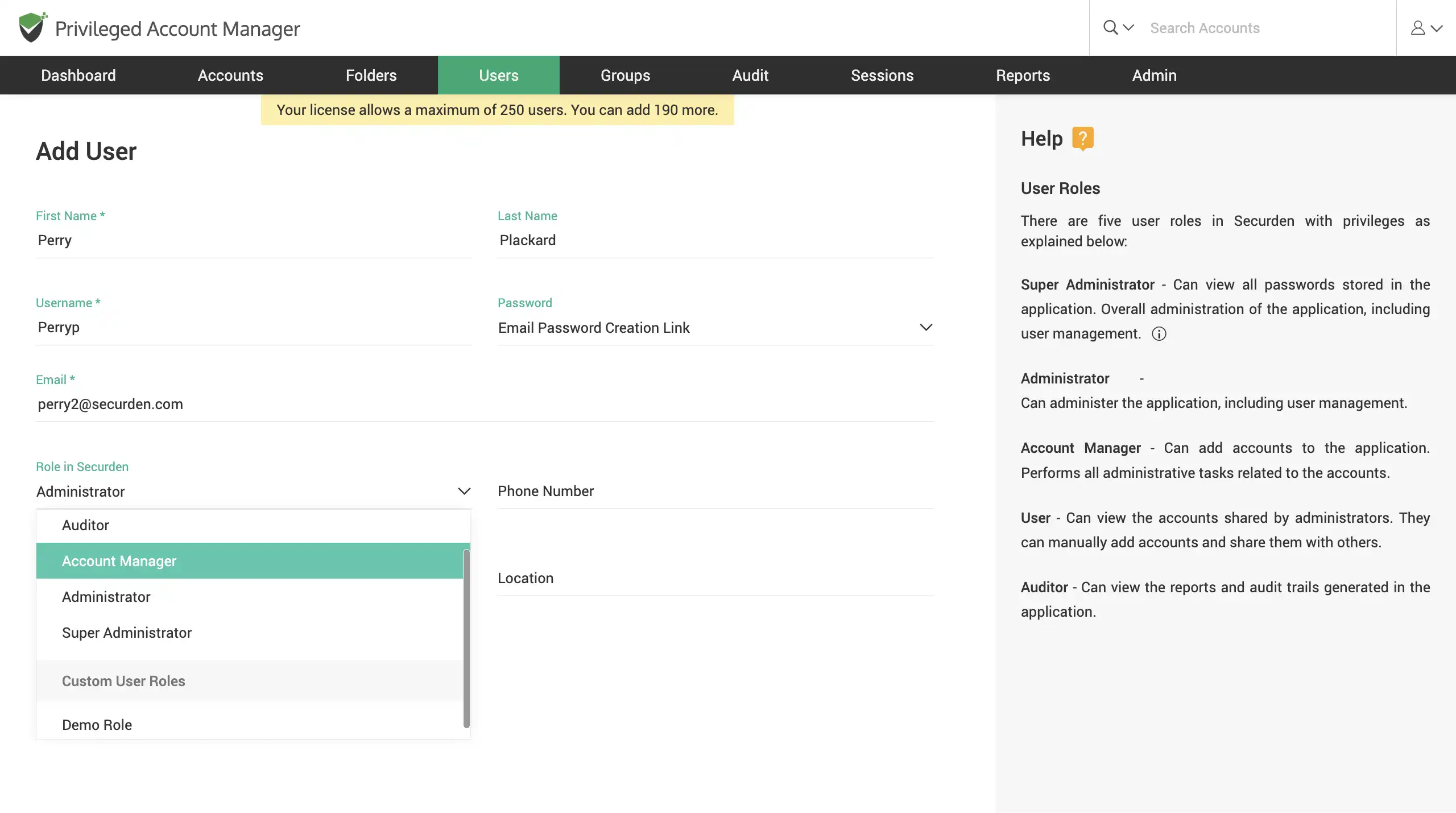
Establish role-based access controls
Once you add users, you can bring them under the purview of access controls. Users can have varying levels of access permissions within the application based on their role. You can select a role from the five pre-defined roles or create a custom user role.
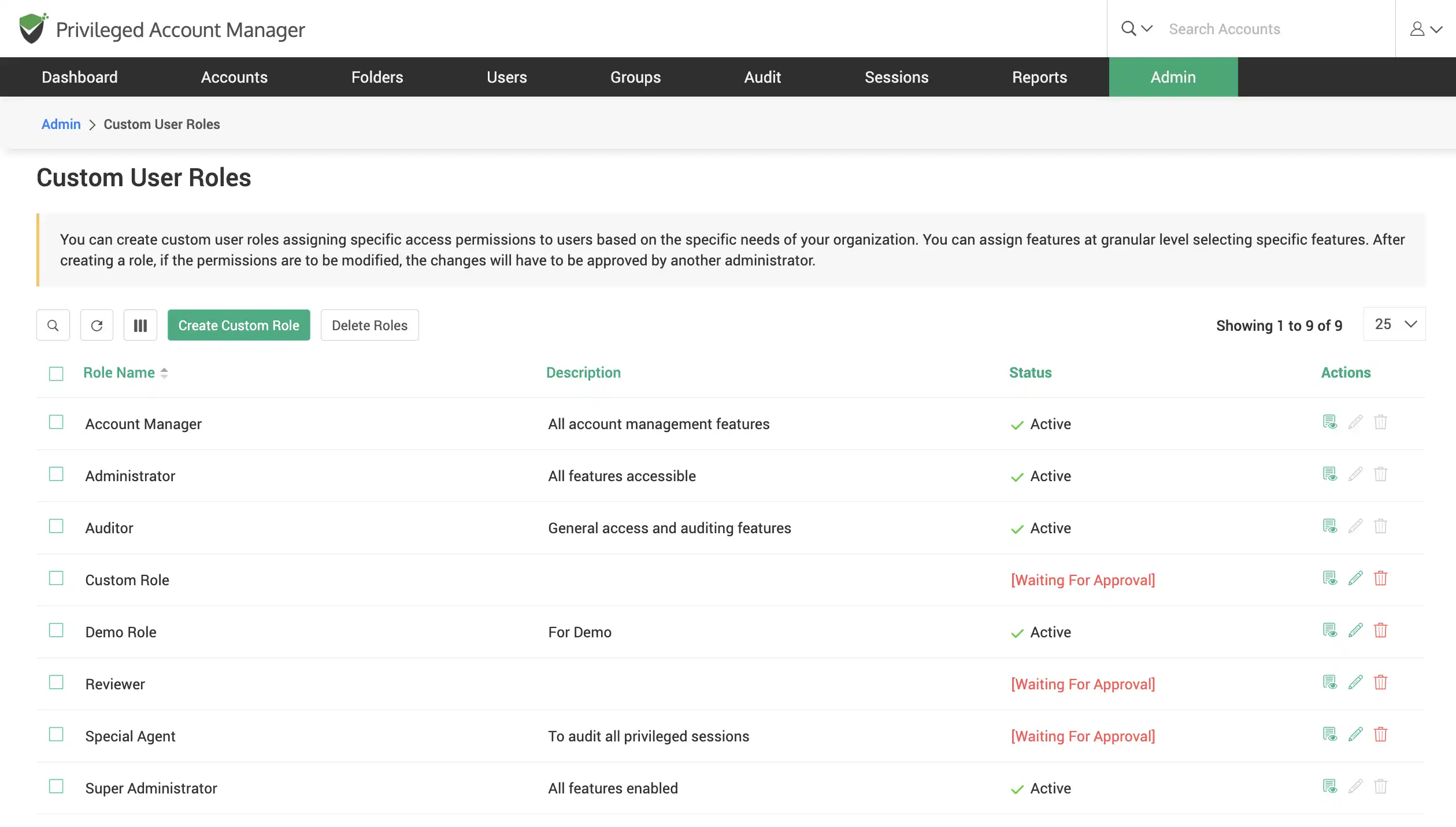
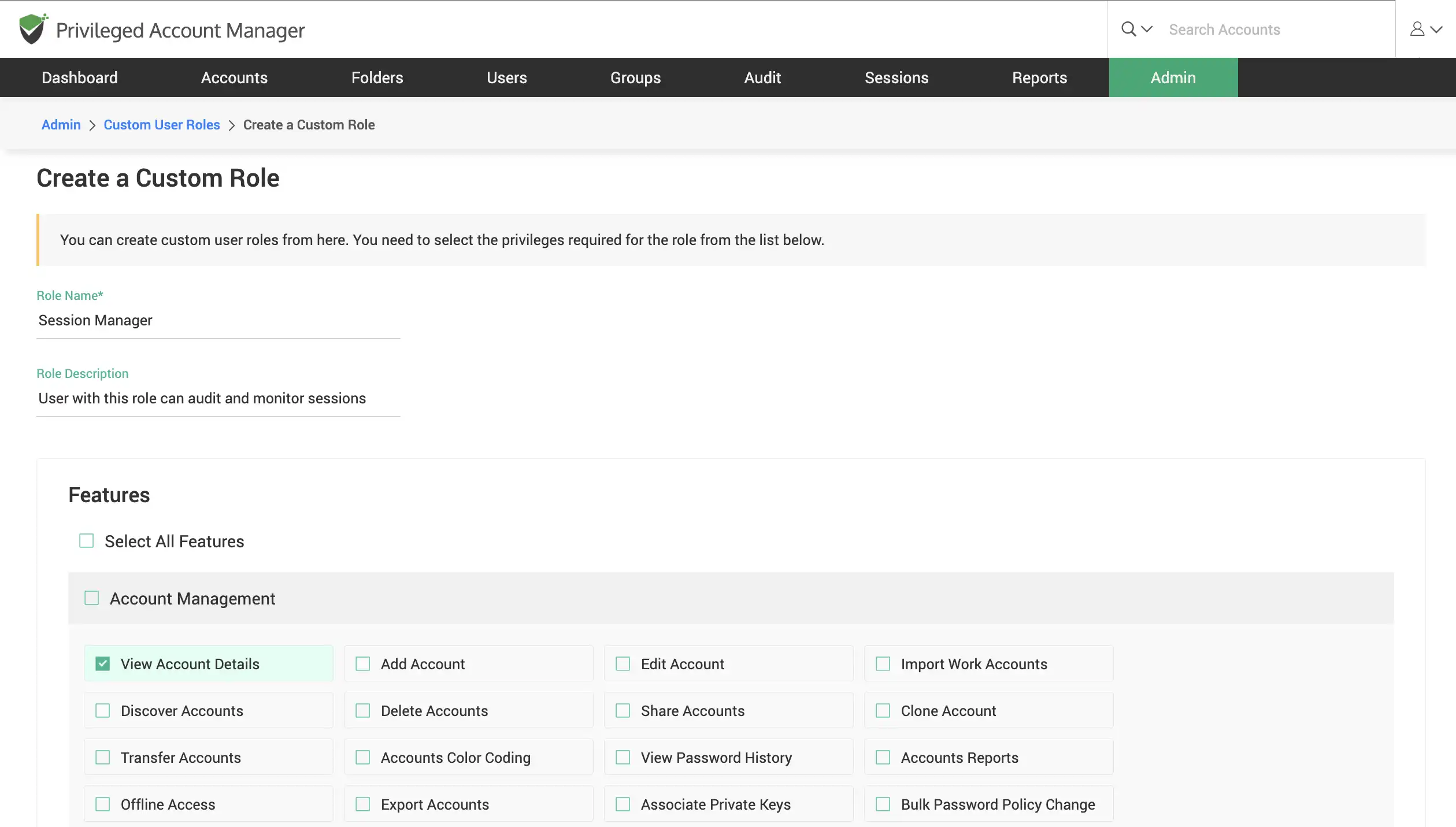
Create custom user roles
Custom user roles allow you to define tailor-made roles to let users perform selective operations in Securden. This gives users specific, limited management capabilities so they can carry out tasks that are only within their scope of work.
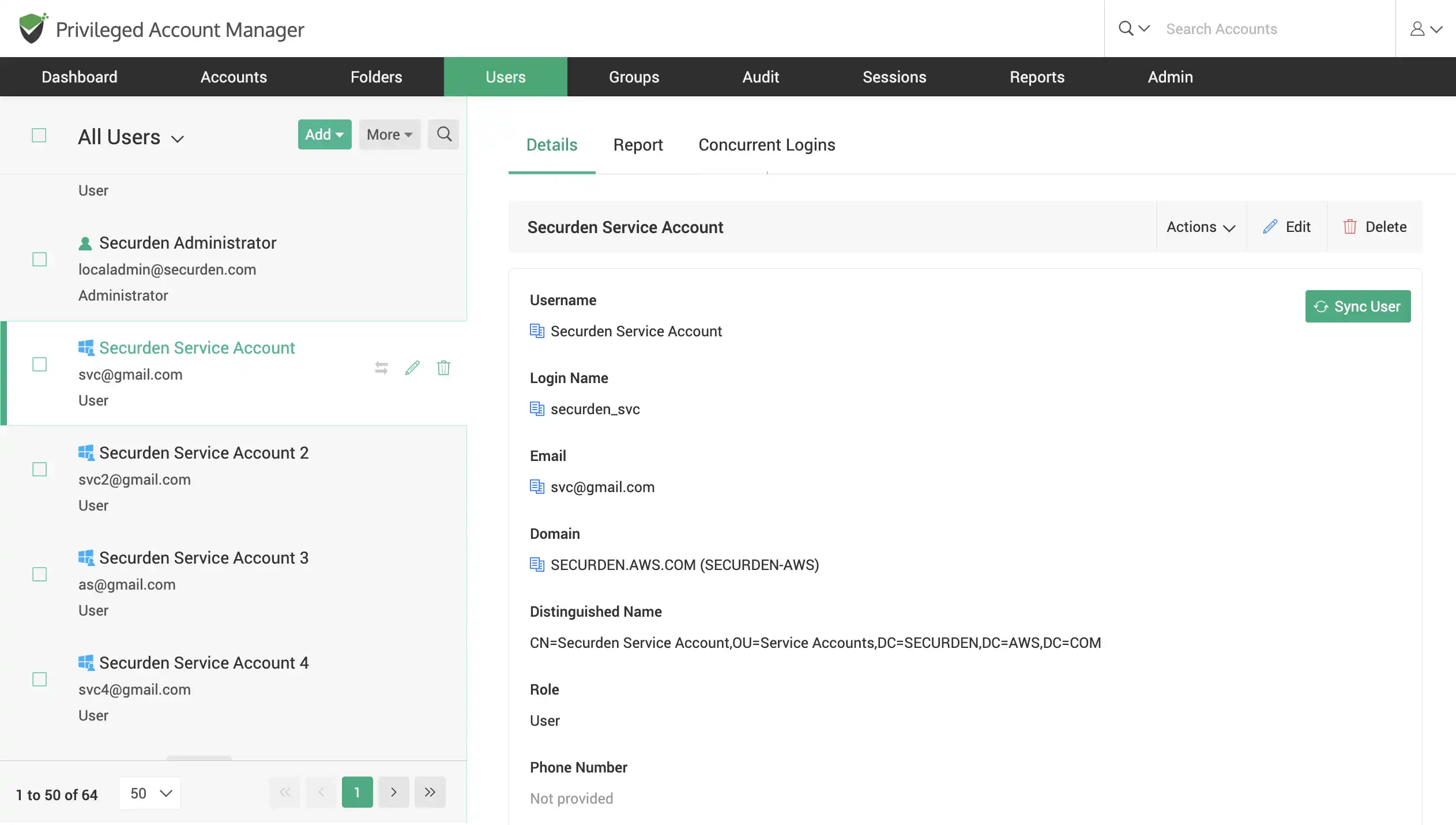
Synchronize users with AD/Entra ID (Azure AD)
Keep in sync with your AD/Entra ID (Azure AD) to replicate your organizations’ user and user-group structure. This ensures that members added and removed in your AD group directly reflect in Securden.
Once you’ve onboarded your users and set up their roles, the next step would be centrally consolidating all your privileged accounts for management.
Account Management
Build a central repository of all your passwords and privileged accounts
PAM serves as the centralized repository of all sensitive data, including passwords, keys, license files, certificates, and more.
Search and consolidate all privileged accounts in your organization. Gain full visibility over orphan and hidden accounts to obtain a comprehensive view of the firm. Manage and classify accounts for easy access management.
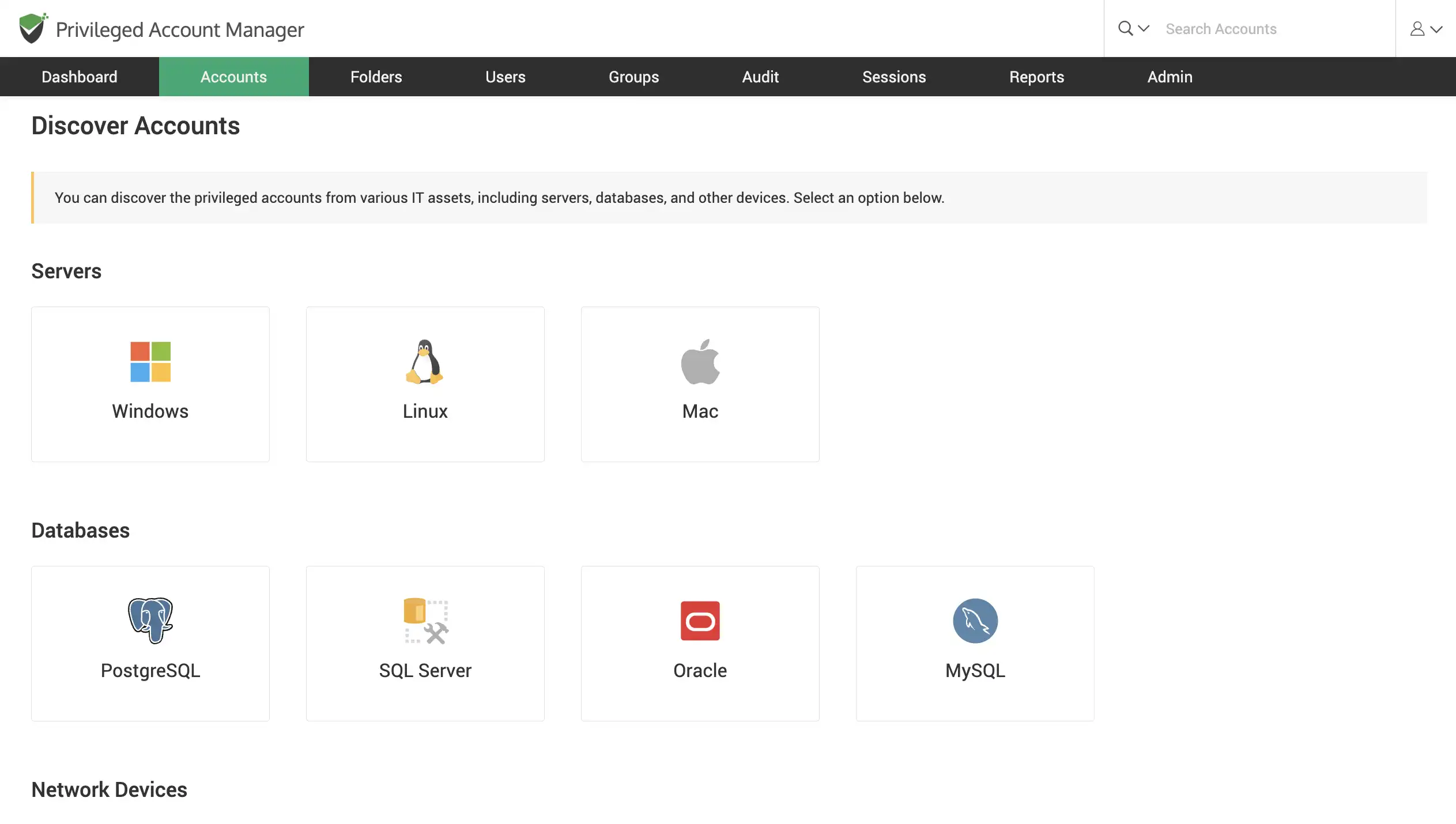
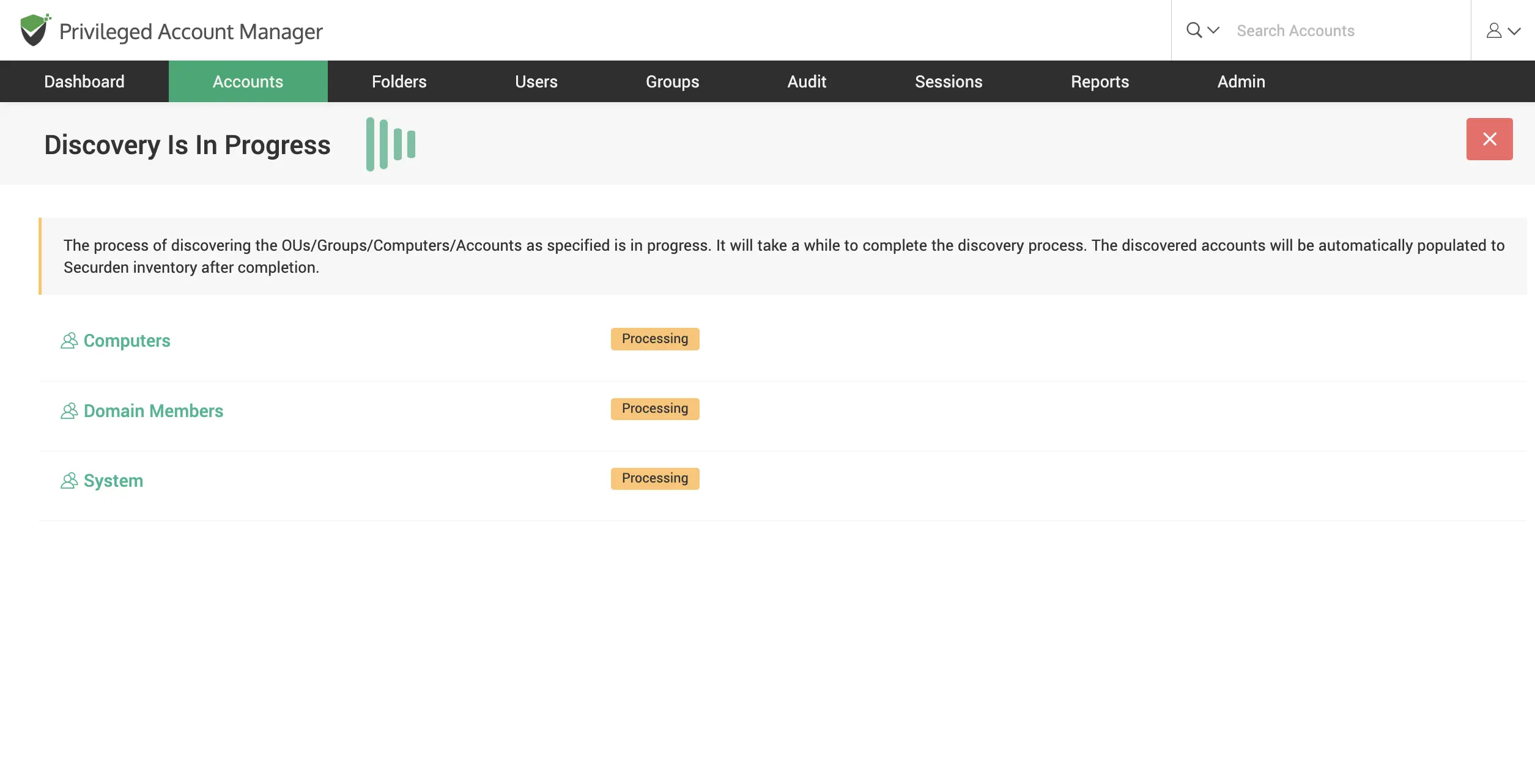
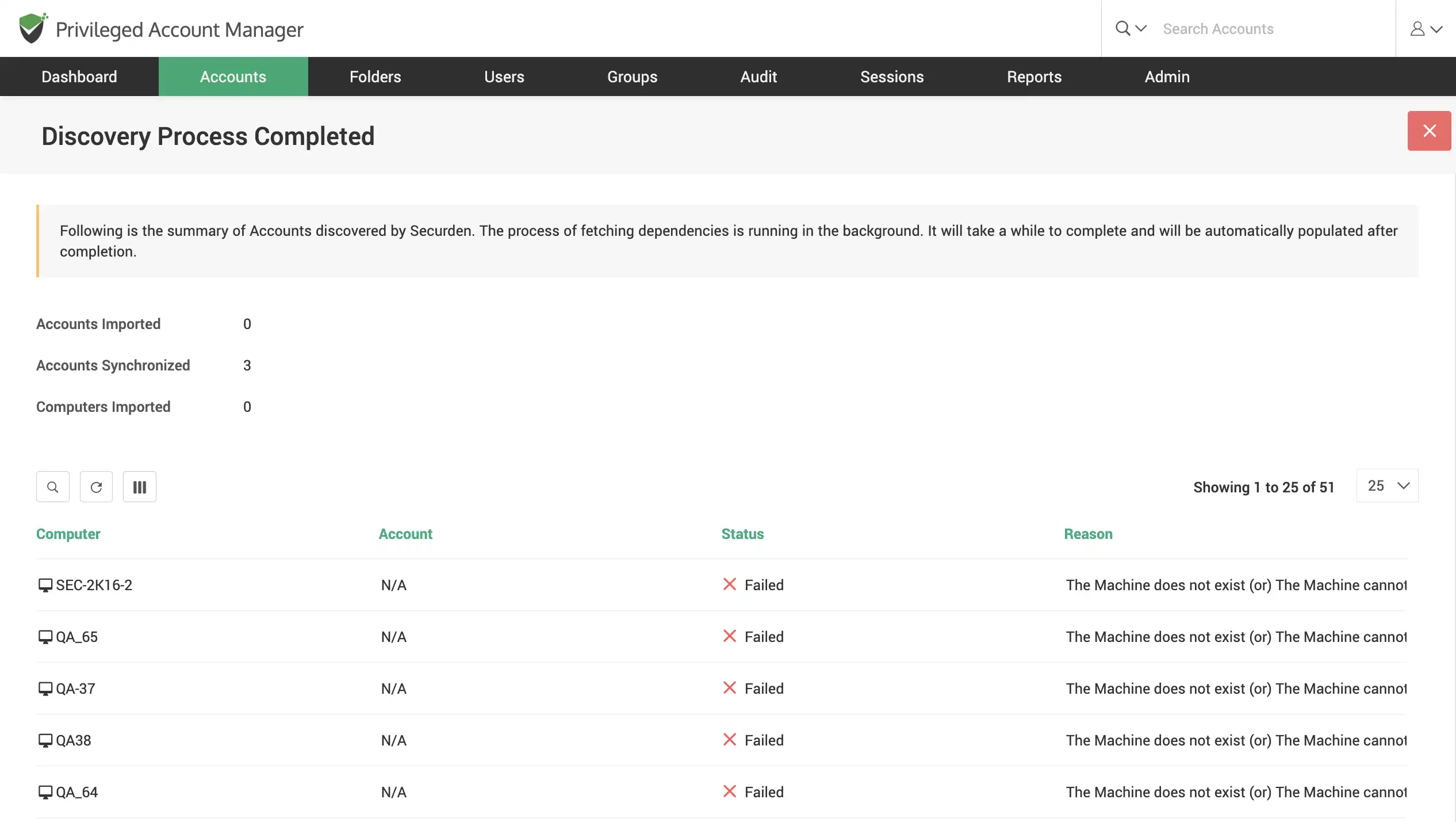
Discover IT assets and privileged accounts
Scan your network to discover devices and accounts, including windows server accounts, database accounts, and network devices across your IT infrastructure and consolidate them in Securden for efficient administration.
