Programmatic access to applications and databases via APIs
In a typical business environment, apart from humans, applications also constantly require access to privileged information. To make operations A2A (application-to-application) and A2DB (application-to-database) communications seamless, credentials are often hardcoded in plain text in scripts, processes and configuration files. This can be detrimental for organizational security as developers can accidentally publish the code (containing plain-text passwords) on GitHub repositories. This causes malicious attackers exfiltrate privileged credentials through scanning tools and launch an attack.
Eliminate hardcoded credentials. Achieve seamless A2B and A2B communication through programmatic APIs.
Securden provides a safe way to handle application-to-application and application-to-database password requests by bringing together all credentials in a centralize, encrypted repository and then allowing programmatic access to the repository. Securden helps achieve this through:
-
Centralized encrypted repository: Securden’s discovery engine helps discover privileged accounts from a variety of servers, databases, and network devices and consolidate them in a centralized repository with AES256 encryption. The existing weak passwords can be rotated and replaced with strong, unique passwords using Securden’s inbuilt password generator.
-
RESTful APIs: Securden offers a set of RESTful APIs that helps applications, databases, and processes programmatically access credentials during runtime. The entire workflow is automated and happens in the background and at the same time prevents exposure of plain-text passwords.
-