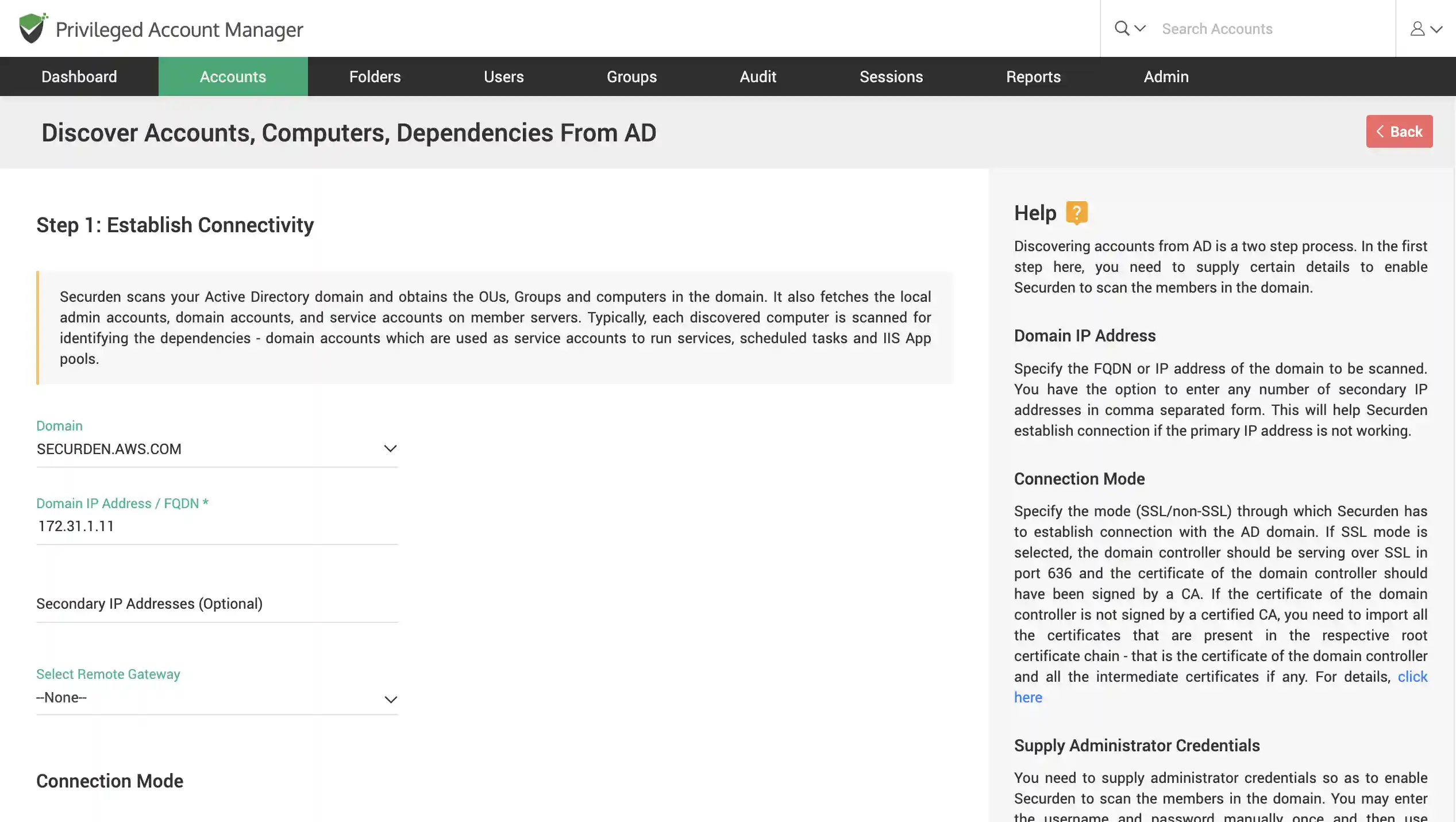
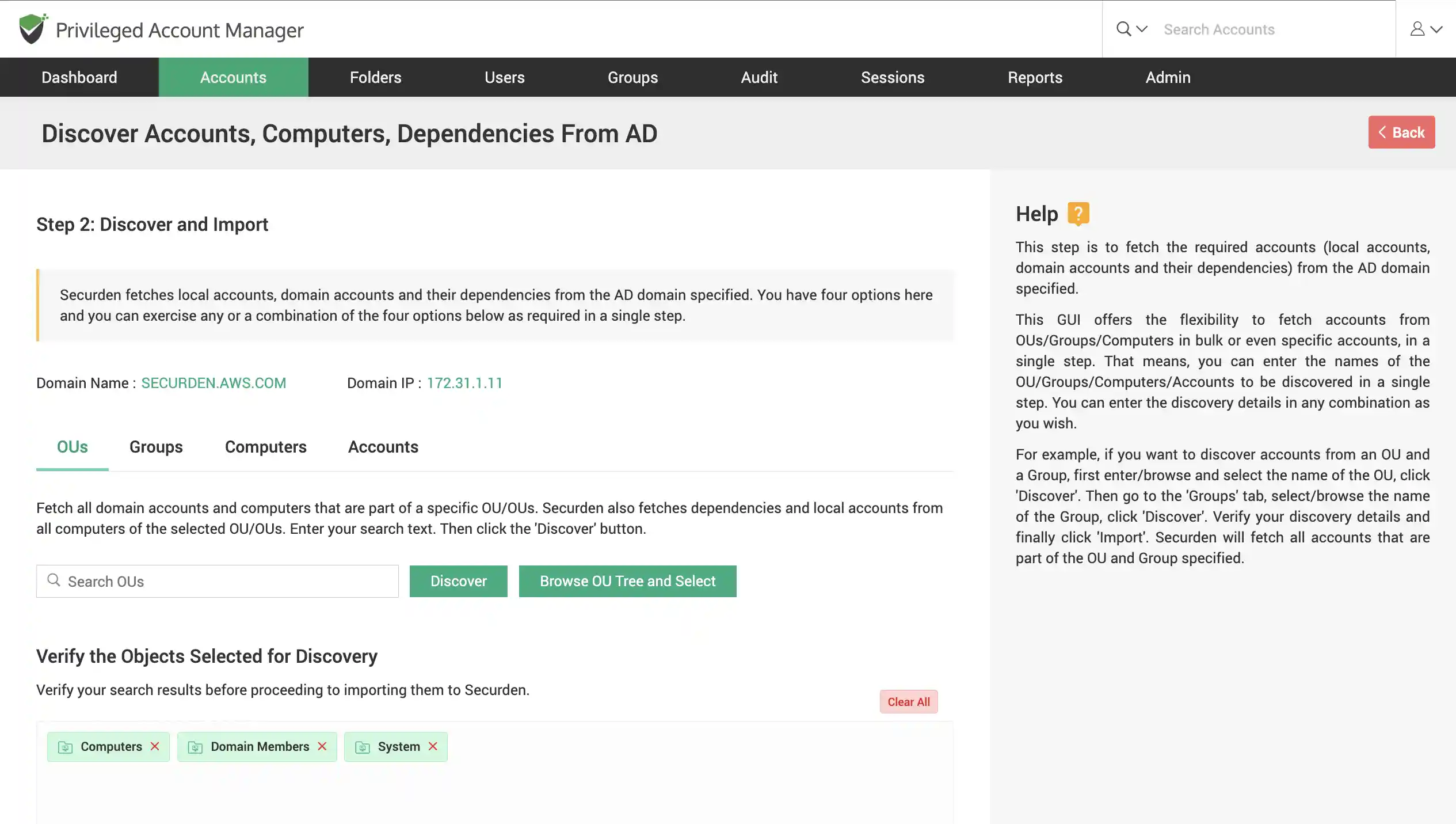
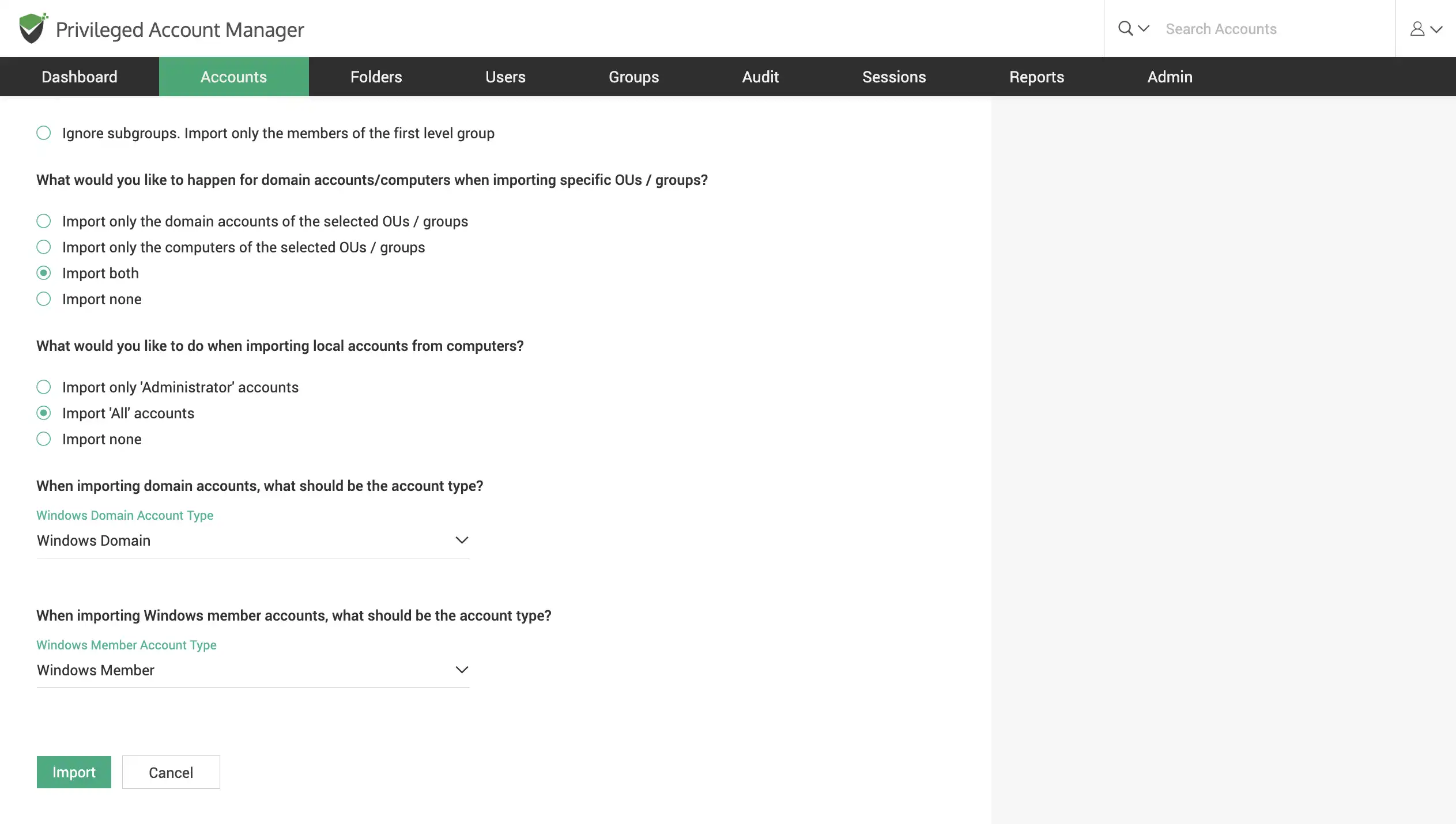
Discover Windows devices and assets
Scan your network to discover windows devices, servers, accounts and dependencies across your IT infrastructure.
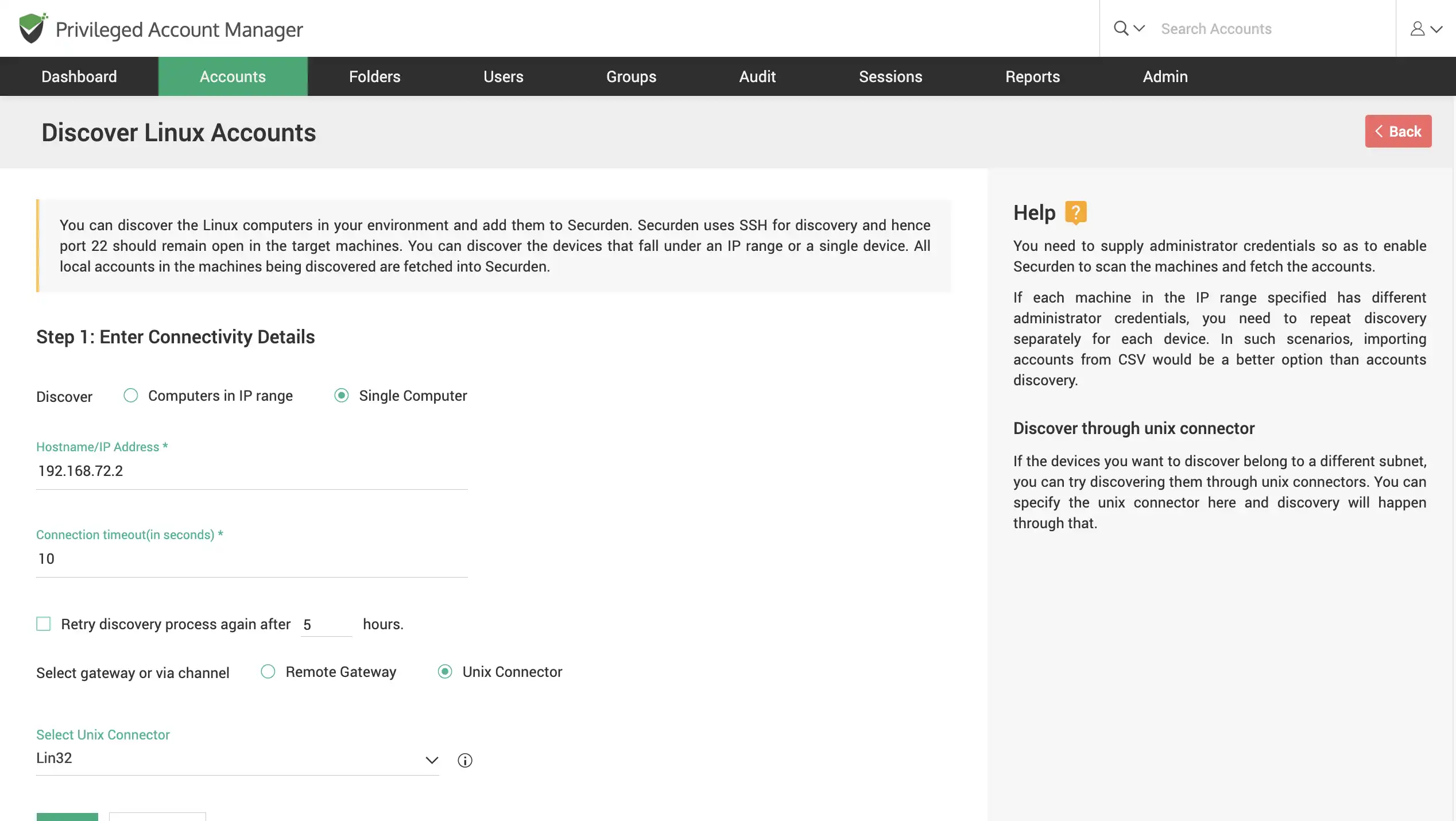
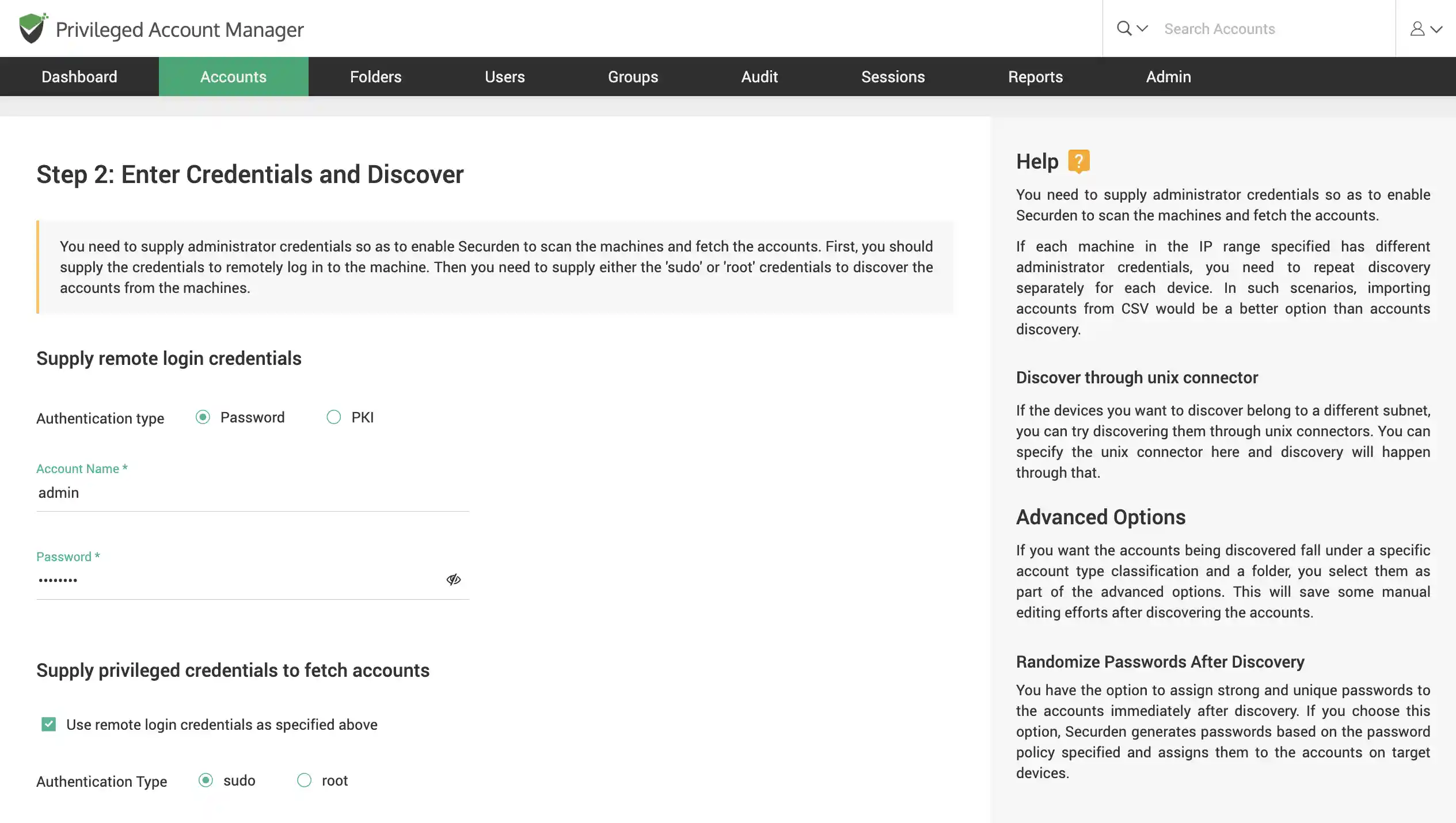
Discover Linux devices
Scan your network to discover Linux accounts using SSH discovery. Find multiple devices that fall under an IP range or find a single device using its IP.
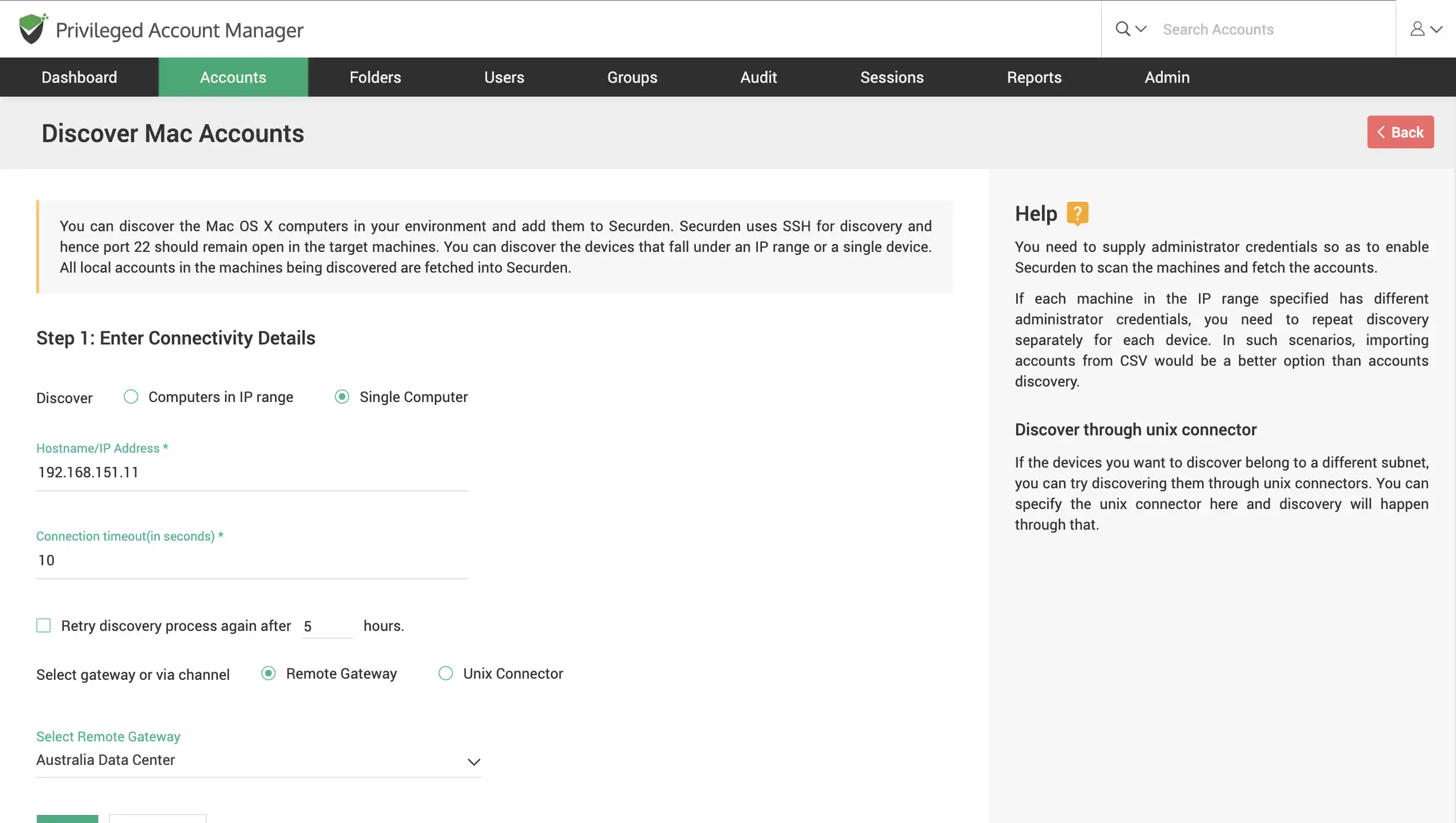
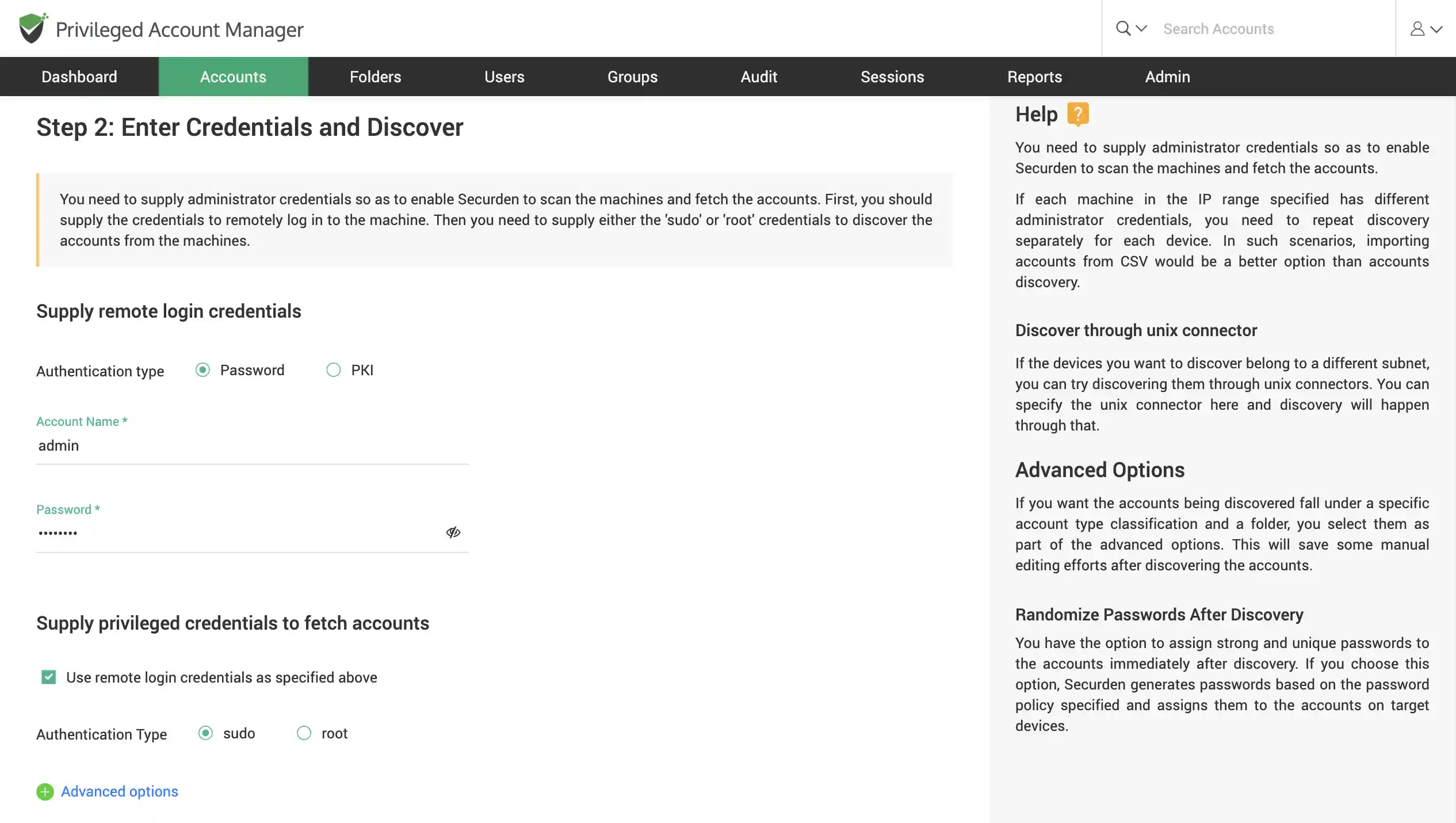
Discover Mac devices
Scan your network to discover Mac OS X devices. Find multiple devices that fall under an IP range or find a single device using its IP.
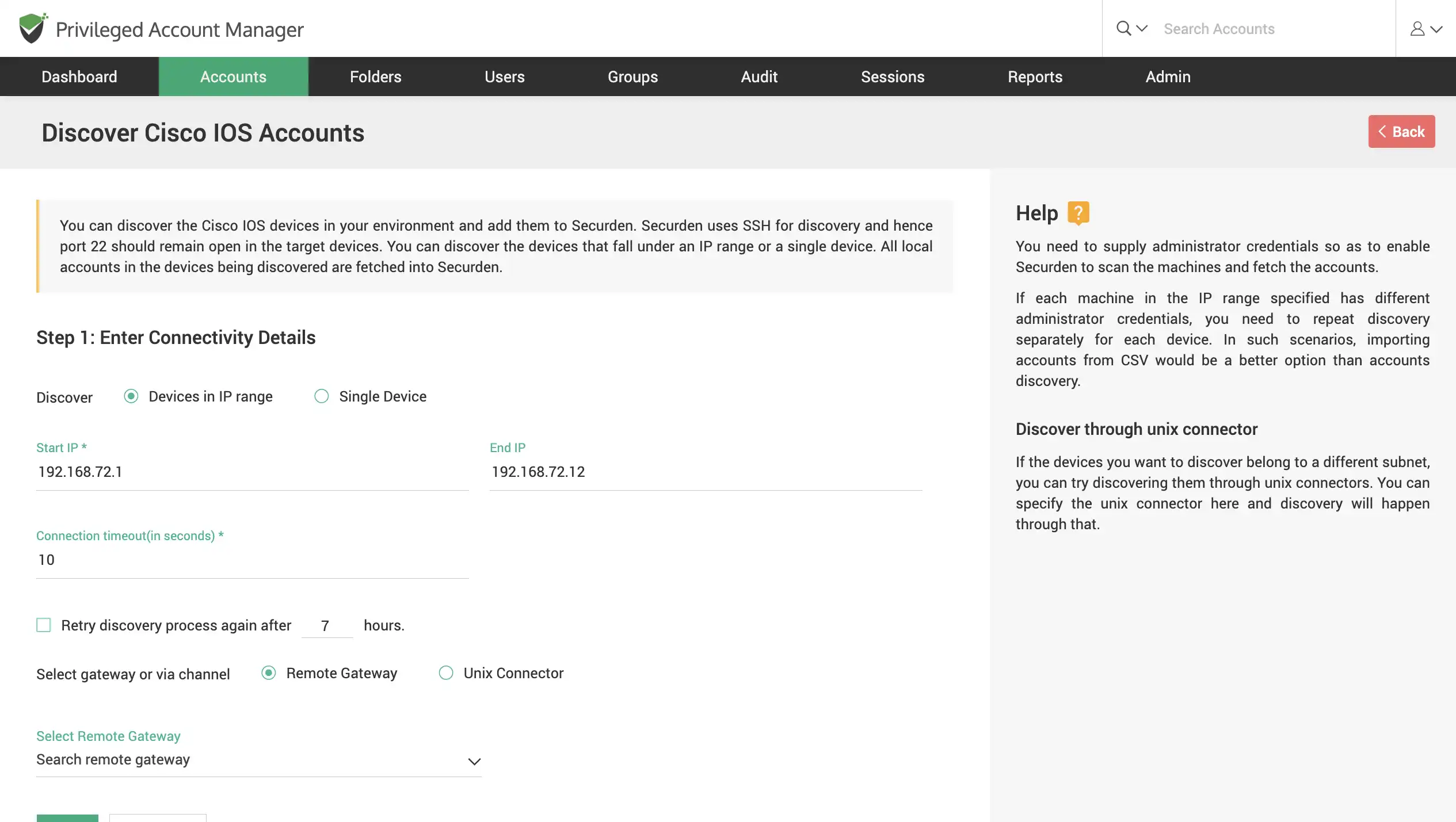
Discover Network devices
Scan your network to discover Cisco IOS devices. Find multiple devices that fall under an IP range or find a single device using its IP.
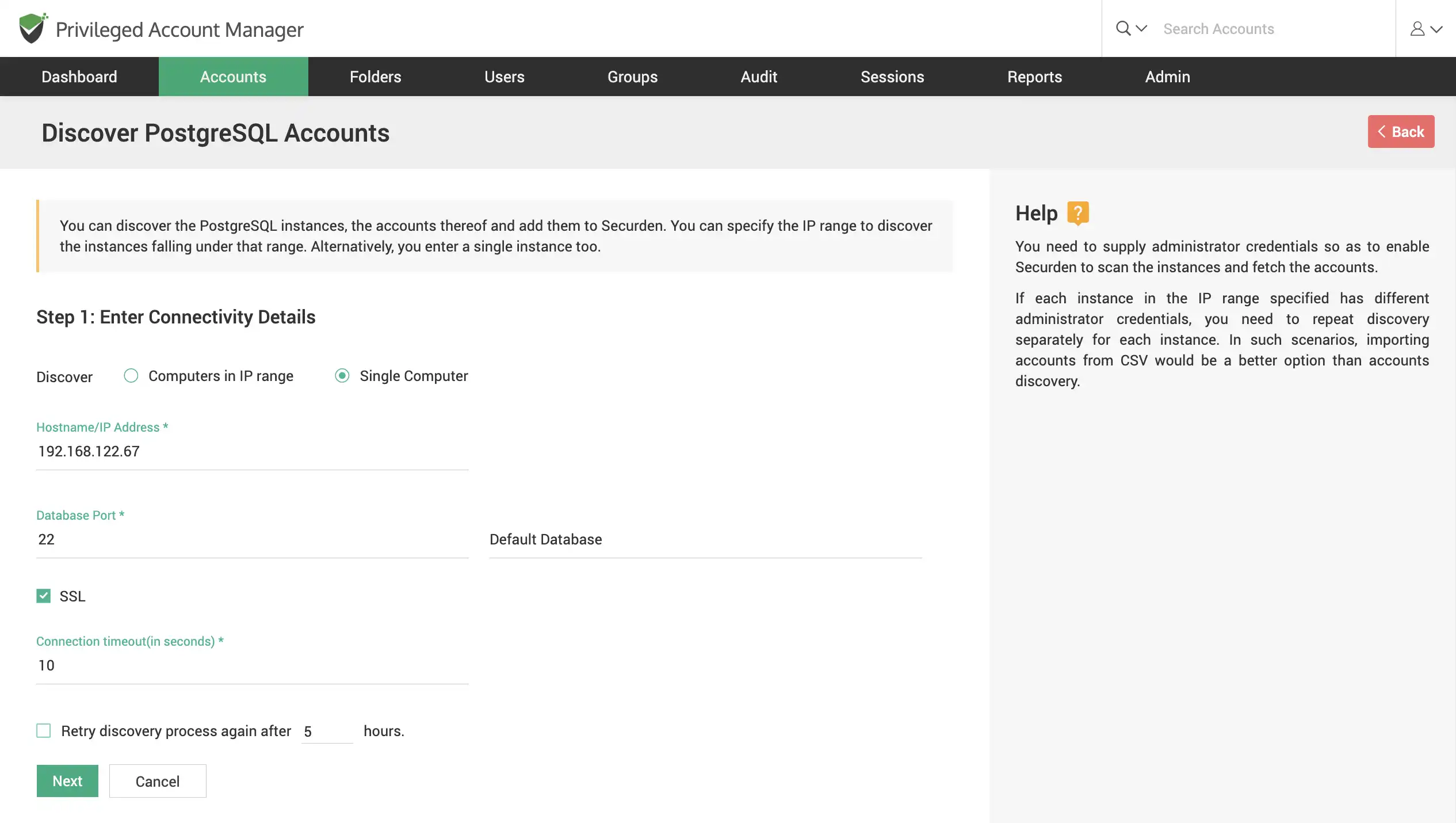
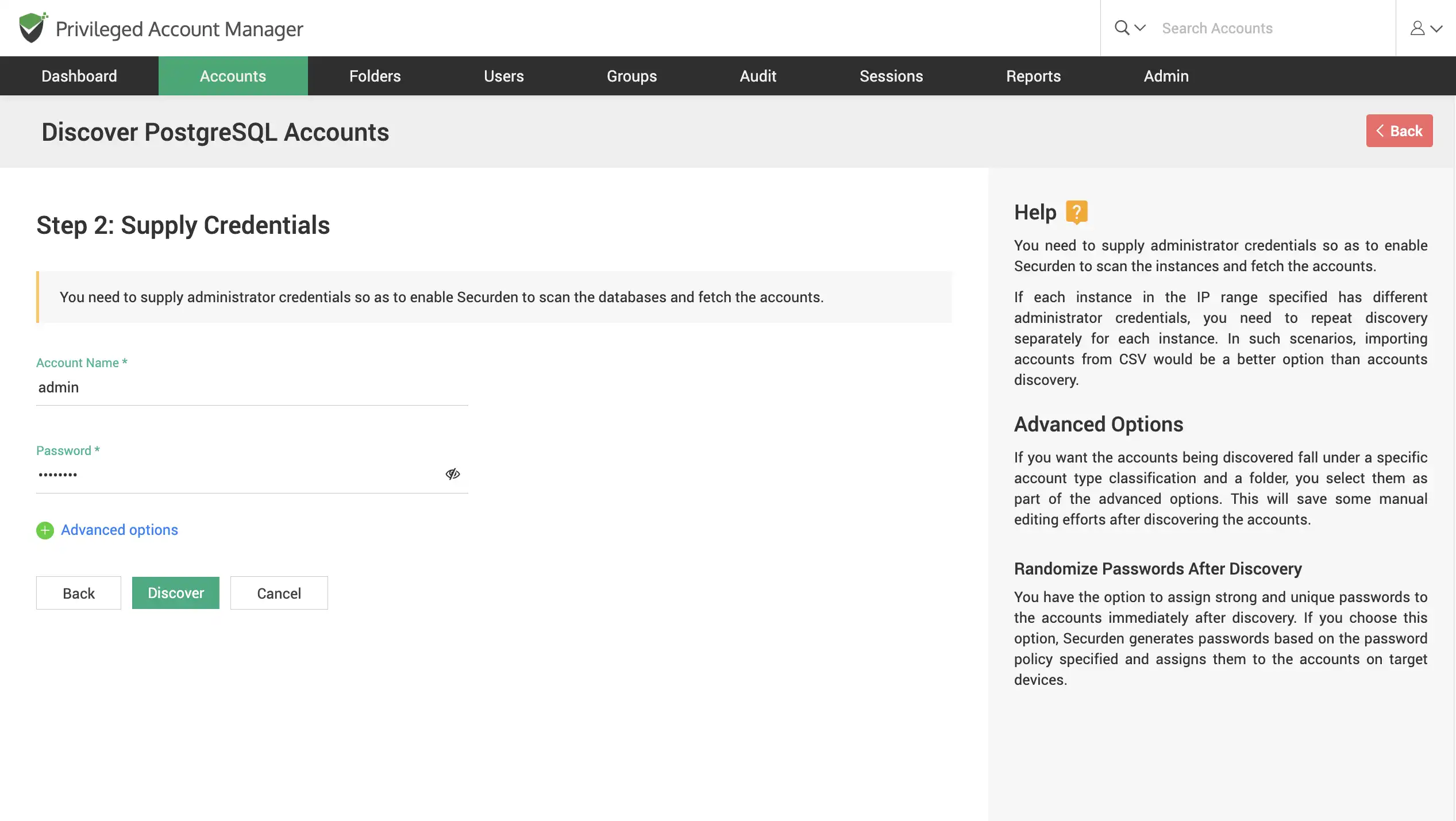
Discover database instances – PostgreSQL, SQL, Oracle, MySQL
Scan your network to discover PostgreSQL, SQL, Oracle and MySQL instances, and the accounts thereof. Find multiple instances that fall under an IP range or find a single instance using its IP.
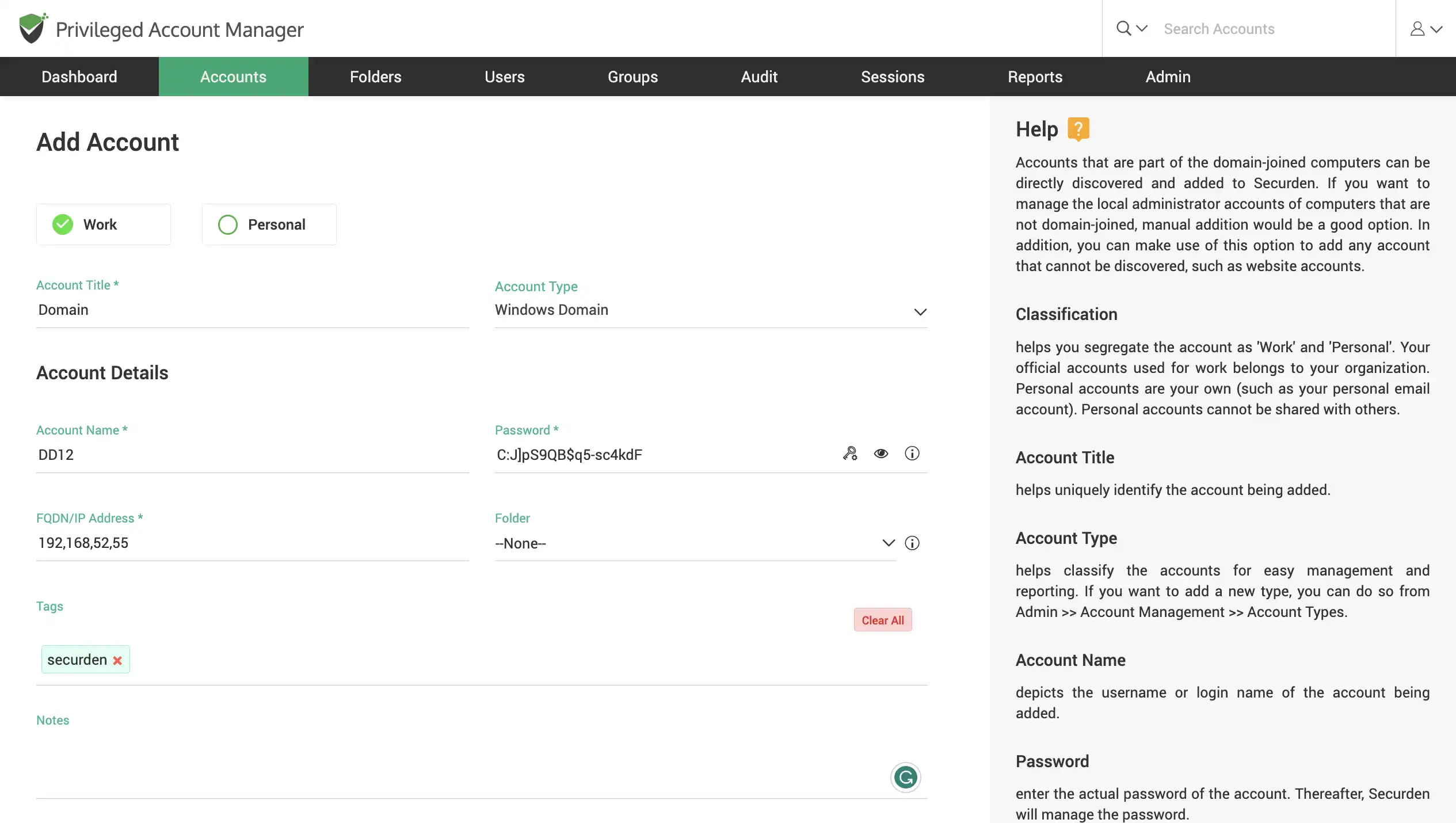
Add accounts manually
You can choose to manually add accounts and manage them through Securden. For accounts you add, generate strong passwords based on a pre-defined password policy. Add tags and notes to your accounts for easy classification.
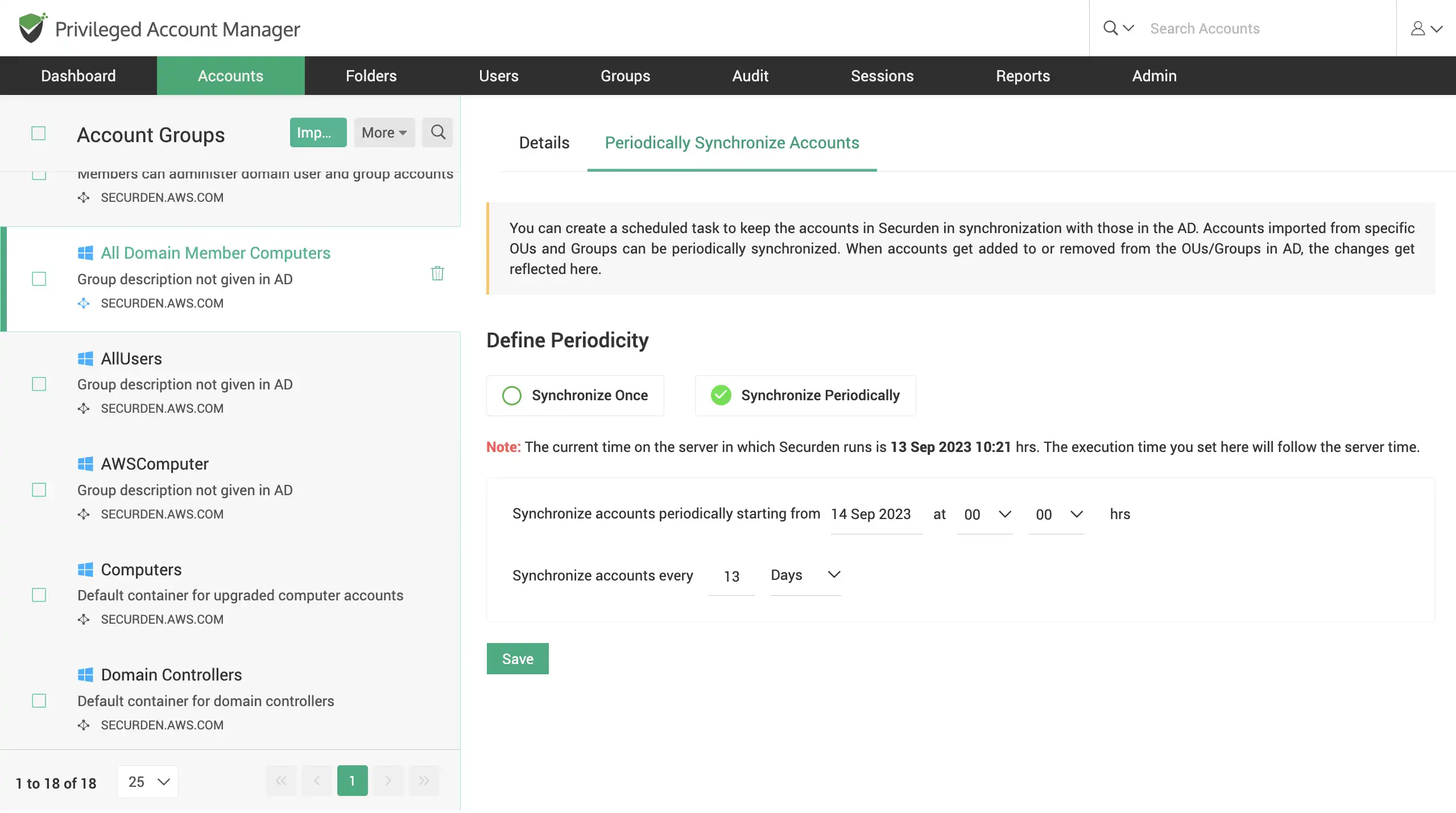
Synchronize with AD/Entra ID (Azure AD)
Once accounts are consolidated, periodically synchronize accounts with your AD. When accounts are added to/removed from OUs/Groups in the AD, the changes are automatically reflected in Securden.
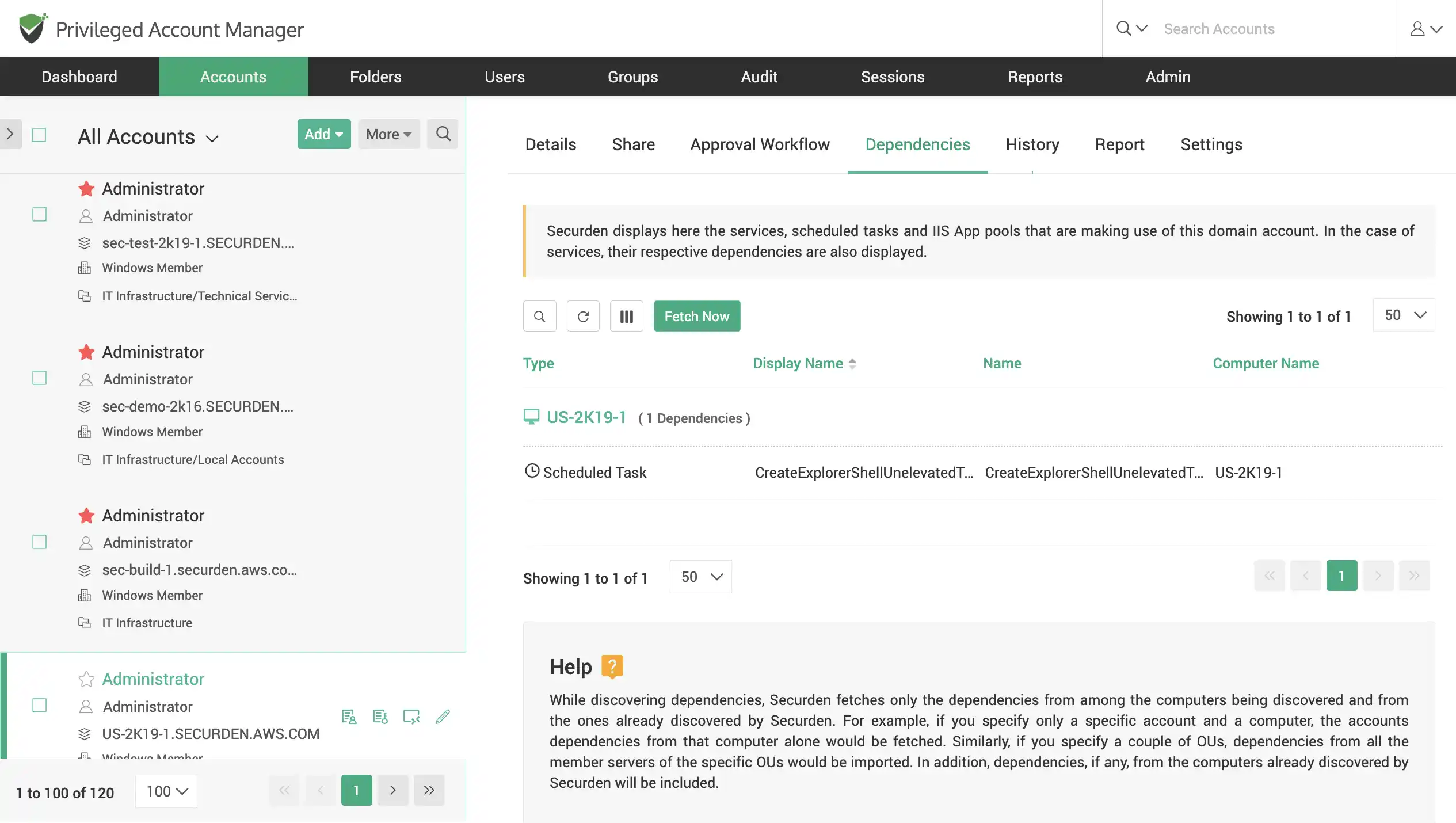
Gain visibility over Windows service and domain accounts, and their dependencies
Fetch and manage highly privileged Windows local, domain, and service accounts that exist in your Windows environment. Propagate password changes to Windows dependencies automatically.
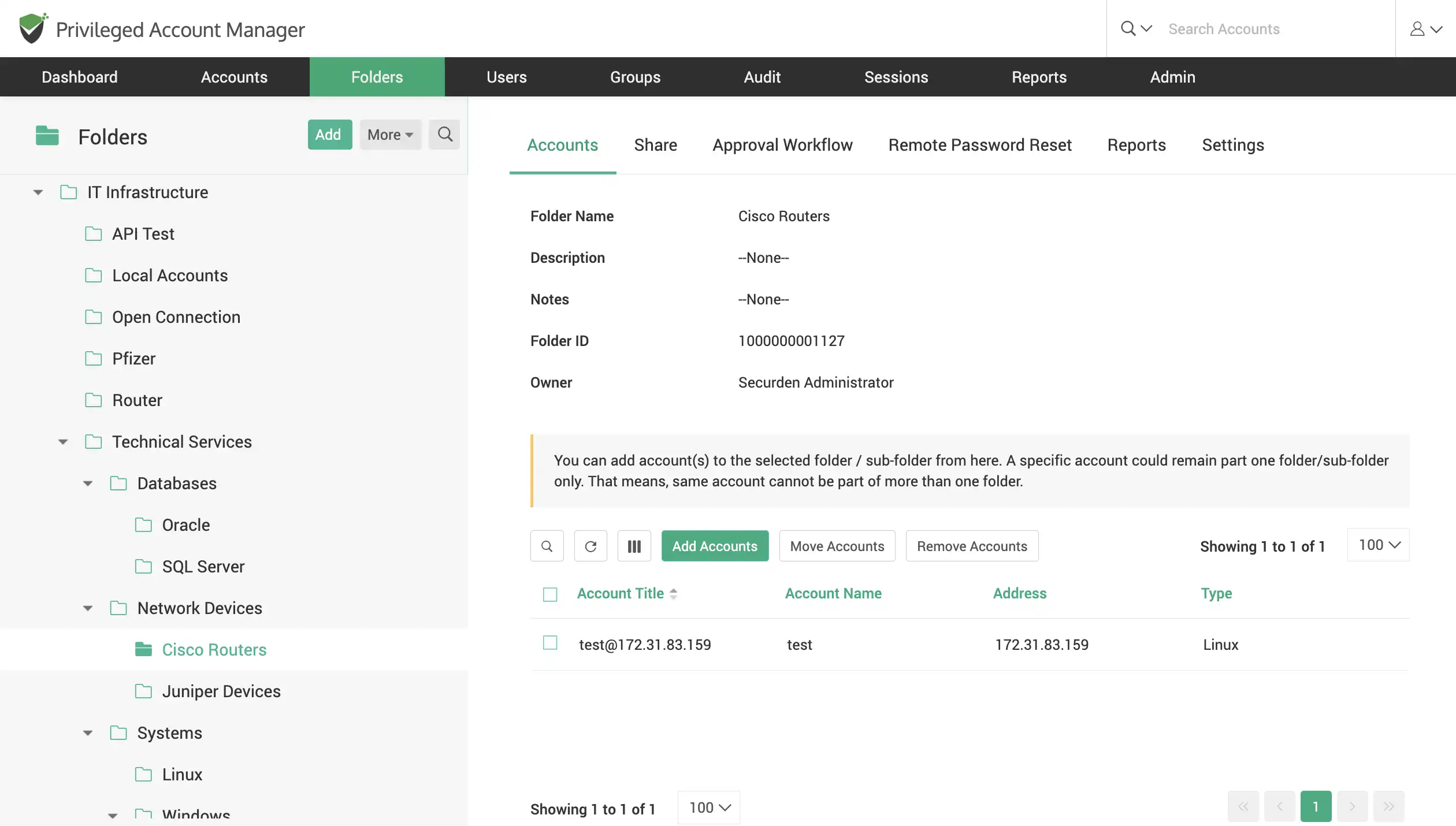
Organize data as folders for bulk management
Group accounts, documents, and other sensitive data together as folders for classification and management. Create folders and subfolders with a hierarchal structure to inherit access permissions based on the parent folder. Carry out critical operations like bulk password change for all accounts in a folder.
Password Management
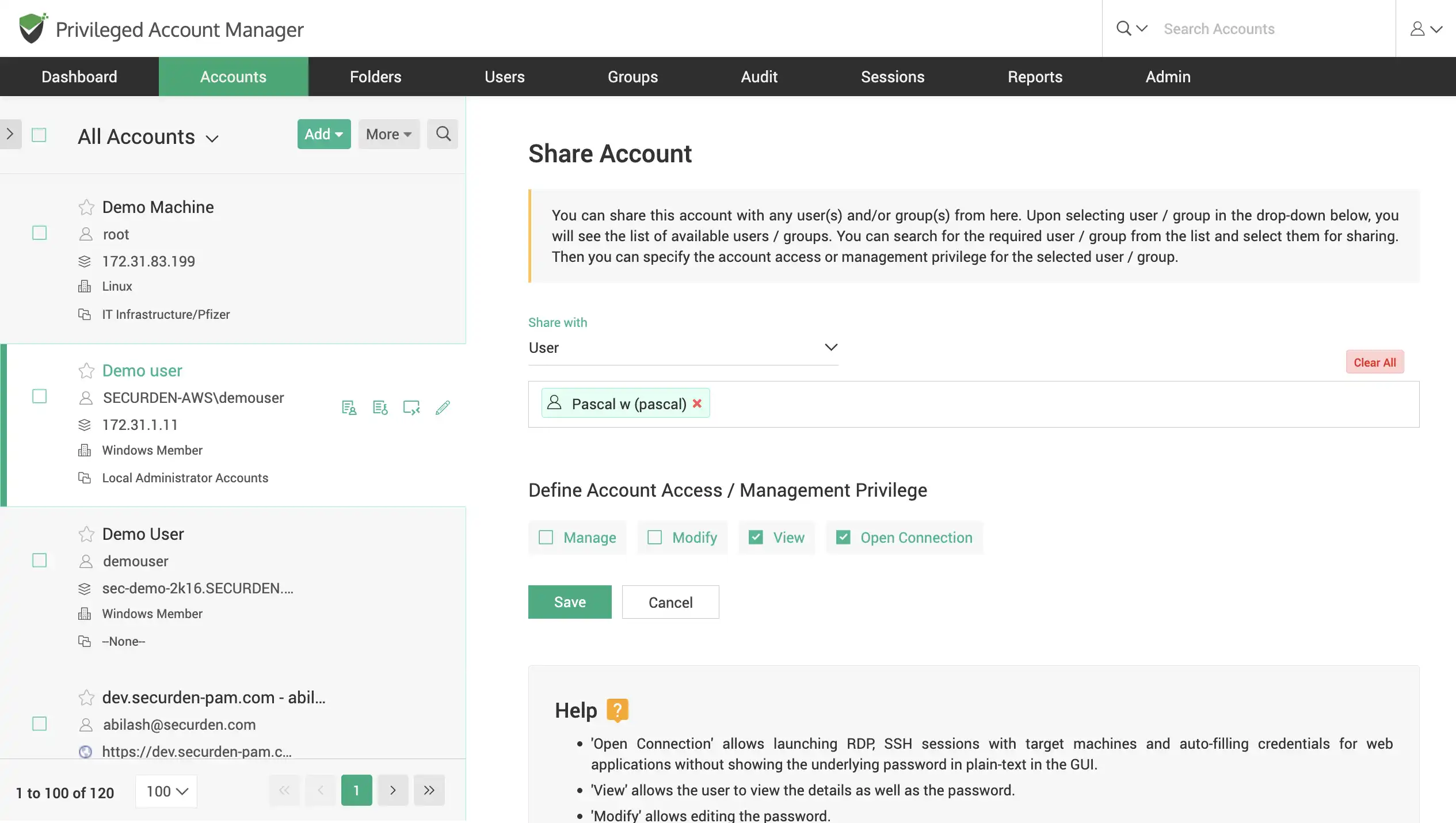
Securely share accounts with the team
Share work accounts with team members/member groups in Securden. Granularly define the level of privilege with which the shared account can be accessed.
Share passwords without revealing them
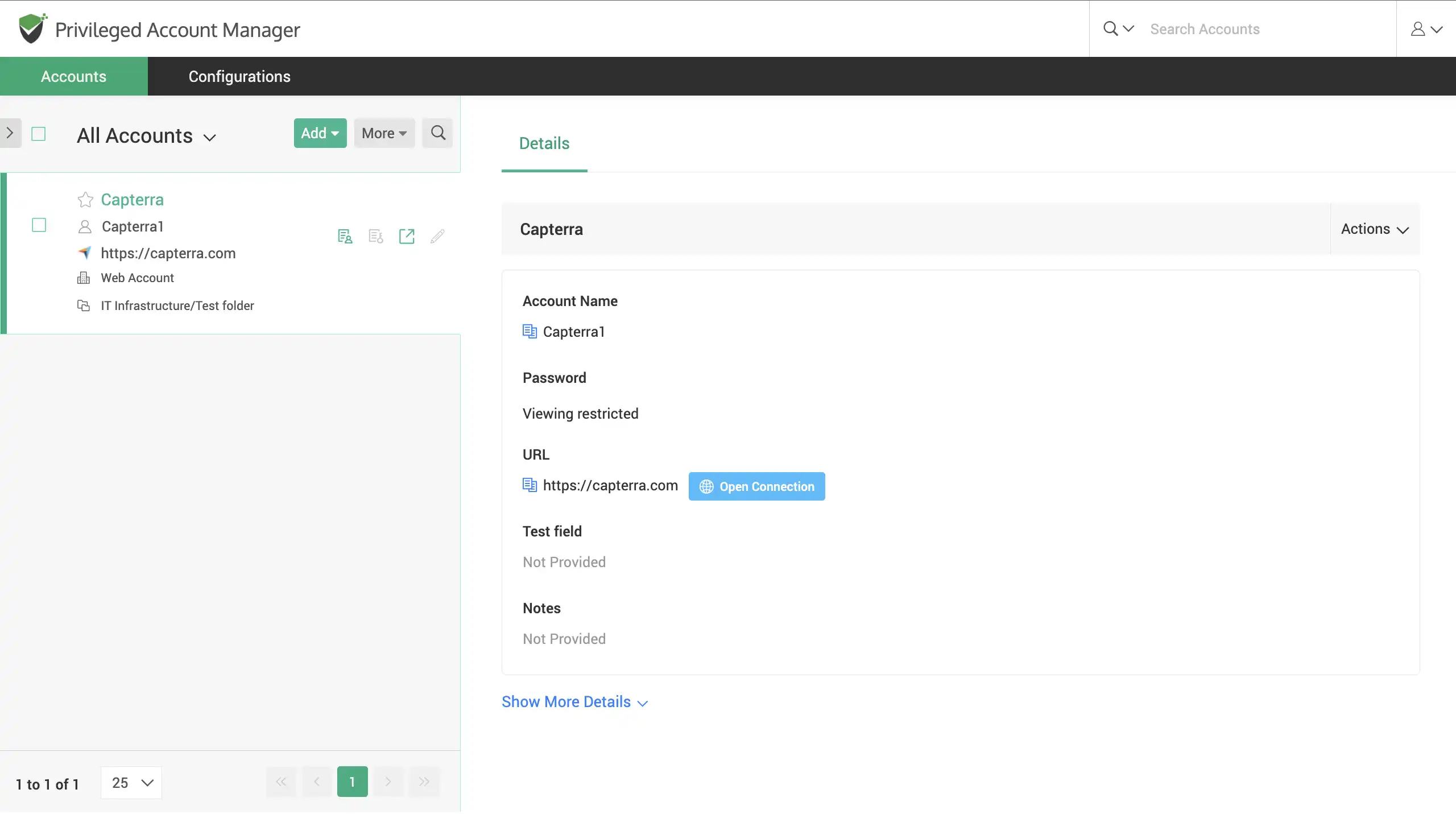
Share accounts with other users while hiding the password from being viewed or copied, allow them to login to websites without knowing the web account password.
Secure remote connections - Allow users to access accounts, target machines and other IT assets by opening an RDP, SSH, SQL connection without showing the underlying password in plain-text.
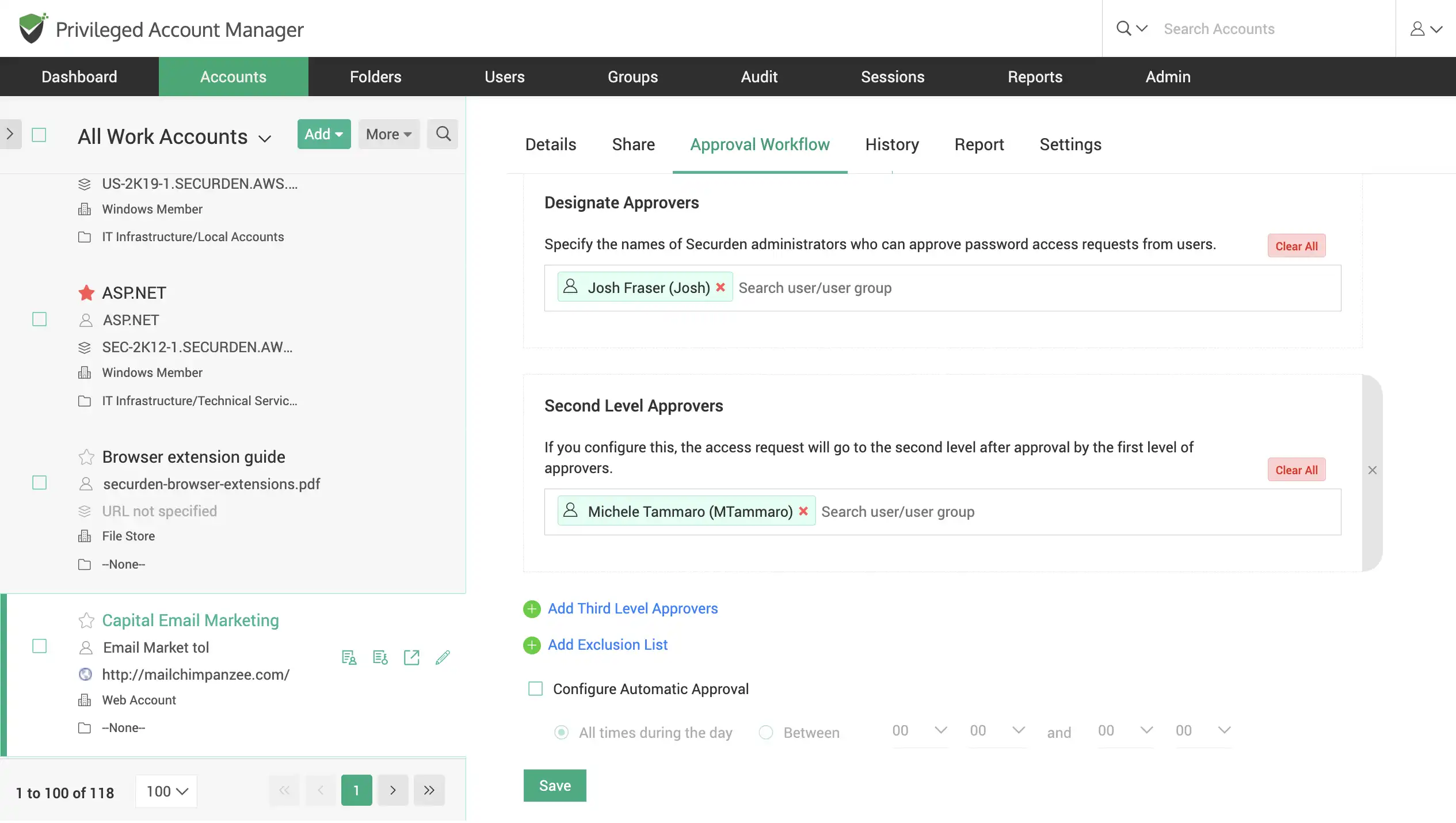
Enforce Just-in-time access with password request-release workflows
Instead of giving permanent access to a privileged account, enforce users to raise requests for time-limited access. One or more administrators will review the request and grant approval. Configure more than one level of approval, and multiple approvers on each level.
On approval, the password will be released. Automatically change passwords at the end of time-limited access.
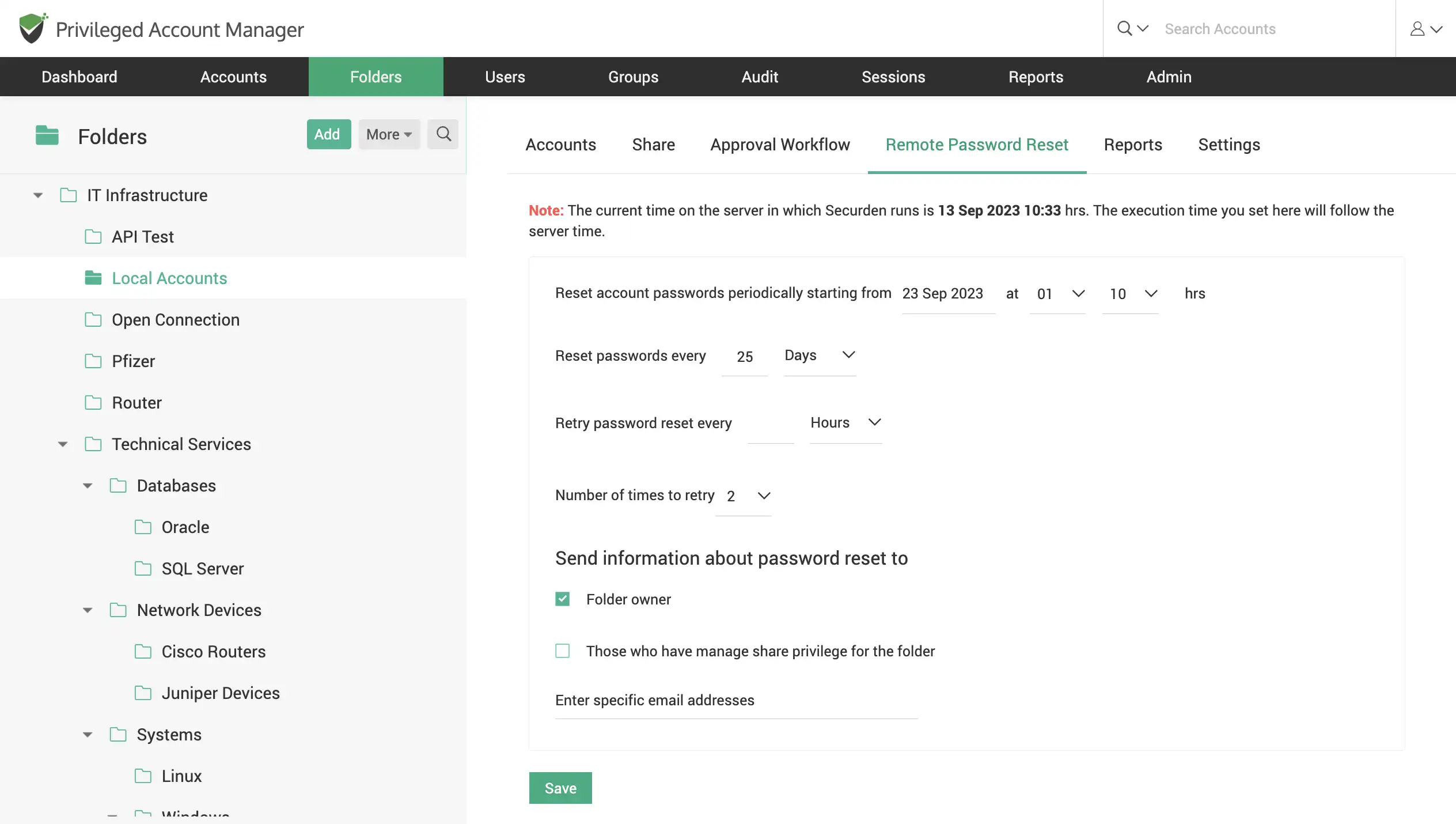
Automate remote password resets
Securden helps you to handle passwords for all types of accounts efficiently. It encourages strong, unique passwords that are rotated on a regular basis. It saves all passwords in a centralized vault so that users don't have to remember them all and can quickly access them when needed.
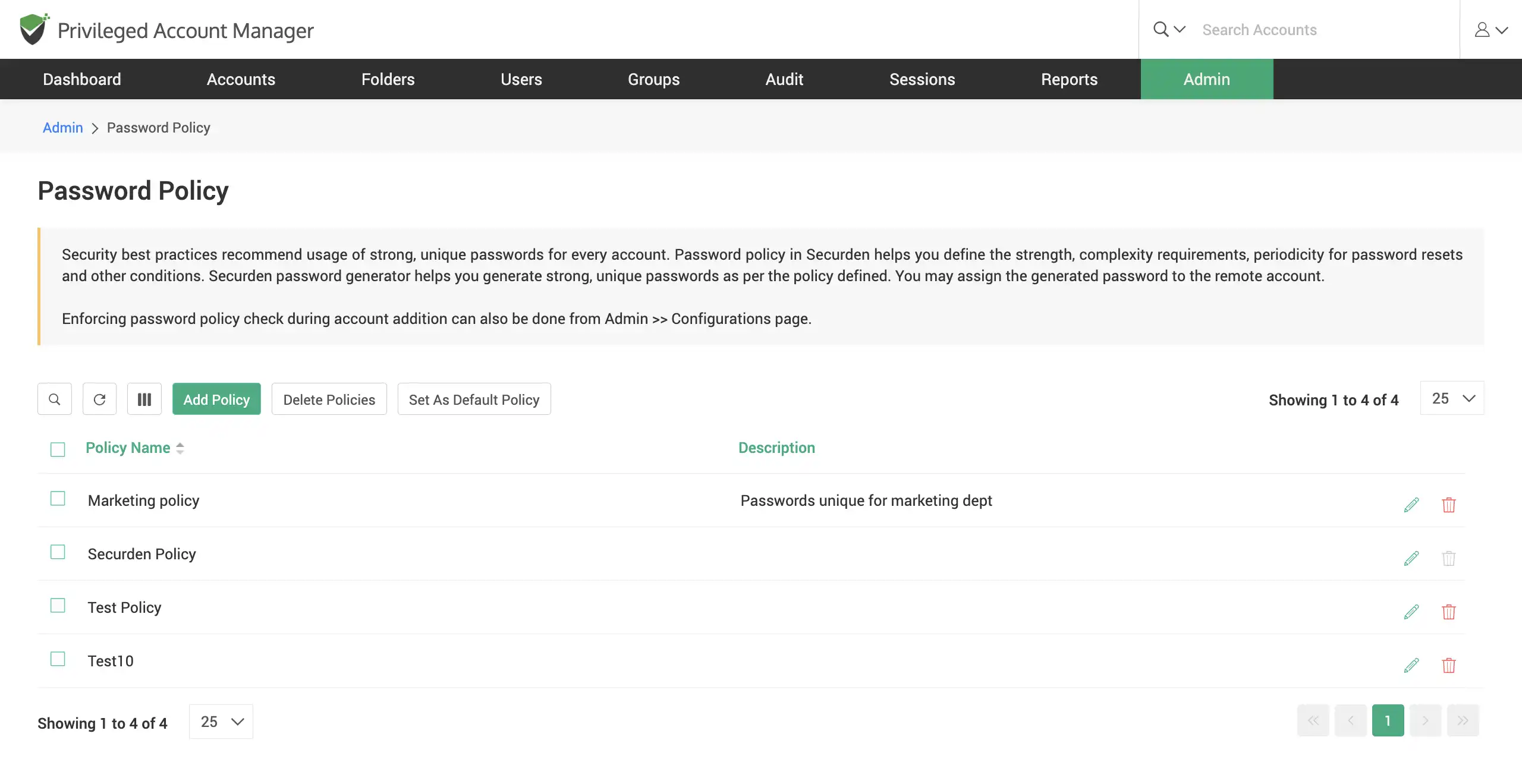
Define password policies
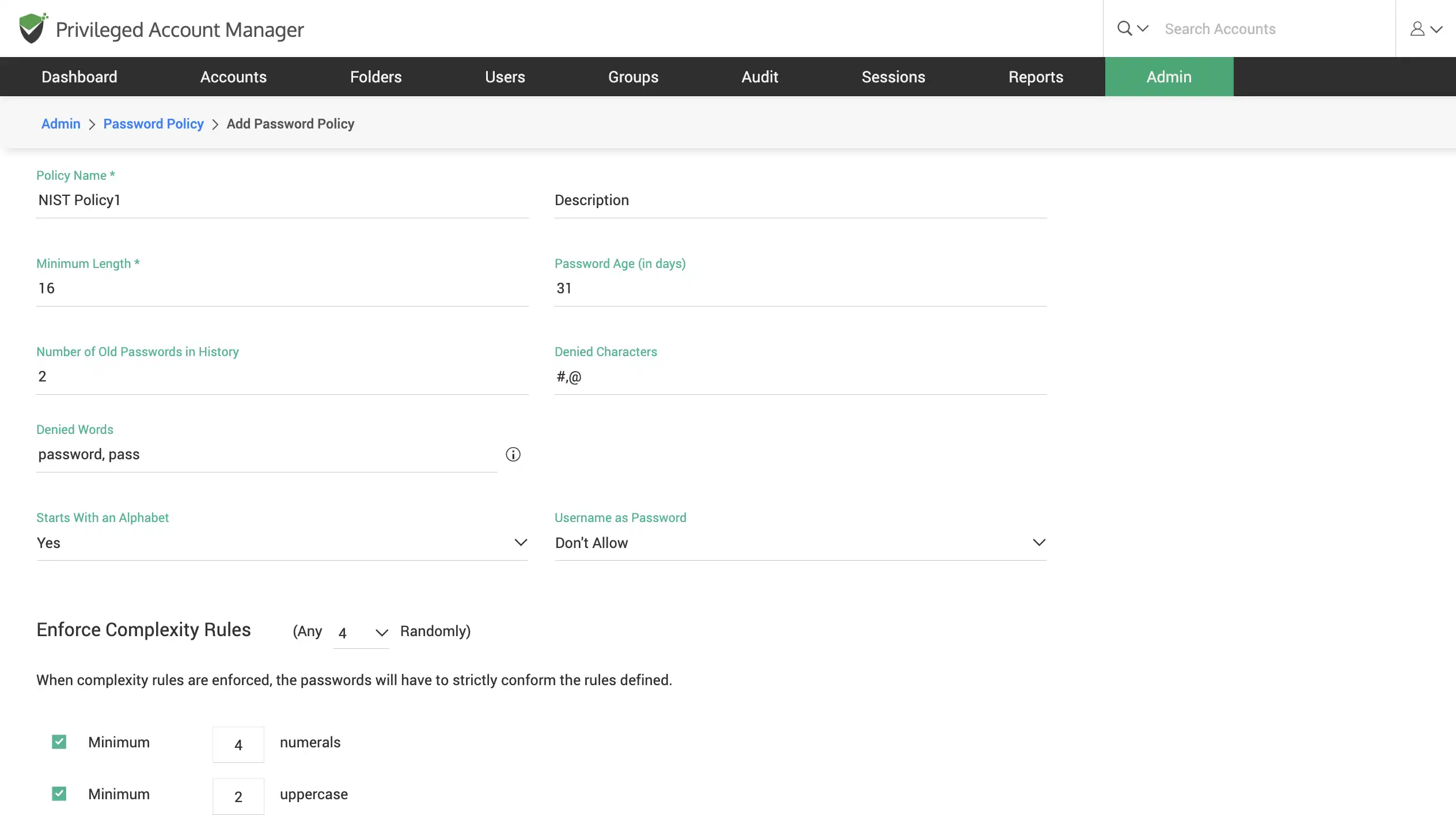
Create password policies to enforce complex passwords across all accounts in Securden. Build password difficulty requirements with customizable parameters such as frequency, length, repeating characters, and so on. Different policies can be created and assigned to different accounts. Securden will automatically enforce these password policies for your organization.
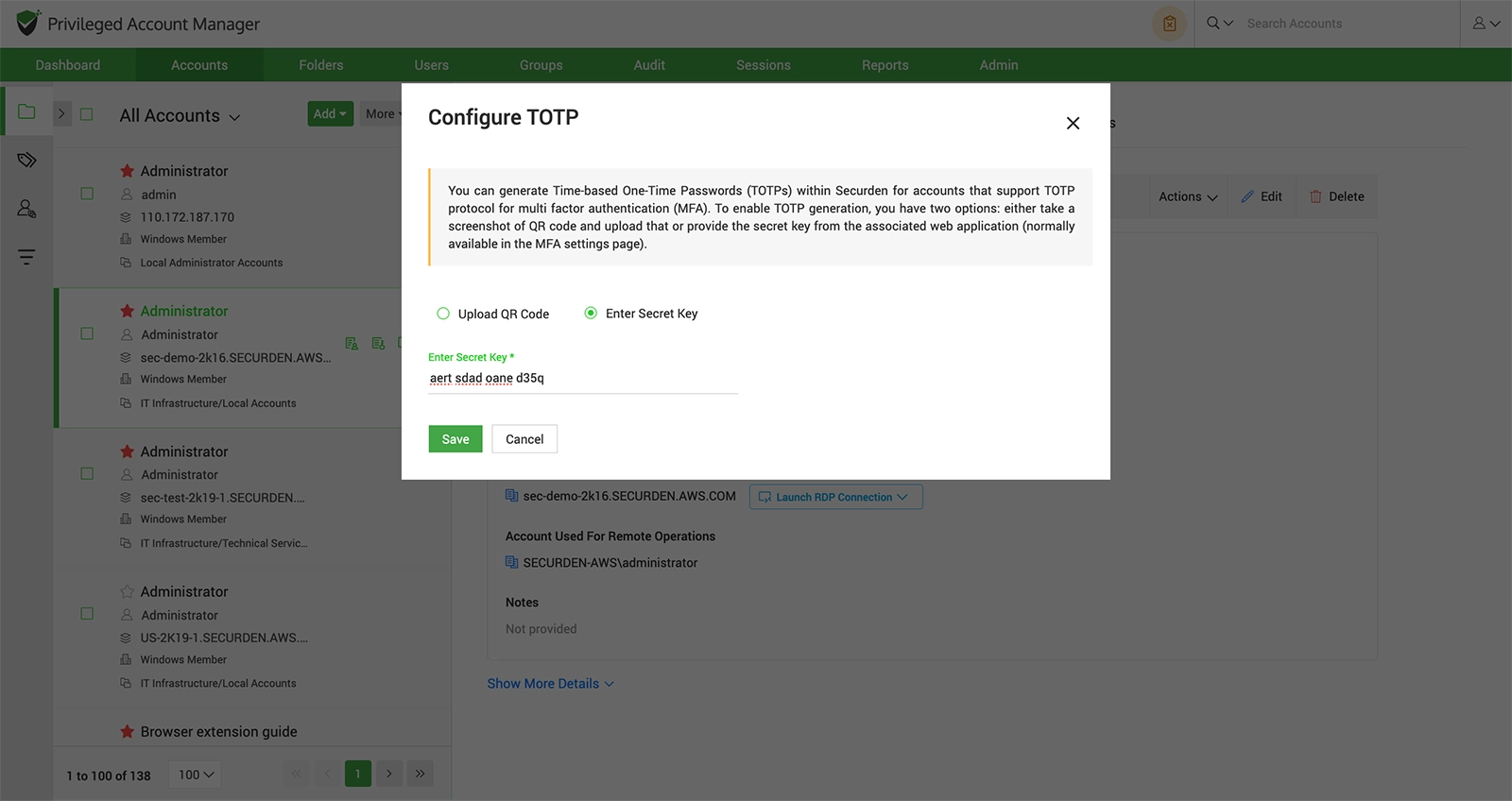
Configure Time-based One-Time Passwords (TOTPs)
Generate TOTPs for accounts that support TOTP protocol for multi-factor authentication (MFA). You can do this by uploading a screenshot of the QR code, or with the secret key from the associated web application (normally available under the MFA settings).
Remote Access Management
Launch one-click connections to remote assets (RDP, SQL, SSH)
Allow your users to securely launch one-click connections to remote IT assets. Launch RDP, SQL, SSH connections directly from the application.
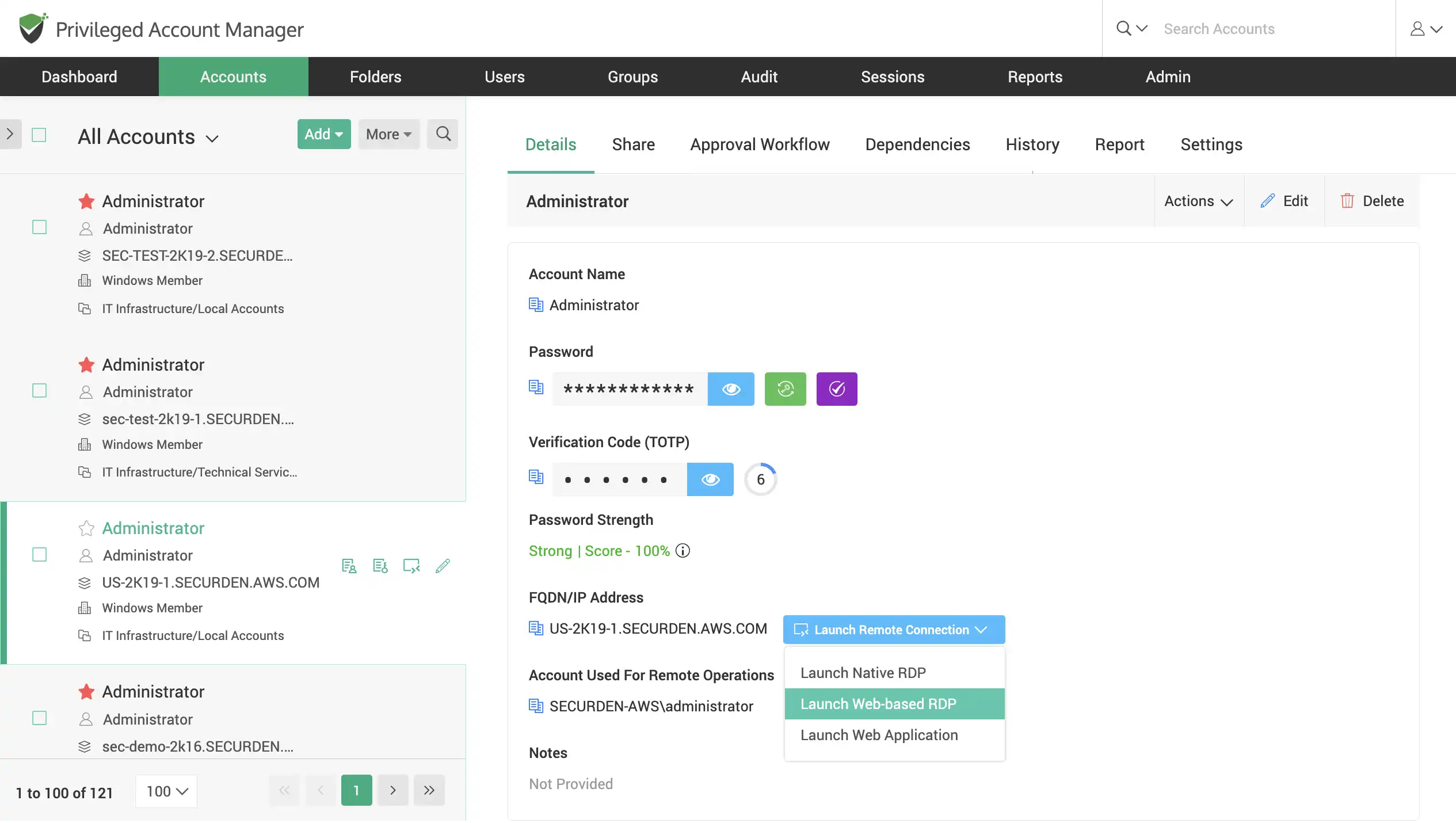
Monitor user sessions live
Shadow sessions launched by users in your organization. Monitor their activity live without their knowledge and terminate sessions if you find any suspicious activity carried out by them.
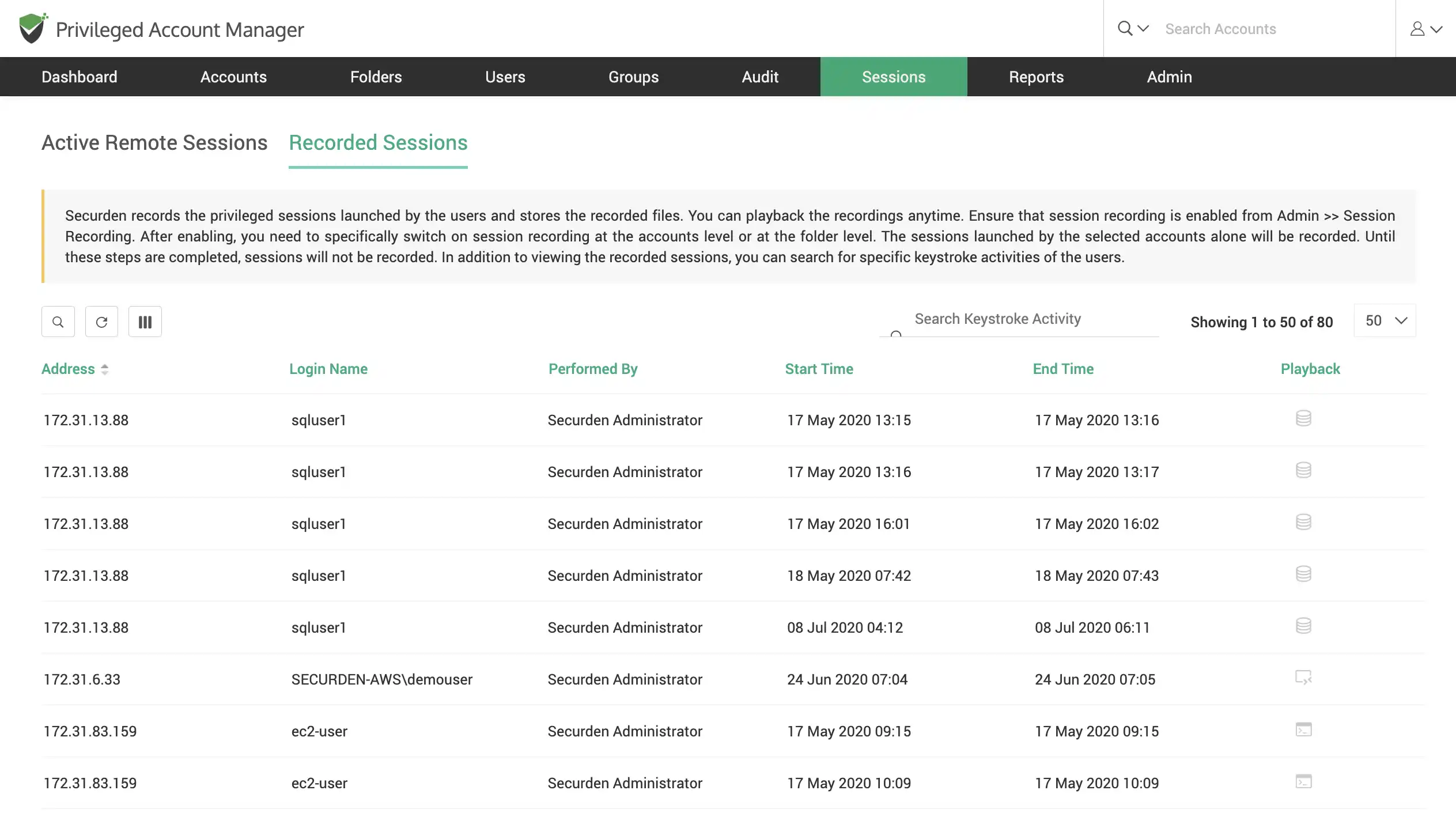
Lightweight session recording capabilities
Store lightweight recordings of all privileged sessions launched by users in your organization. Make use of the comprehensive search to identify keystroke activity and find if any specific commands were used during a session.

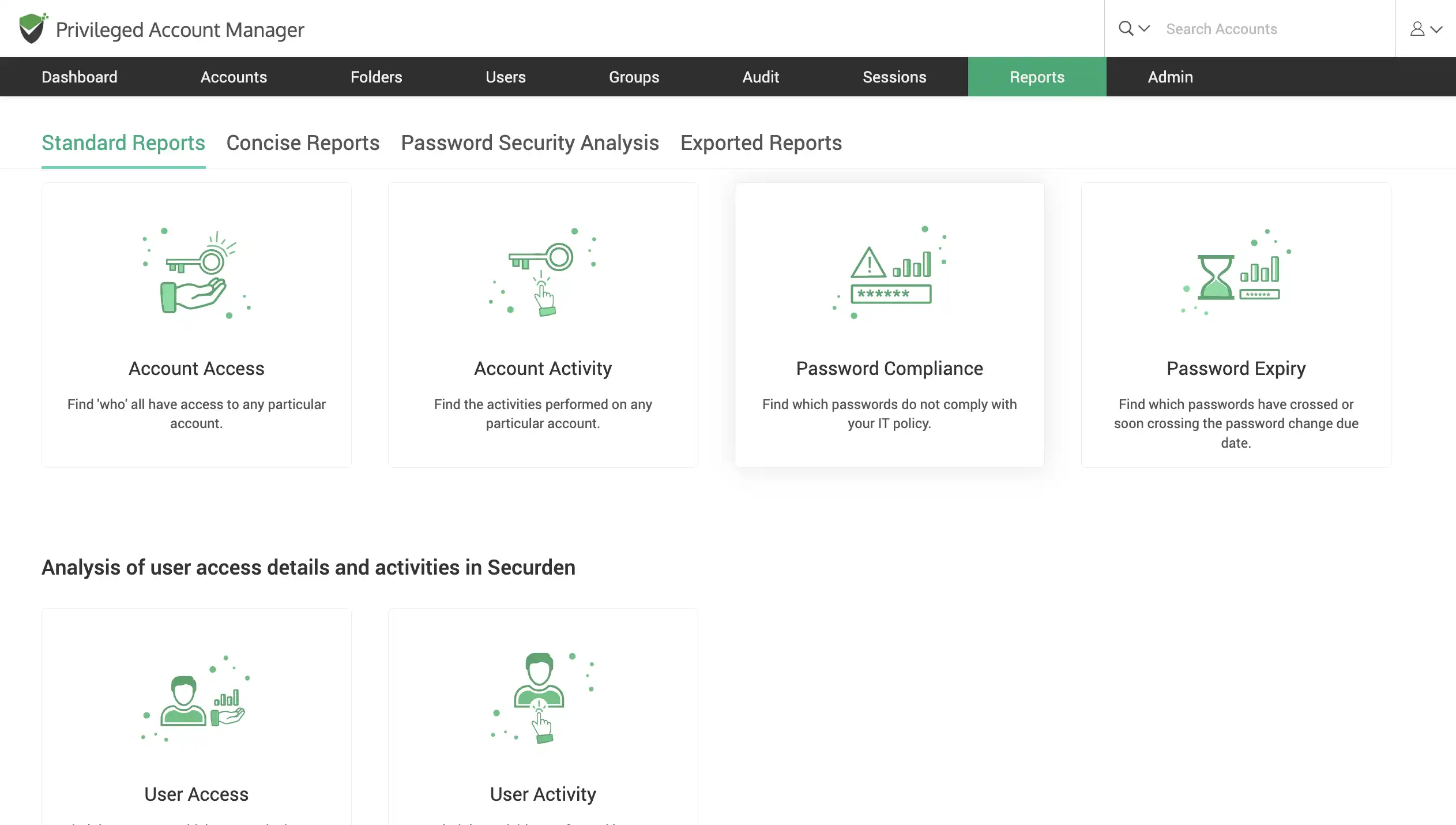
Compliance Reports and Audits
Comprehensive auditing & reporting
Audit and track all privileged access activity. Obtain comprehensive reports on password access, user activity and all privileged account activity to acquire security insights. Generate and export reports on-demand or schedule specific reports to be sent to inbox.
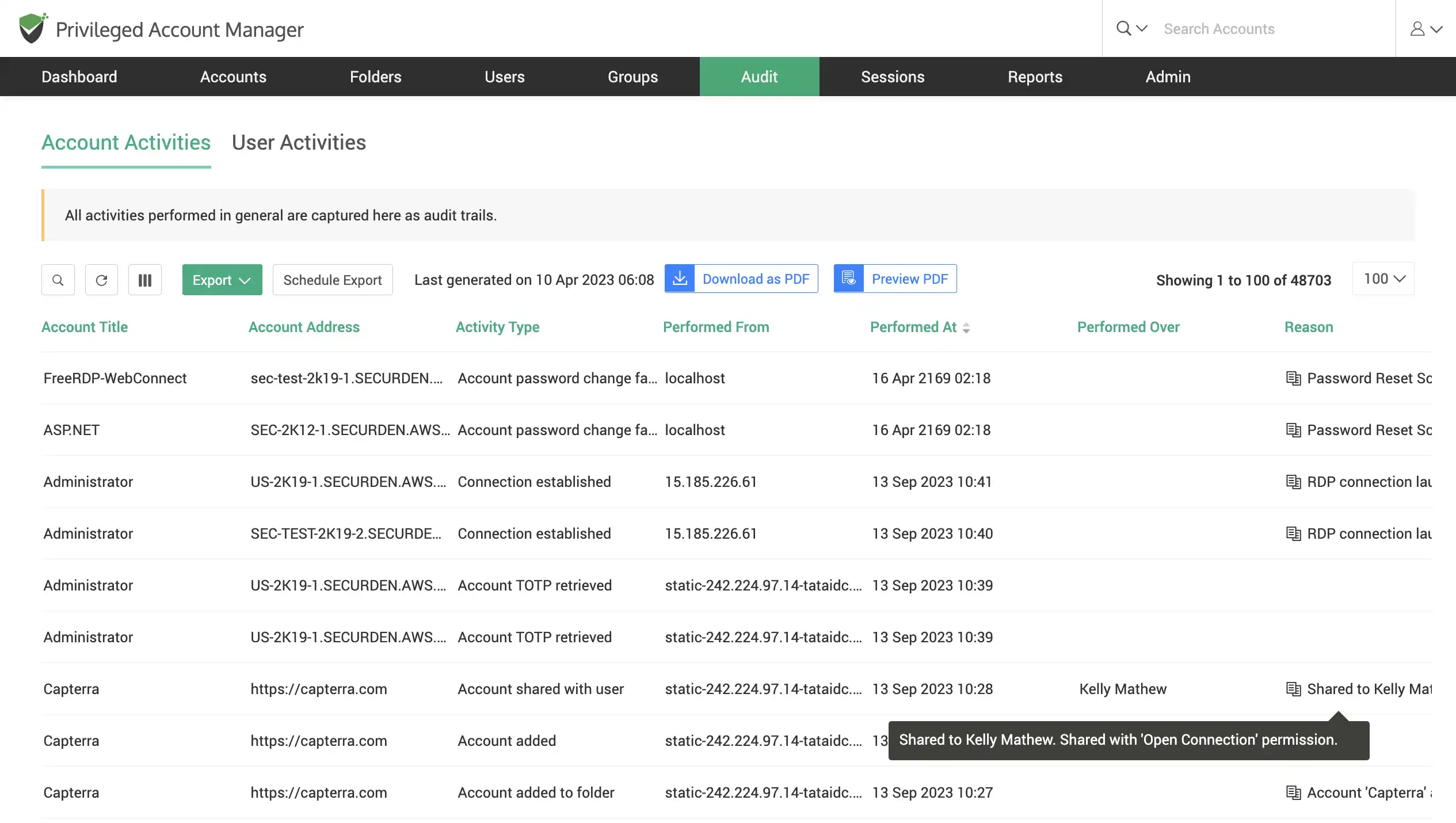
Drill-down on audit trails
Search and gather specific audit activities using searchable text-based trails. Filter data based on text-based or command-based search and export the drilled-down report for further insight.
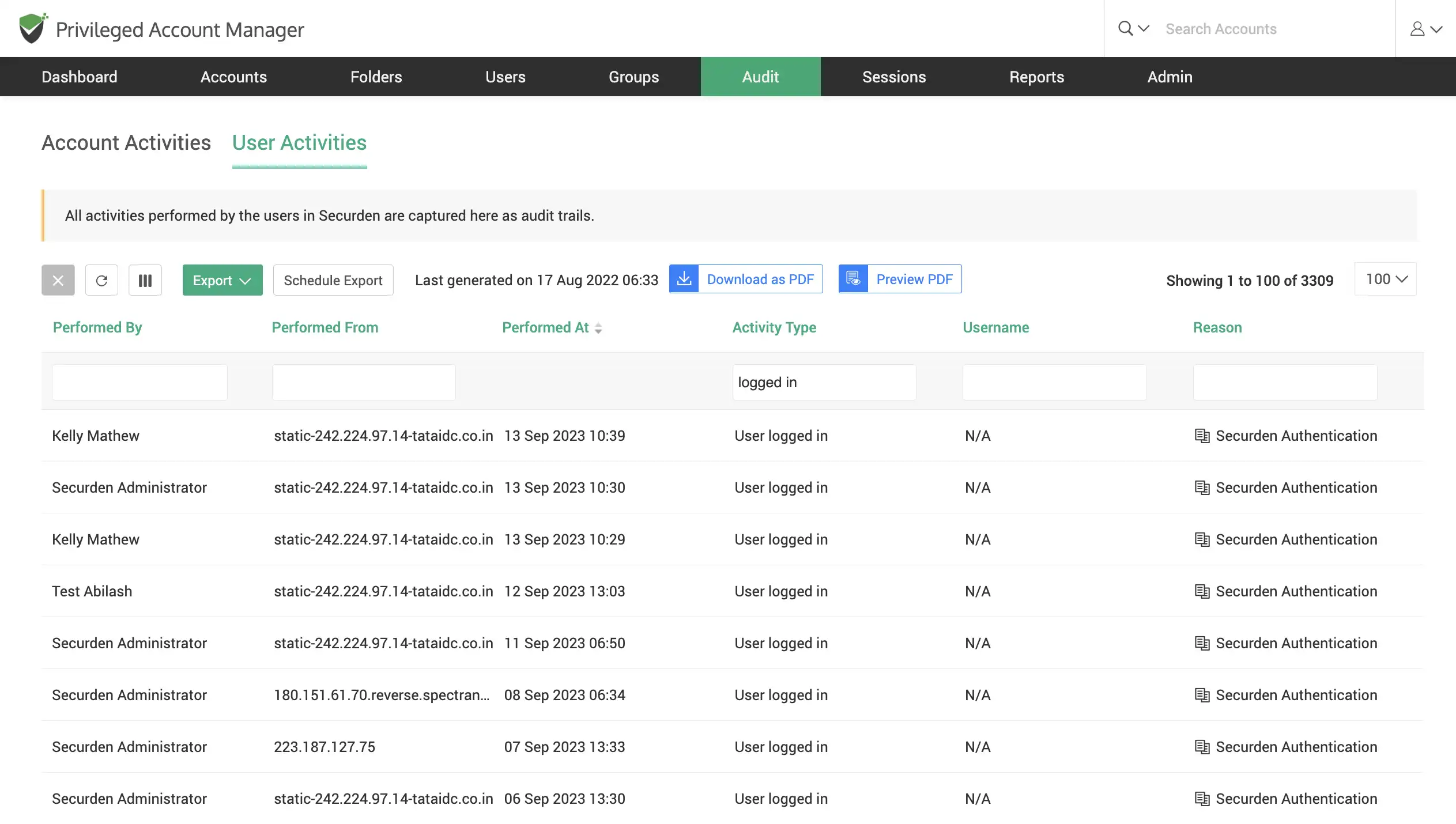
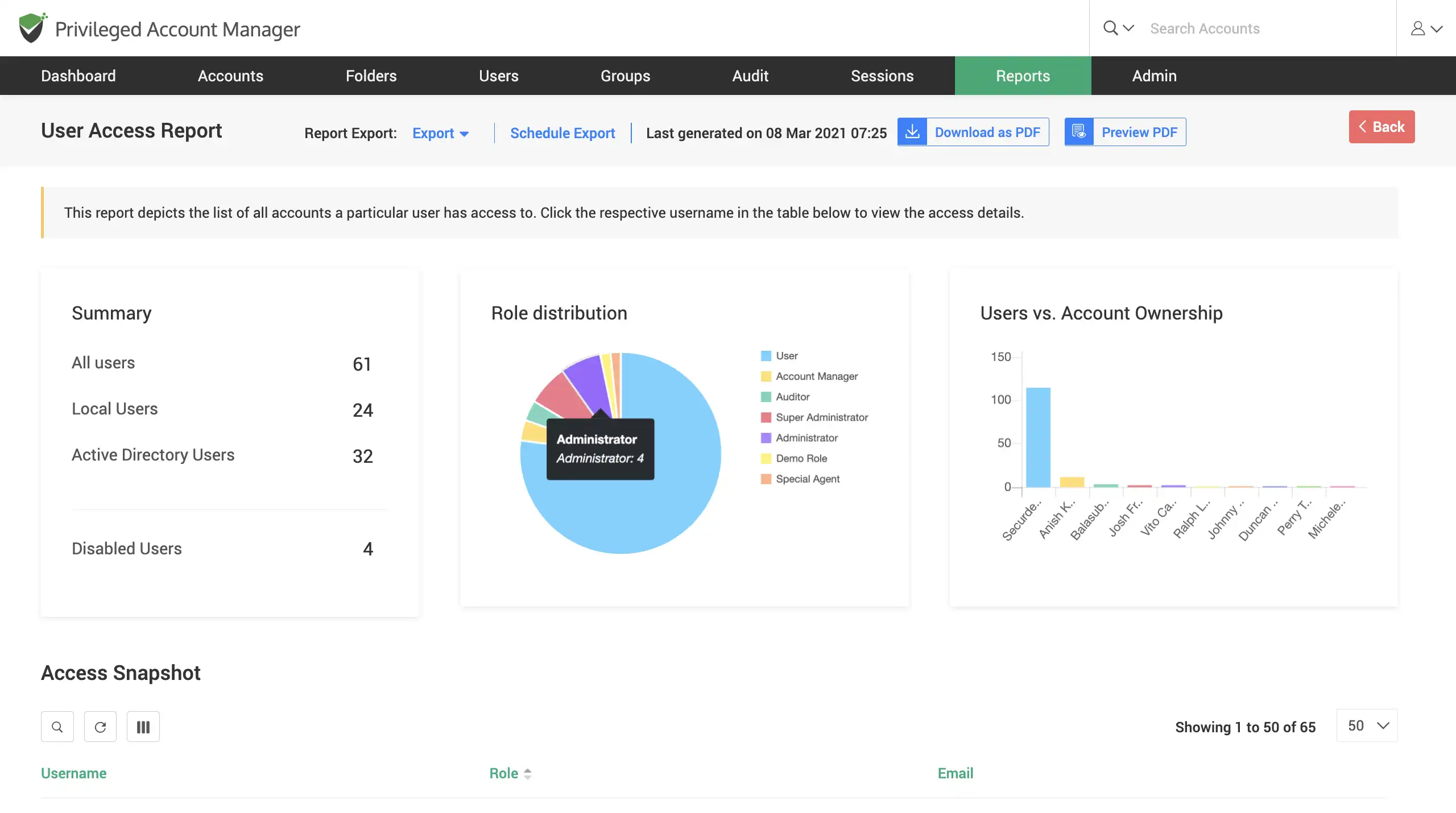
Intuitive user access and activity reports
Gather actionable insights with an overall analysis of user activities based on various parameters. Gain visibility over which users have higher access privileges in Securden.
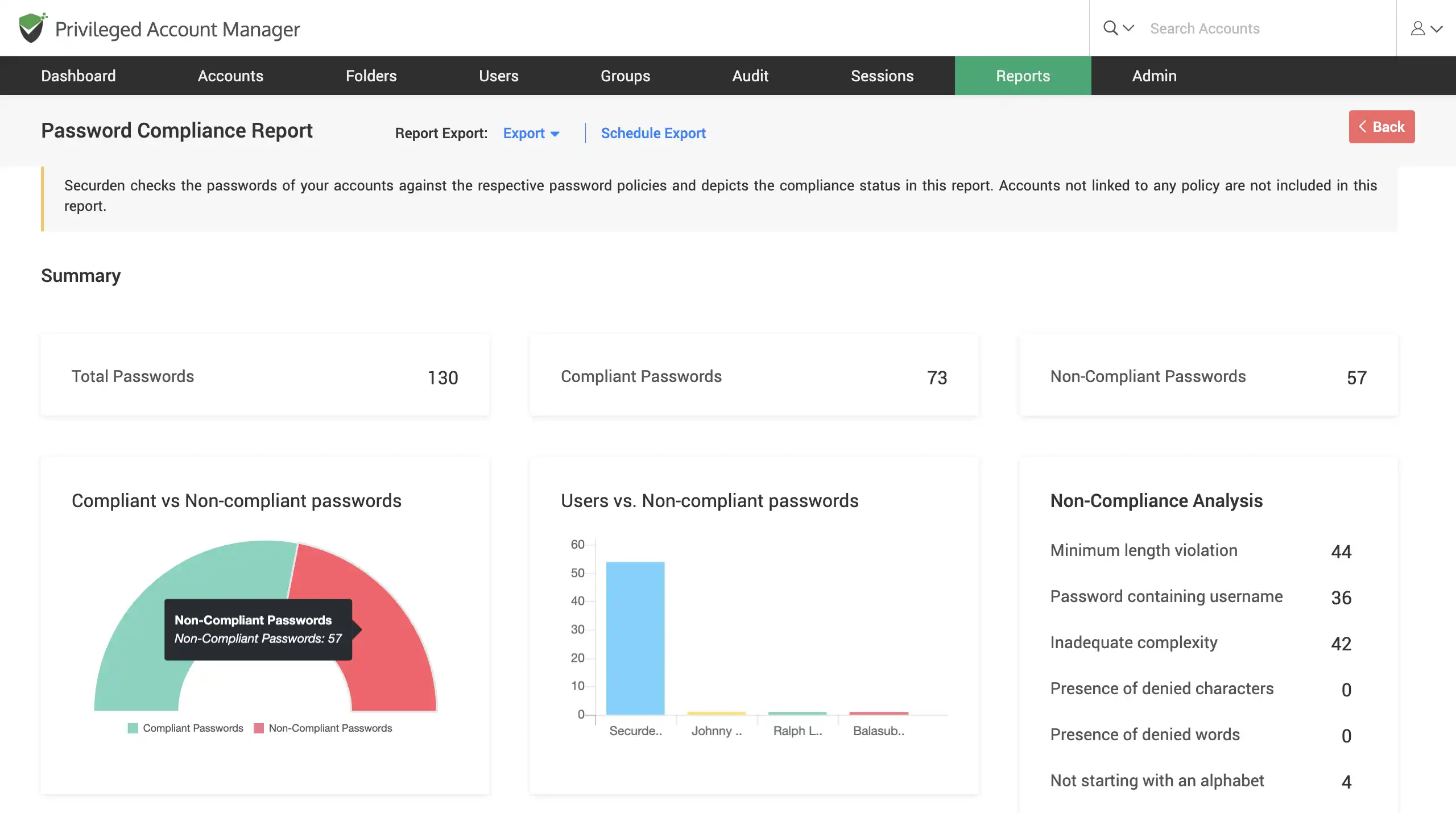
Examine and enforce password compliance
Gain intel on which passwords are not in compliance with your IT password policy. Replace the non-compliant passwords with secure and complex passwords using the Securden password generator.
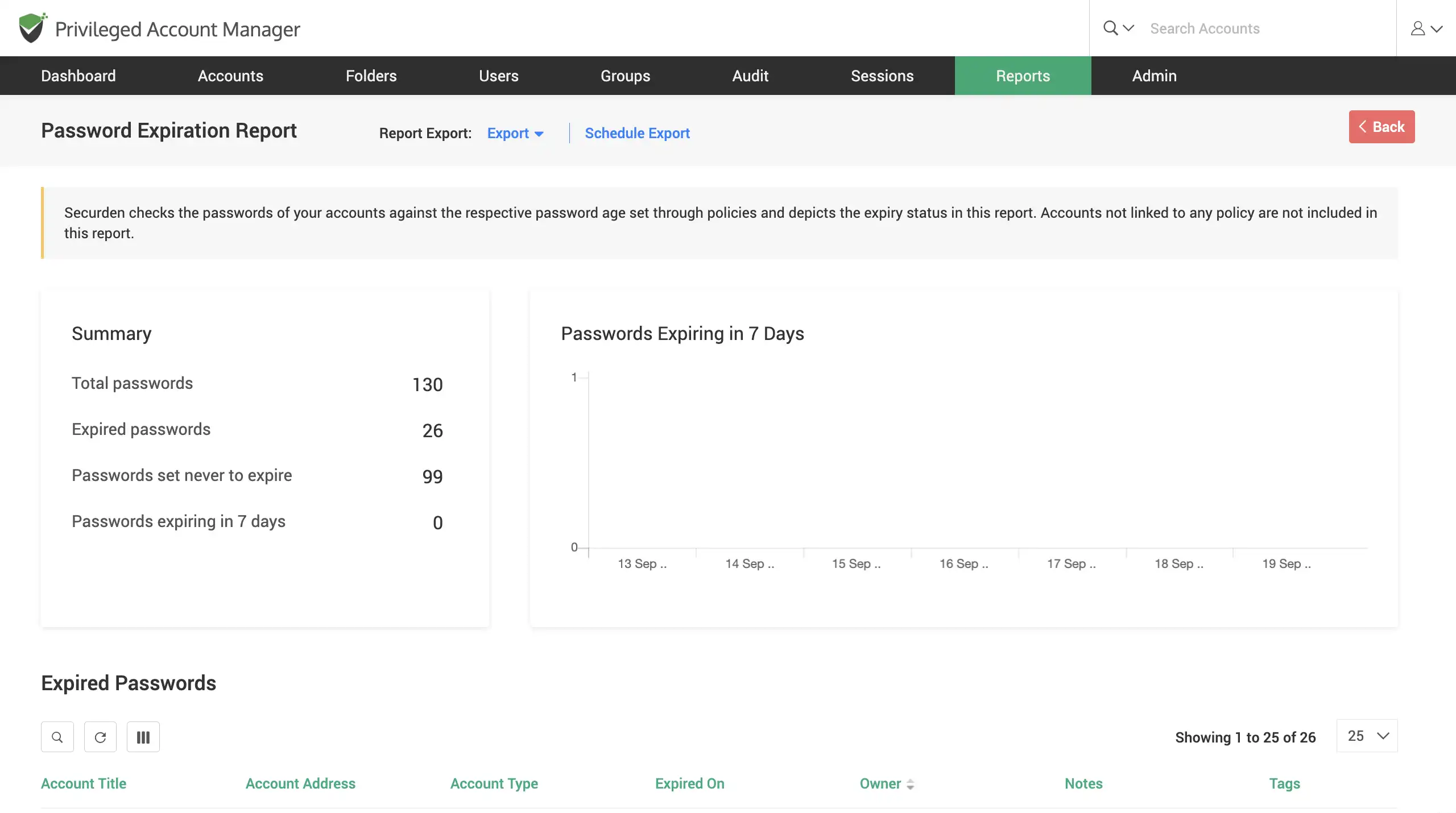
Monitor expiring passwords
Monitor passwords that go beyond their password age (Password age is defined through the password policy). All expired passwords, and ones close to expiry are consolidated in this report. You can renew such passwords using the inbuilt password generator. Additionally, you can also schedule periodic password reset to ensure passwords do not expire.
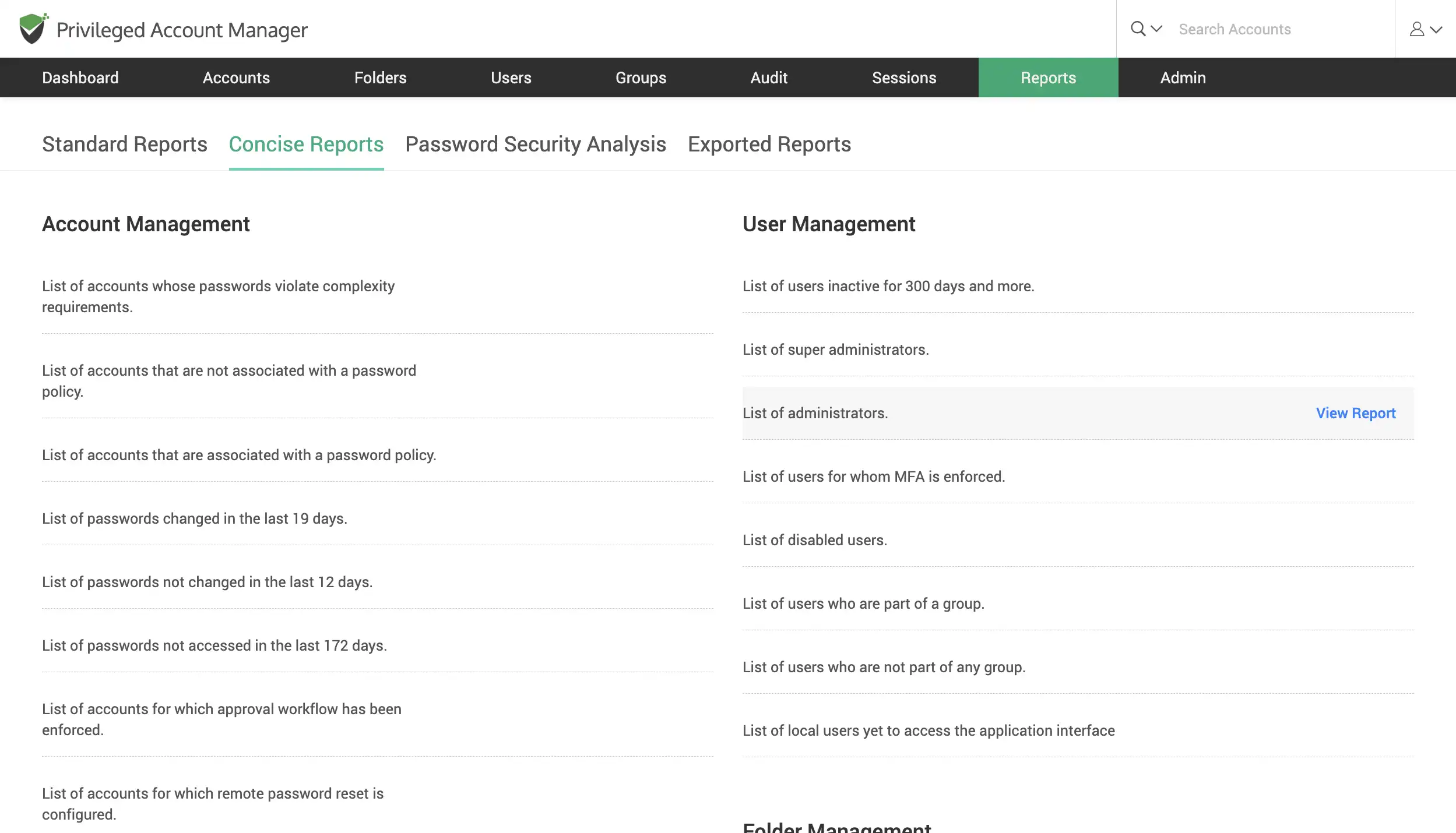
Generate micro reports for specific requirements
Generate concise reports which cater to specific needs. With the ability to configure these micro reports down to the last detail, they come in handy during an audit or for compliance requirements. These reports answer very specific questions such as ‘List of Inactive Users’, and ‘List of passwords changed in the last N days’.
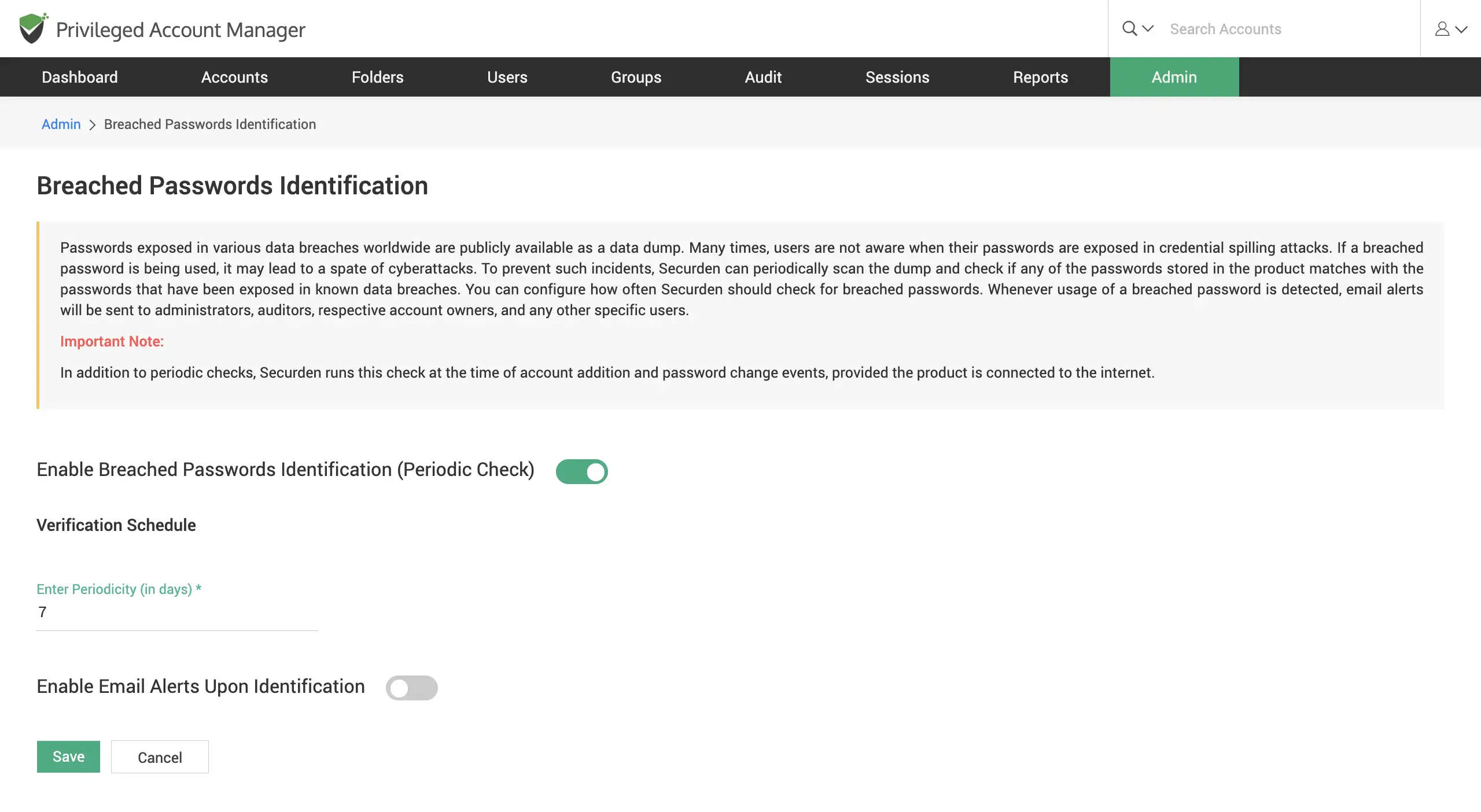
Identify & replace vulnerable passwords in use by scanning the dark web
Scan the dark web for exposed passwords and compare them with the hashed replica of your passwords to identify which account passwords have been previously compromised. Get email alerts for breached credentials upon identification.
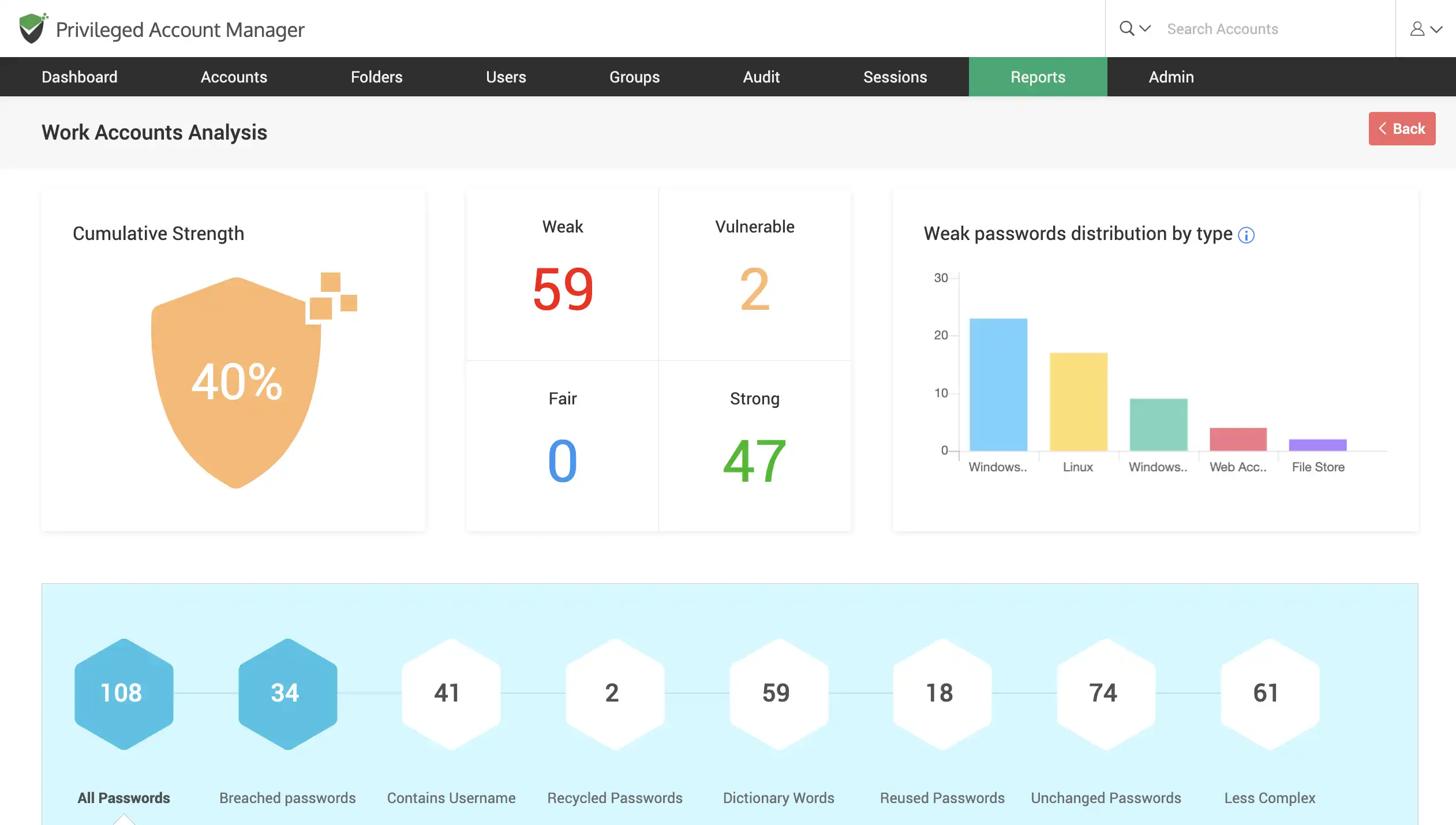
Assess the strength of your passwords
Investigate all your passwords to get a cumulative strength score of them. This report also assigns a strength score to each specific password and divides them into four groups: weak, vulnerable, fair, and strong. The reason for each classification is also explained, allowing you to take remedial measures to improve your password security.
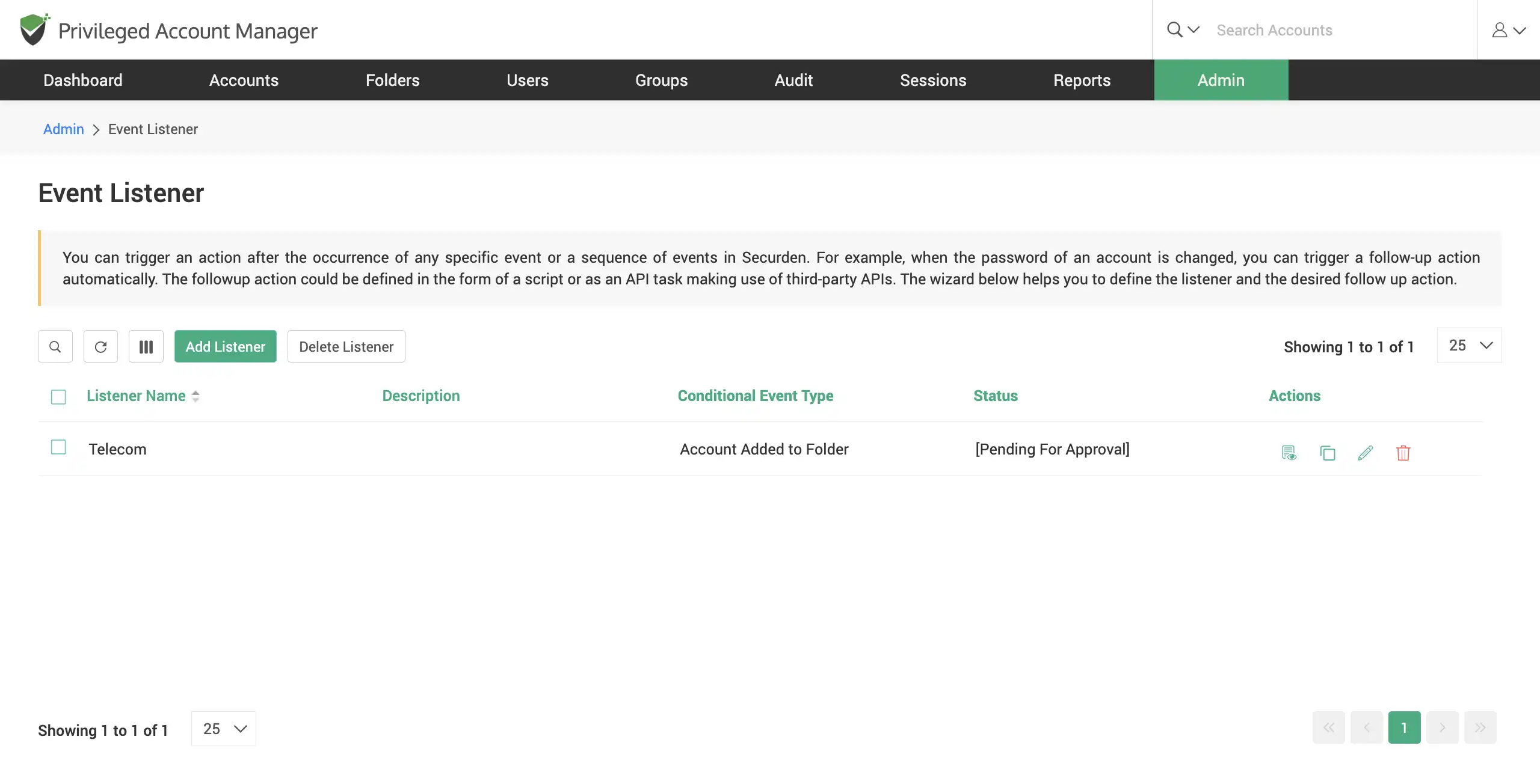
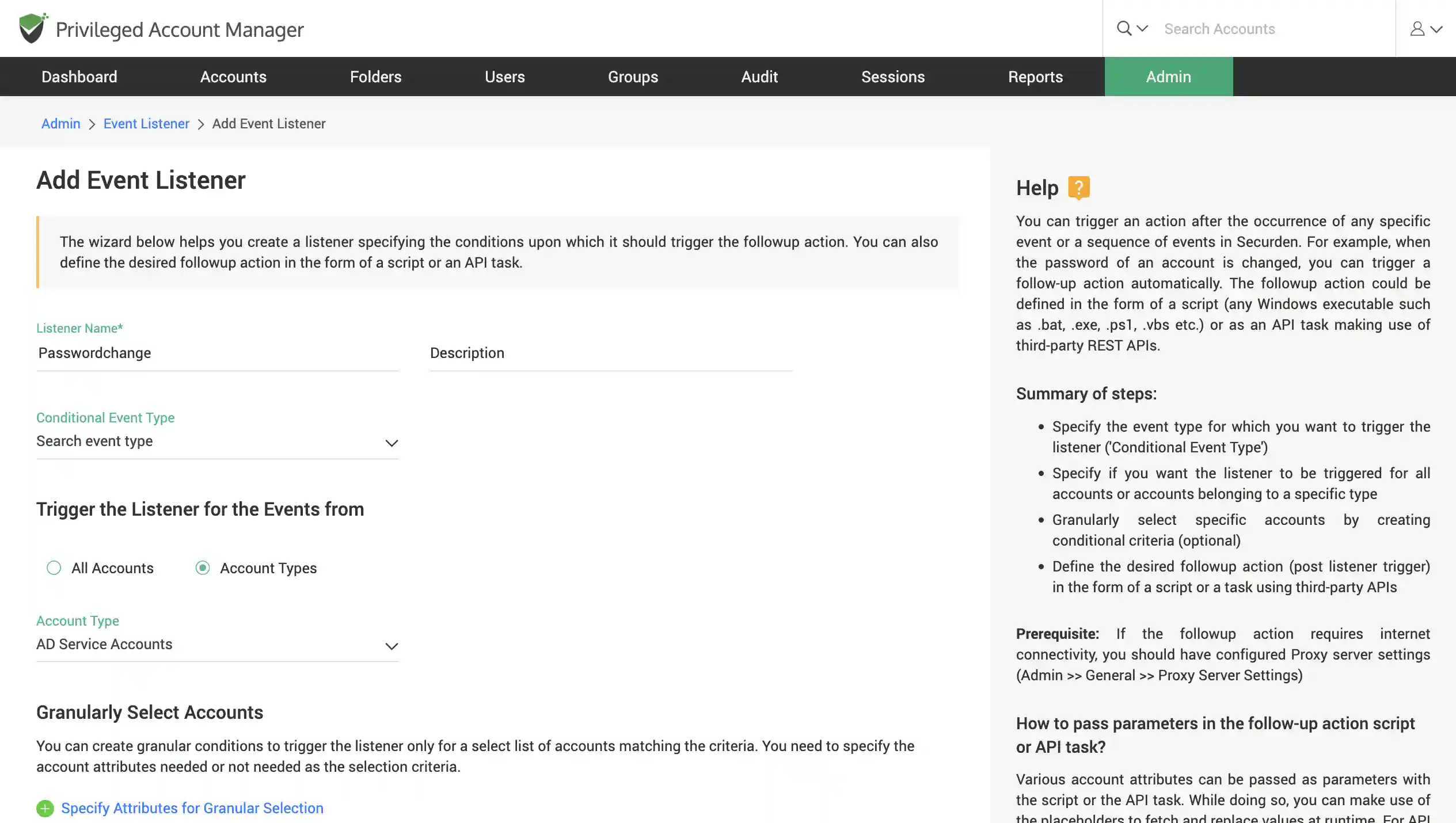
Trigger automated follow-up actions for swift incident response
Trigger automated follow-up actions for any event that occurs in Securden. You can select specific critical events like account deletion, breached password identification and define an action to be carried out as a response. These response actions can be input in the form of a script or a task (Using APIs). Typically, Securden continues to listen for the event to occur and then executes the script you defined to do the follow-up action.
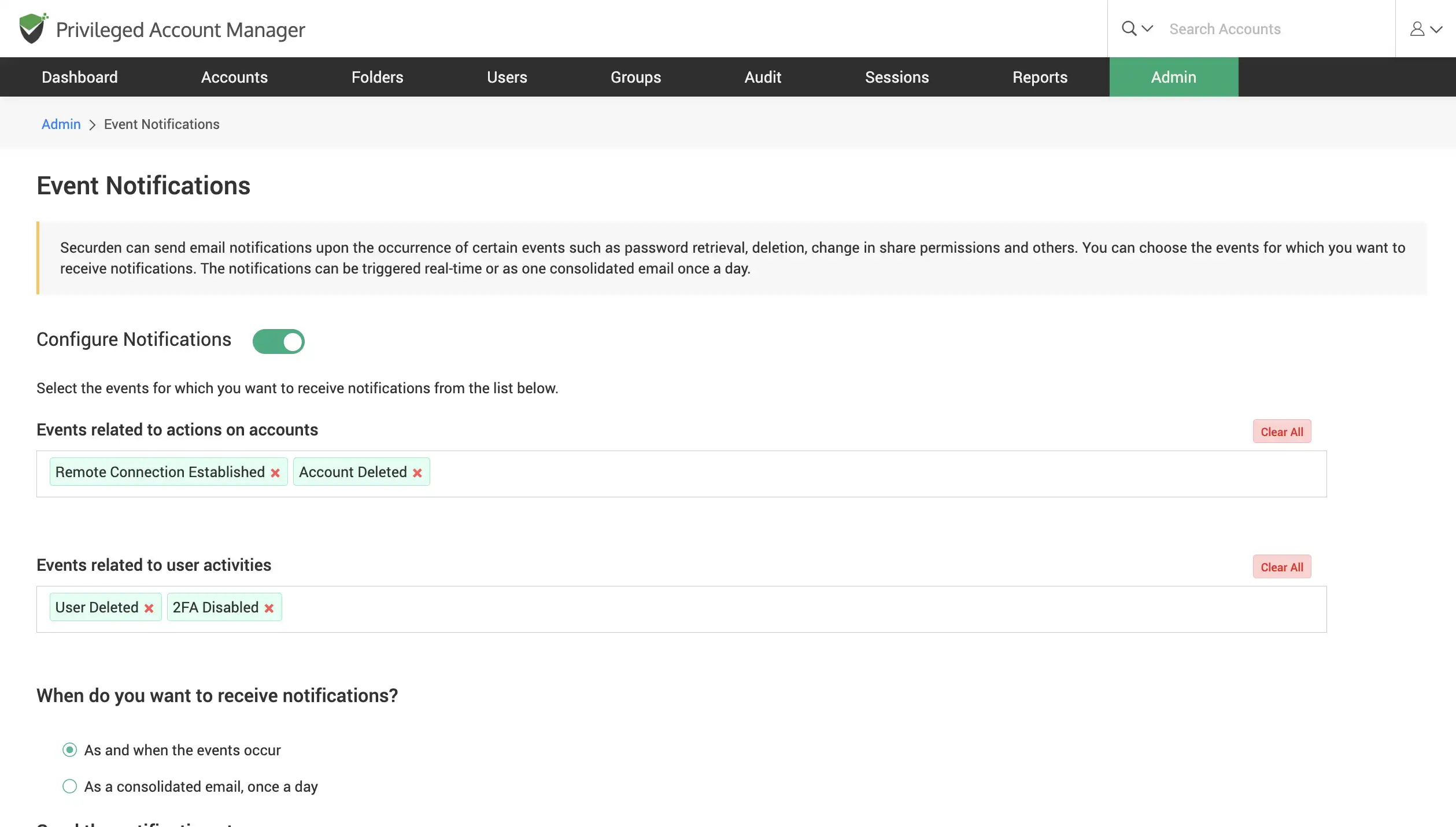
Receive event notifications in real-time
Receive email alerts when a specific event occurs, such as password retrieval, addition, deletion, or other modification activities. You can specify which events should be notified. The notifications can be sent out in real time as the event occurs or as a consolidated email once a day.
Endpoint Privilege Management
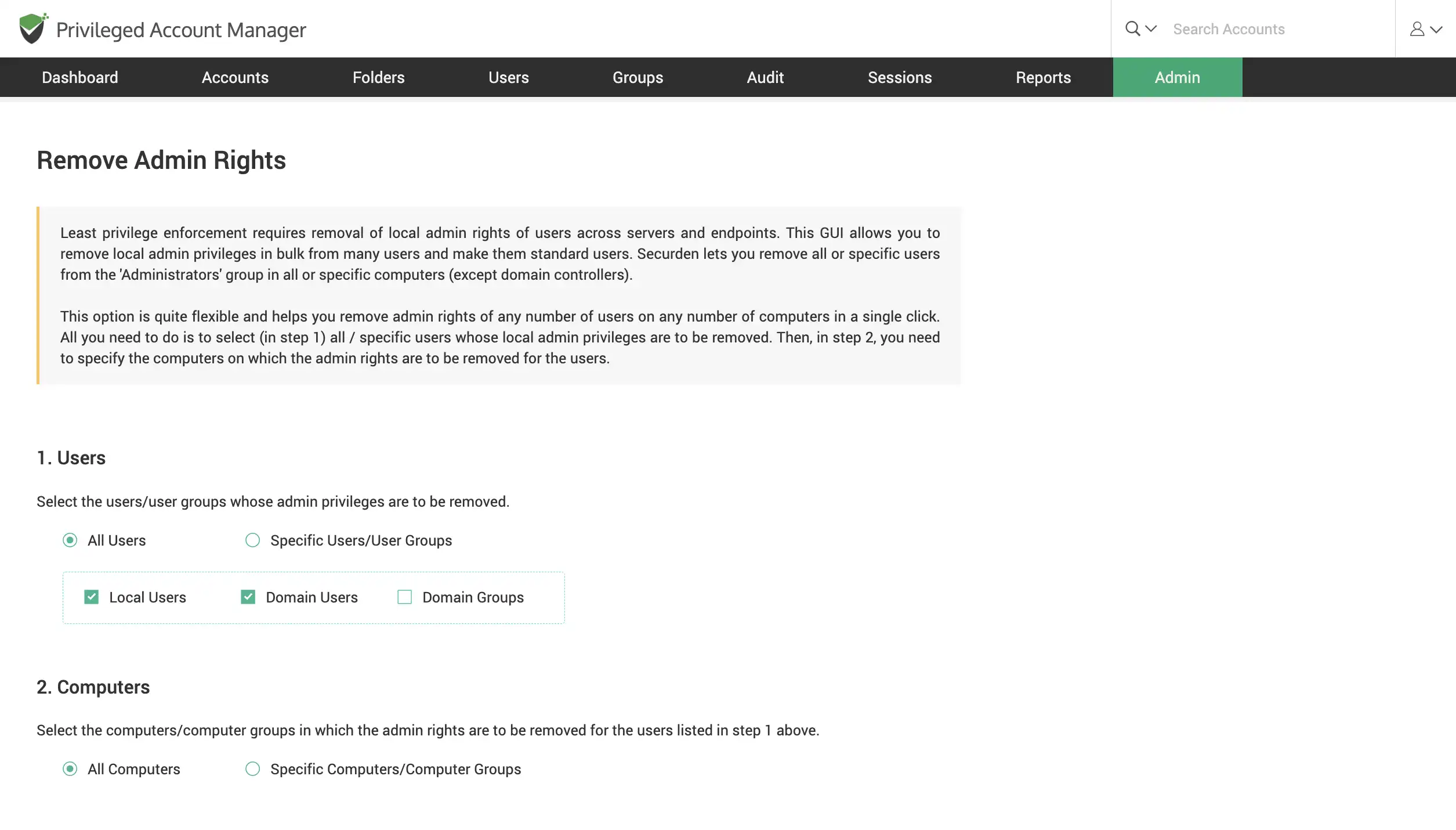
Remove admin rights across endpoints, servers
Granularly eliminate administrator rights for your users, across all systems. Deploy the Securden Agent on endpoints where you wish to control user rights and control applications.
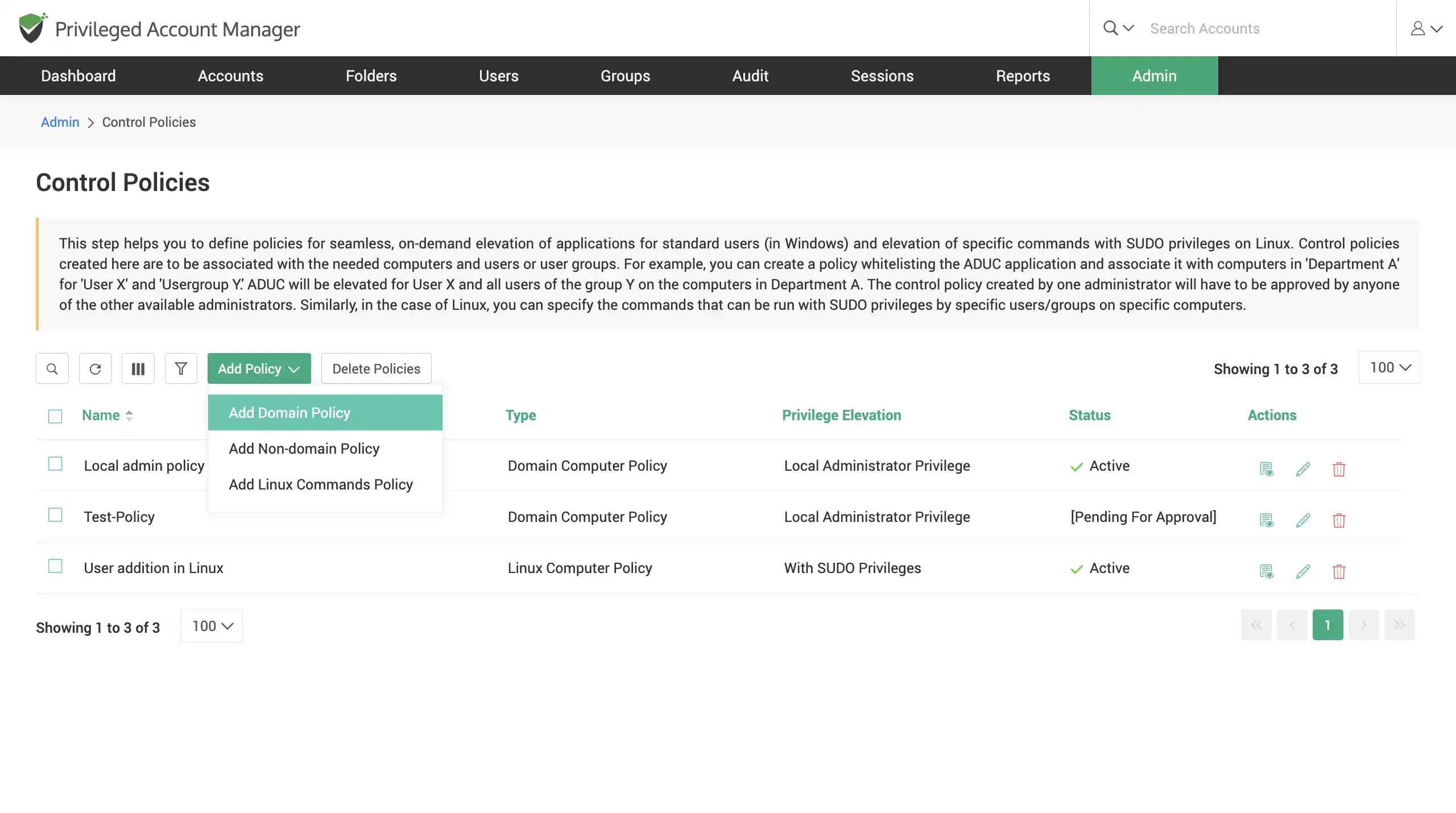
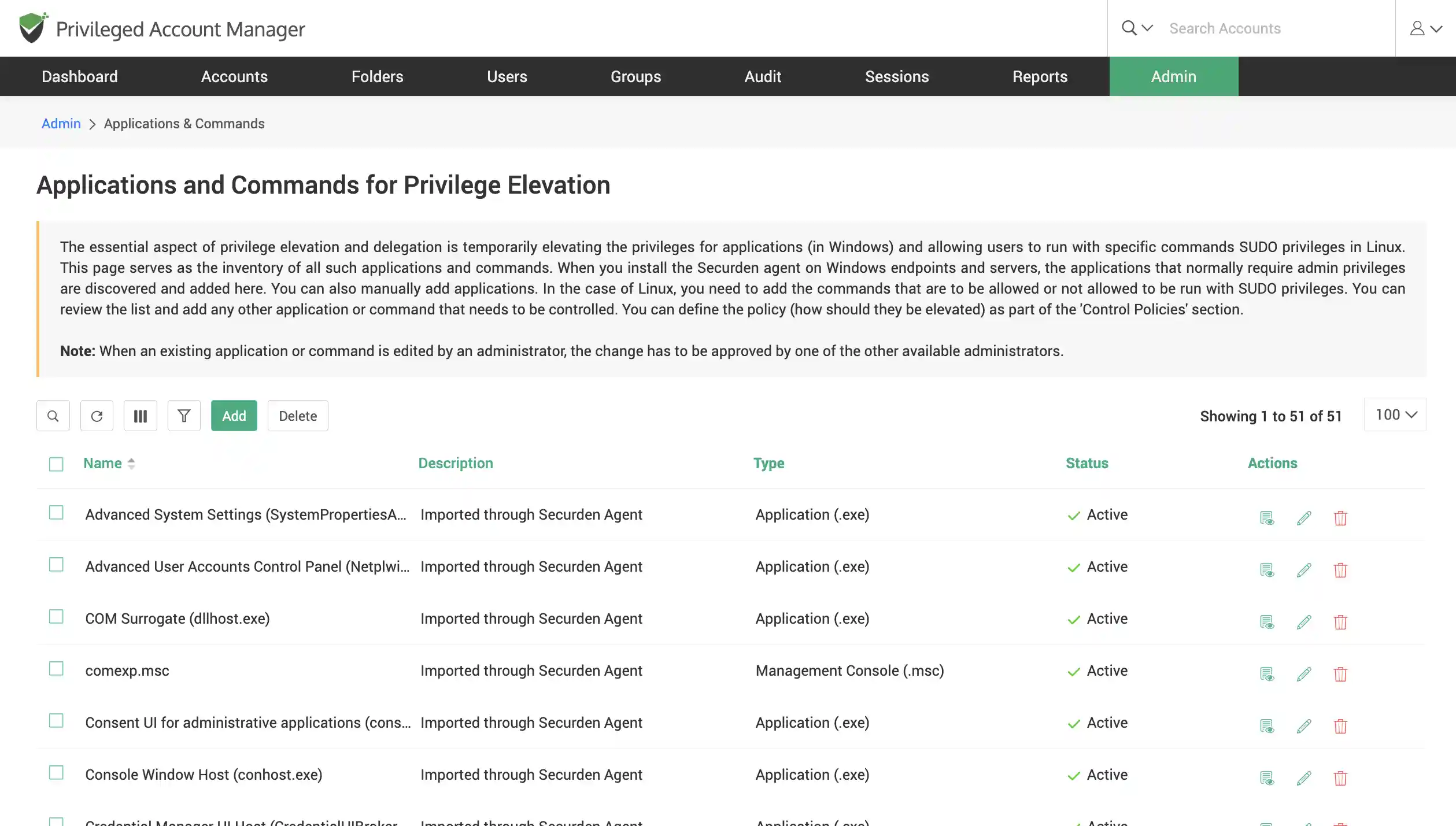
Elevate applications for standard users on-demand
Define centralized policies to whitelist/block applications for specific users/user groups. Elevate applications/commands for standard users on-demand with approval workflows.
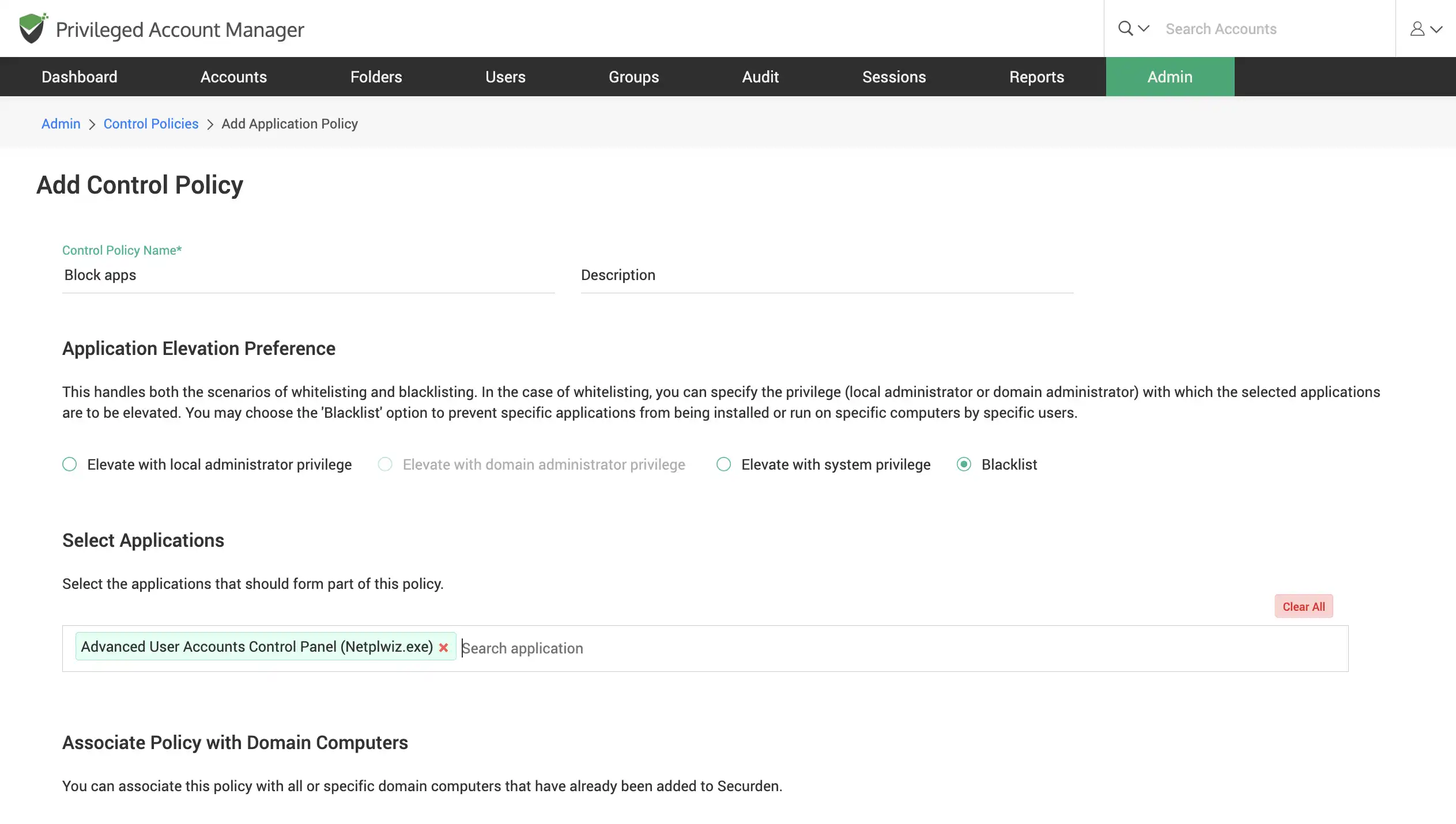
Establish command filtering and application controls on Unix
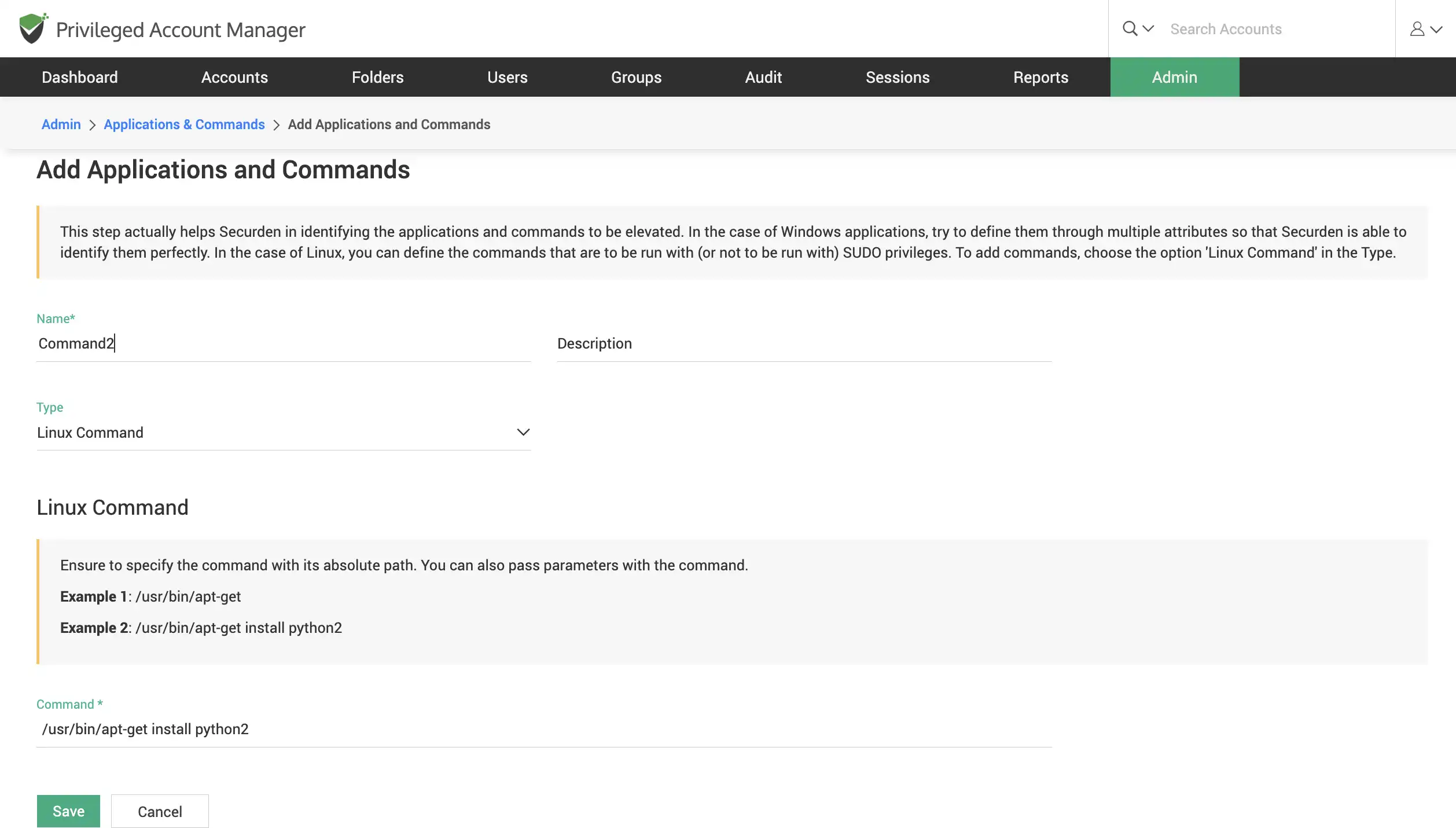
Establish controls for which commands can be run (or not run) in Linux with sudo privileges. All requests raised by users for running applications and executing commands can be approved by an administrator or a user designated as the approver.
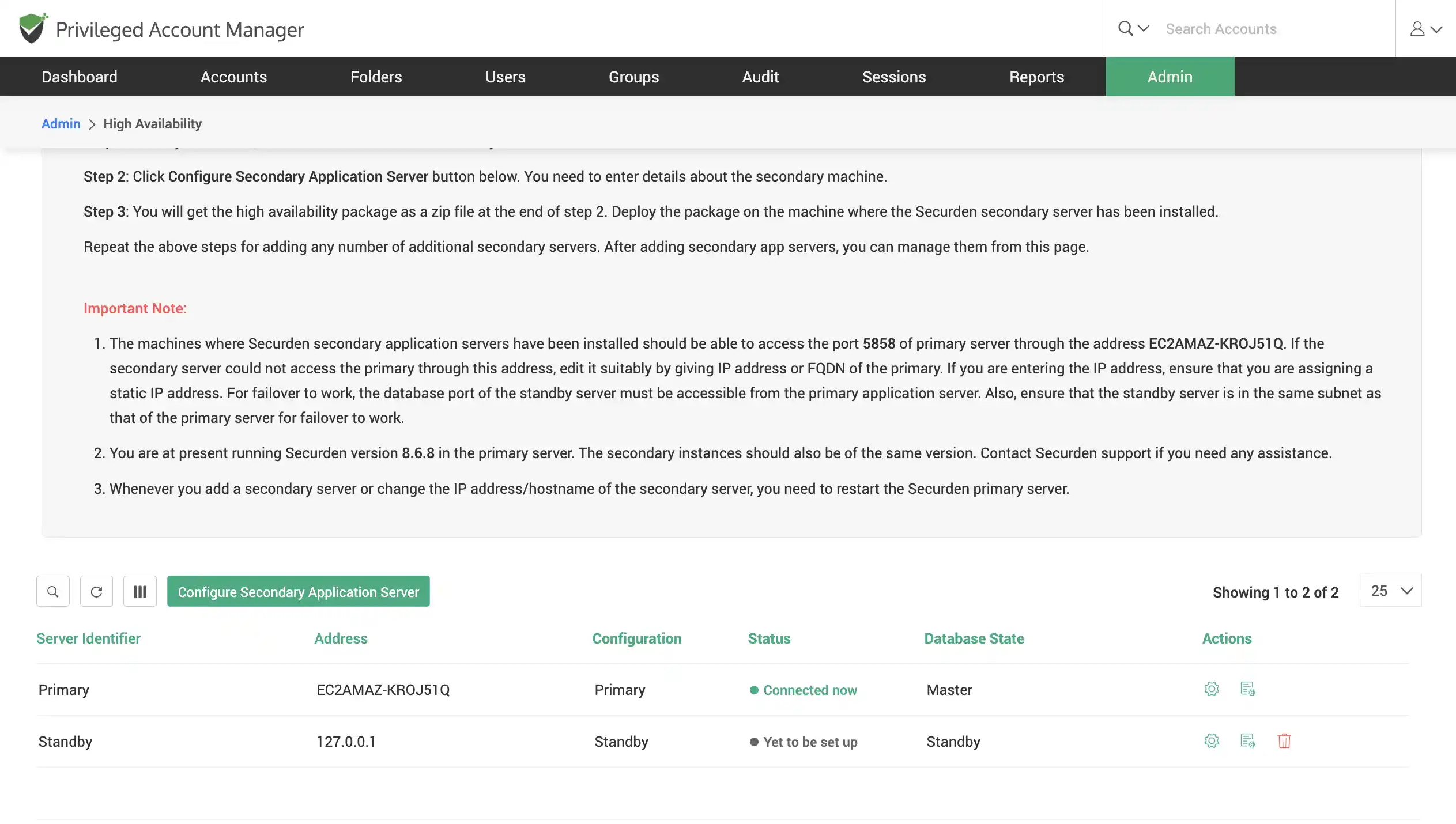
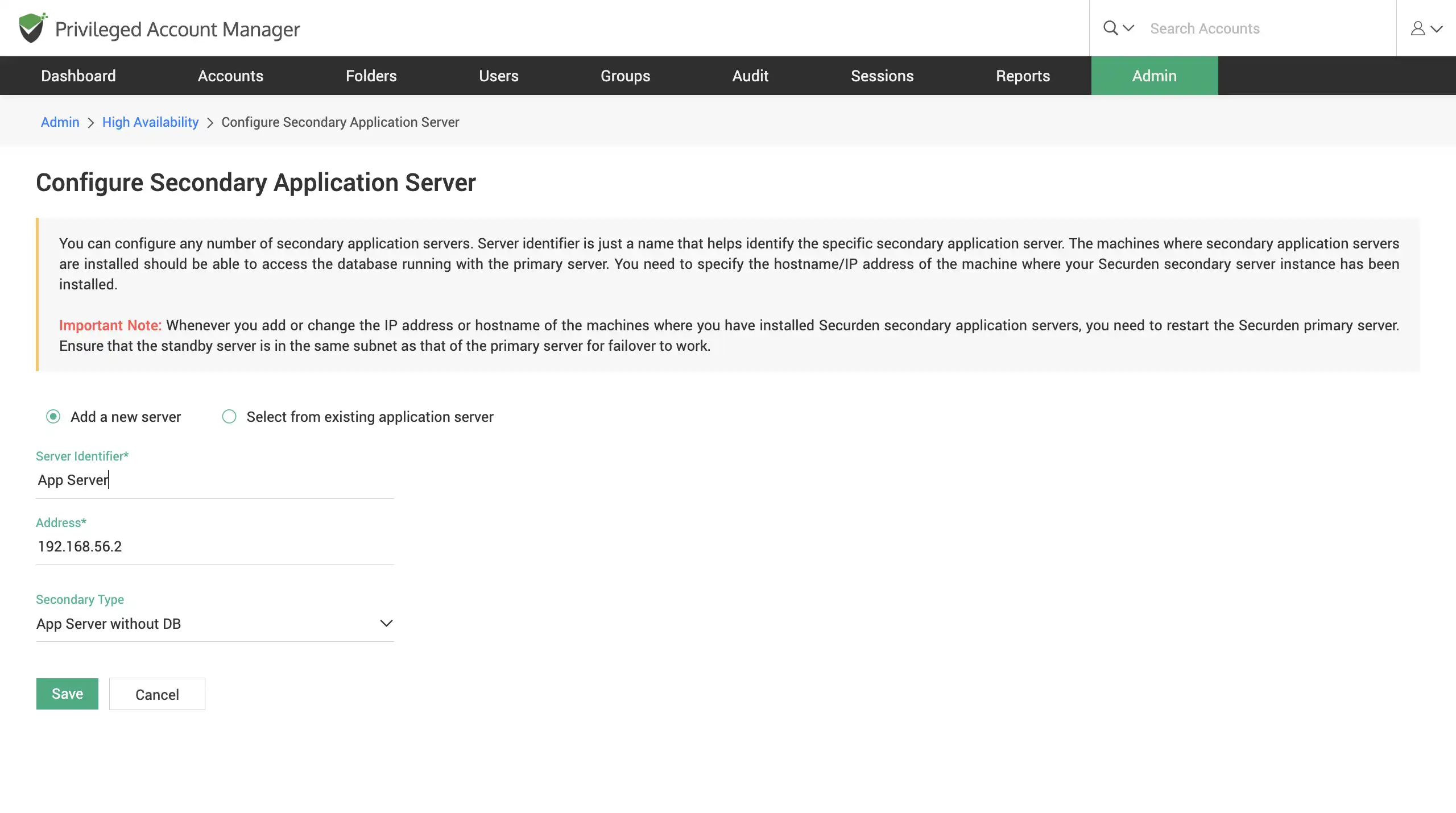
Configure high availability to ensure uninterrupted access to privileged passwords
To ensure uninterrupted access to the web application, Securden comes with high availability architecture. Deploy any number of additional application servers, which would serve as the secondary servers.
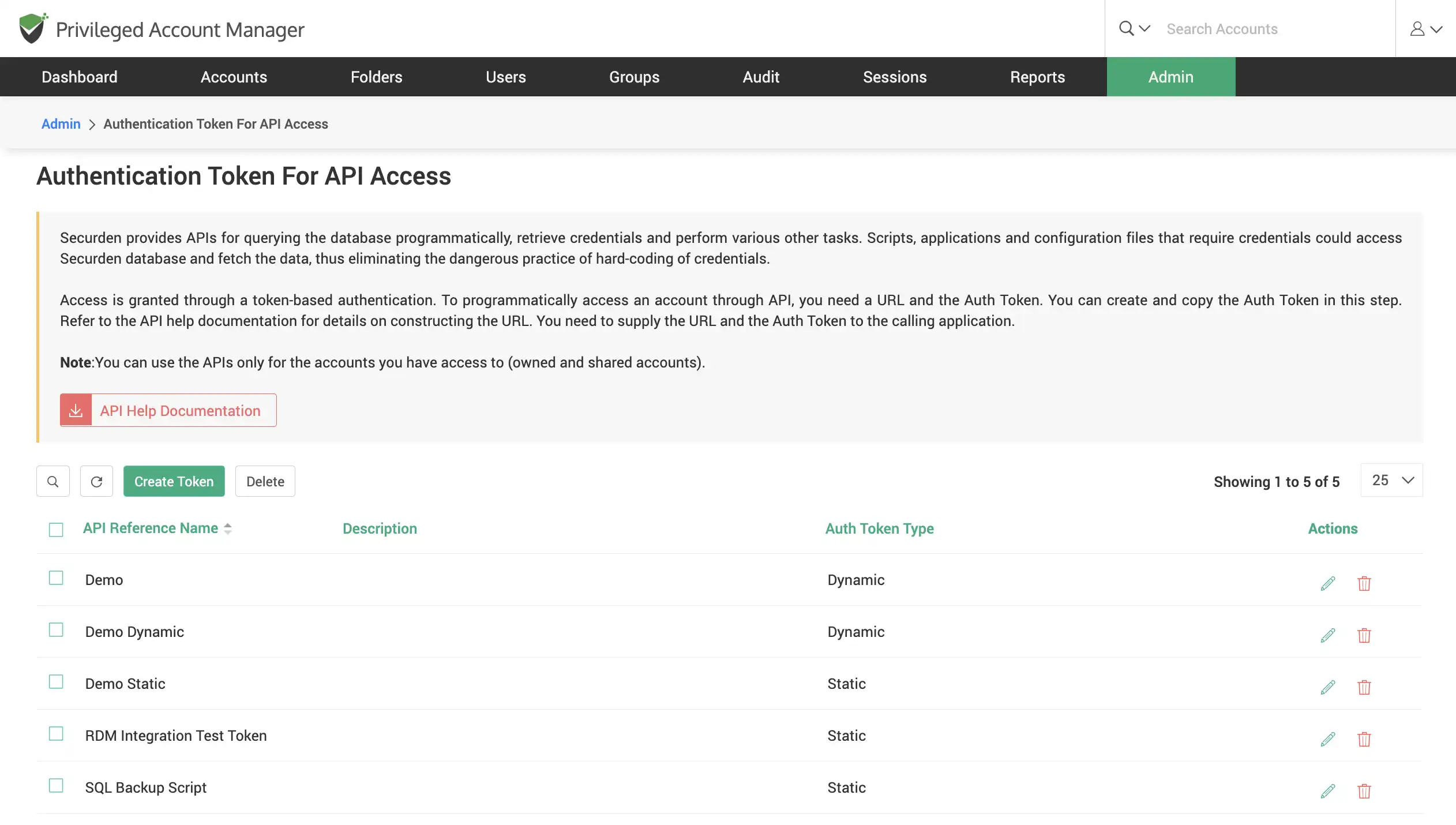
Eliminate hardcoded/embedded credentials using APIs
To ensure smooth workflow, machine and application identities, DevOps secrets, and SSH keys are supplied when required with the help of a compelling set of APIs. Programmatically retrieve credentials, create accounts, add users, modify attributes, etc. with RESTful APIs.
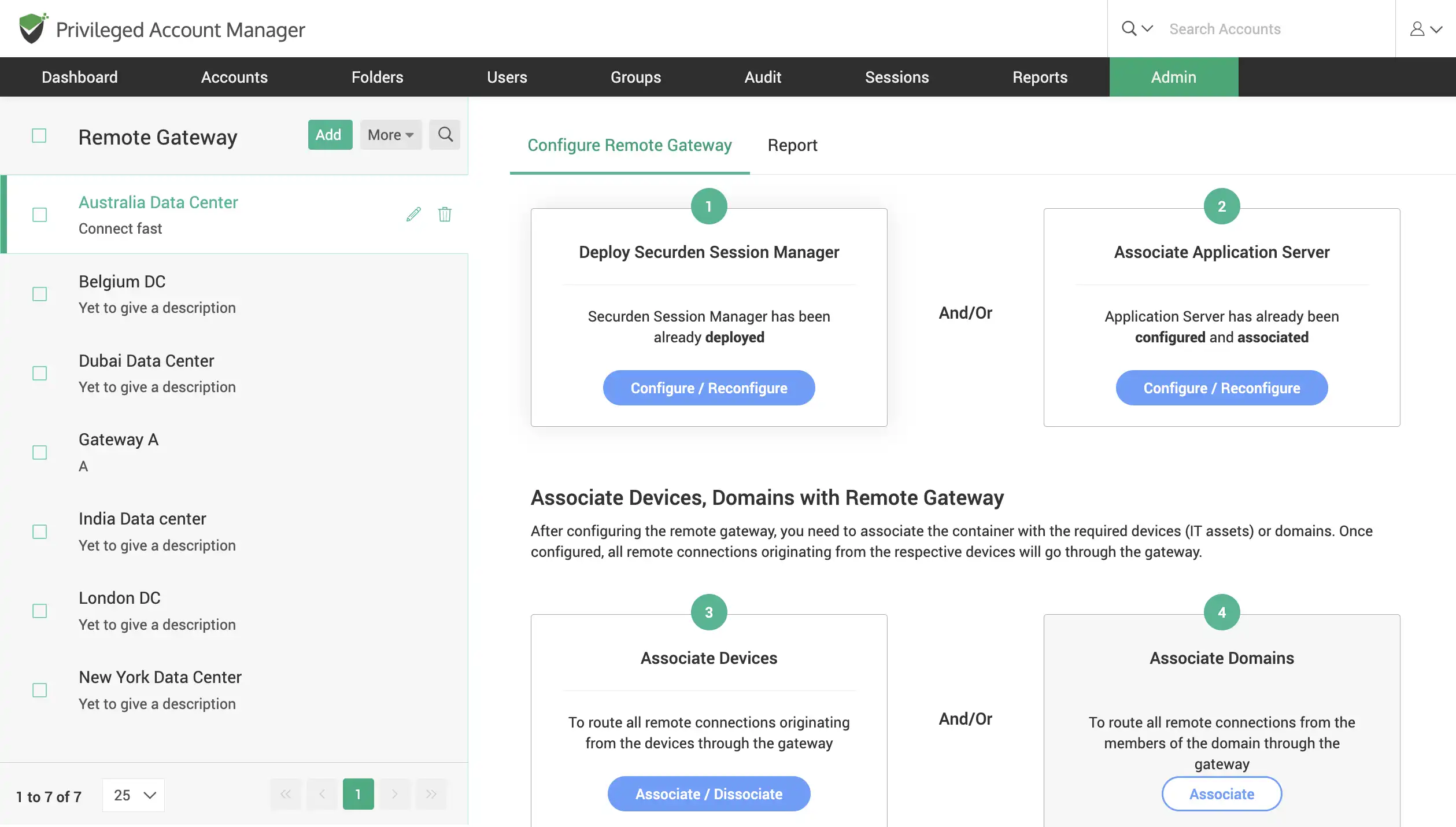
Leverage remote gateway for remote connections and operations
Connect to remote devices using native, and web-based remote connections and record all sessions launched. Carry out remote password reset operations using the application server that acts as a remote broker.
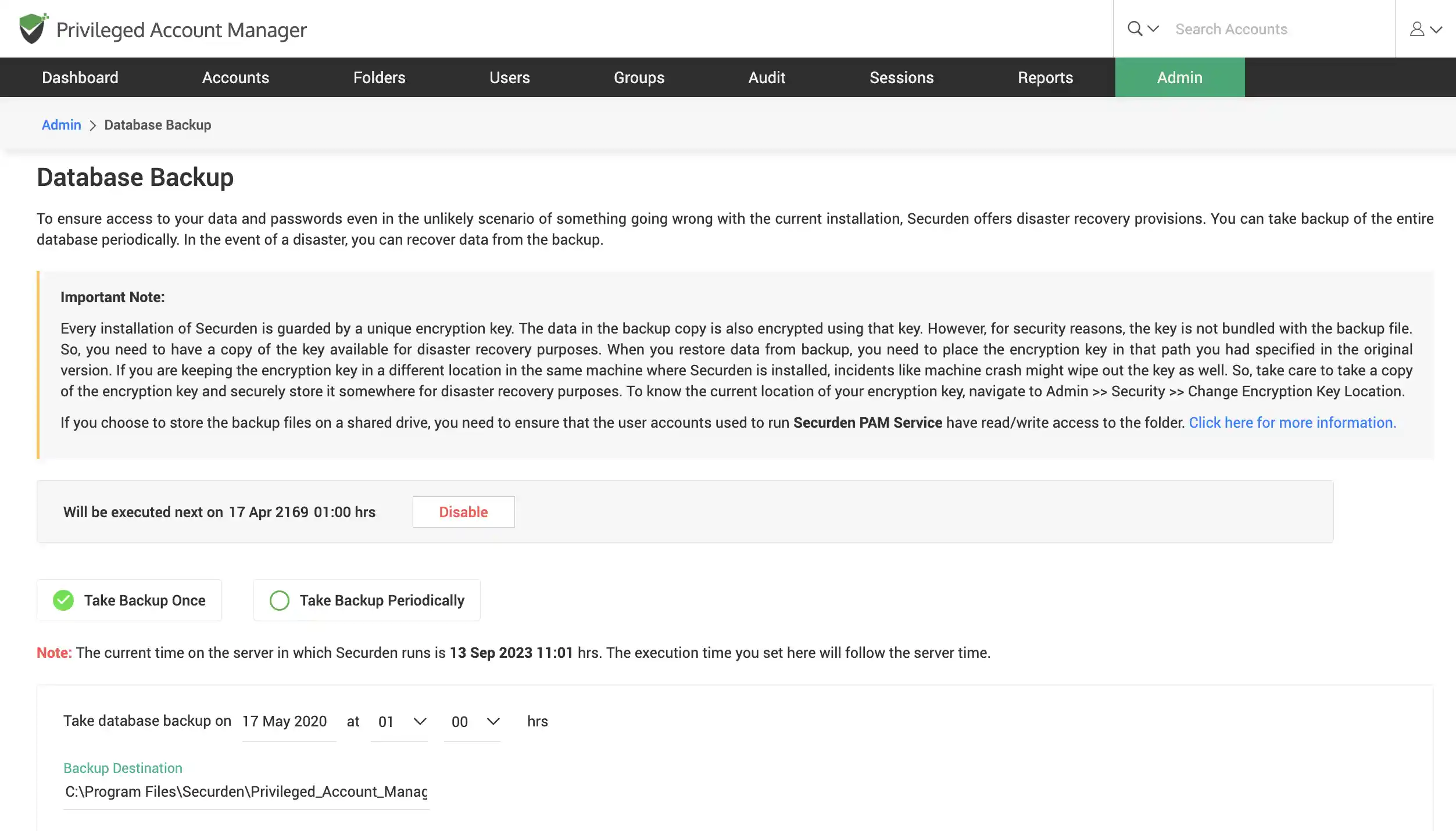
Set-up disaster recovery with periodic backups
Automate back-up of all your data and passwords stored in Securden in the event something goes wrong in your installation. Choose between taking individual back-ups or scheduling a periodic backup within a specified time frame.
Integrate with SIEM solutions to obtain actionable insights
Send syslogs of all events occurring in Securden PAM to SIEM solutions such as Splunk, Fortinet, LogRhythm, etc.
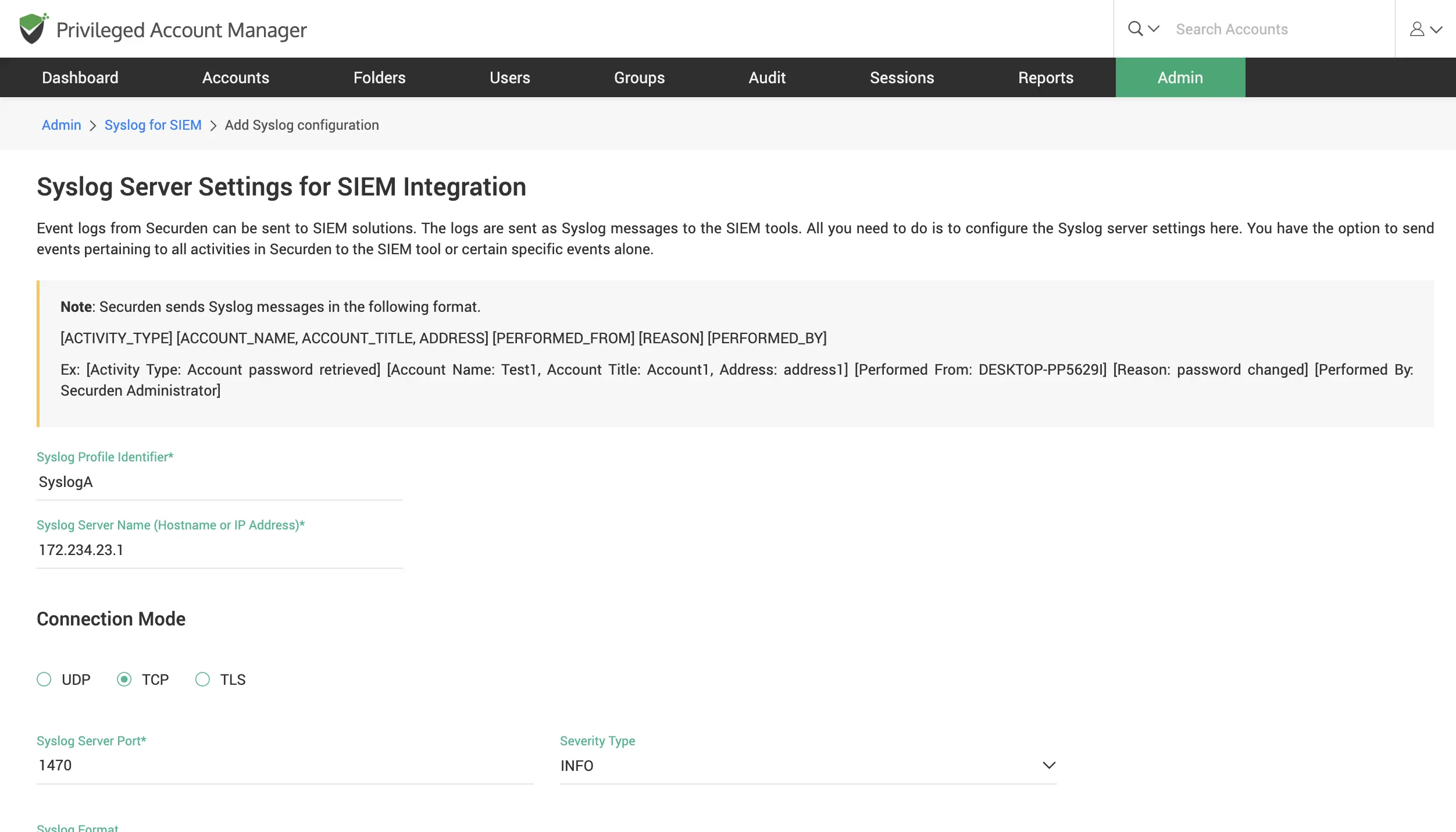
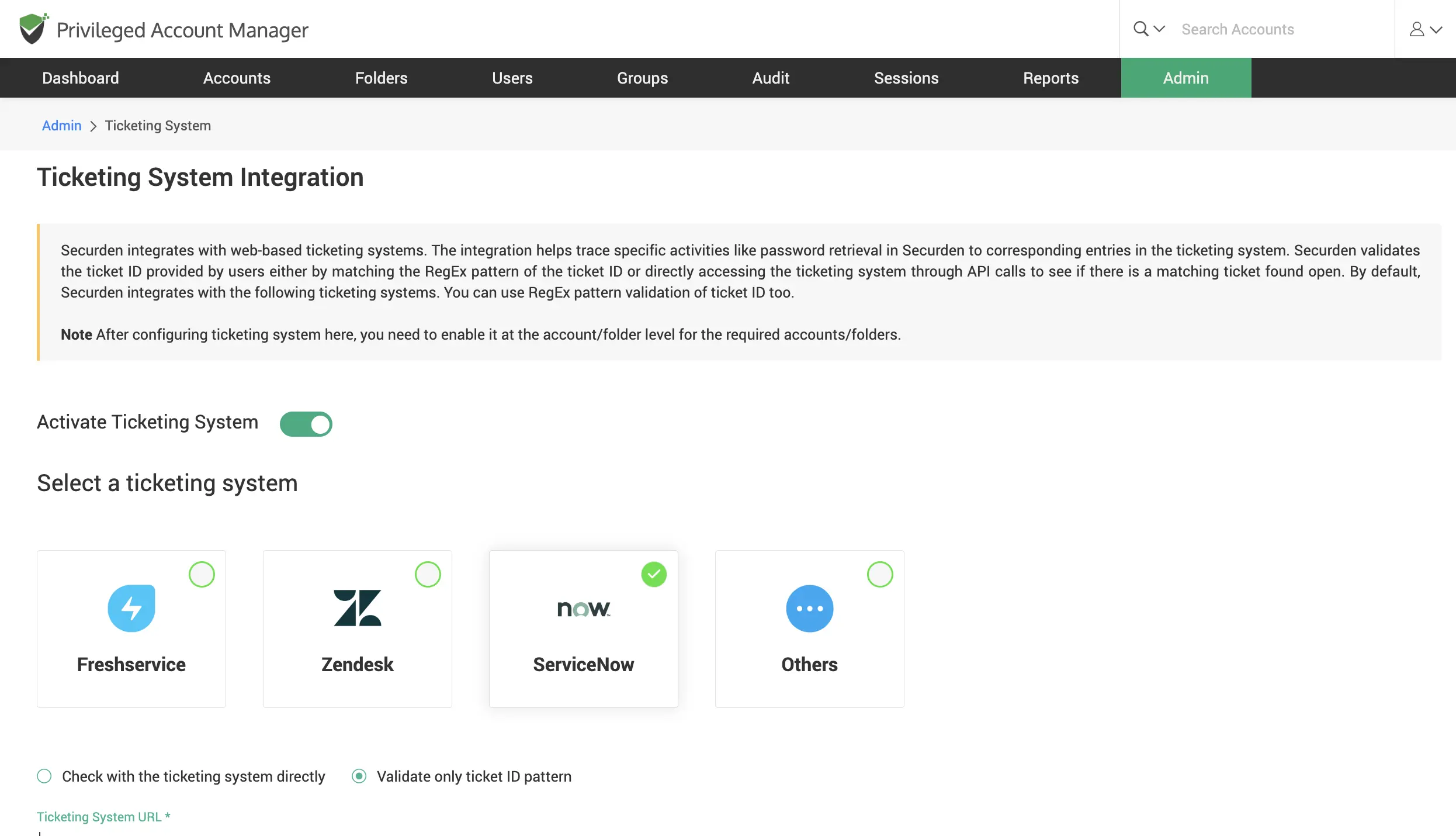
Integrate with ticketing systems
Allow access to accounts based on a valid ticket ID. Integrate with leading helpdesk solution providers such as Freshservice, Zendesk, ServiceNow, and others.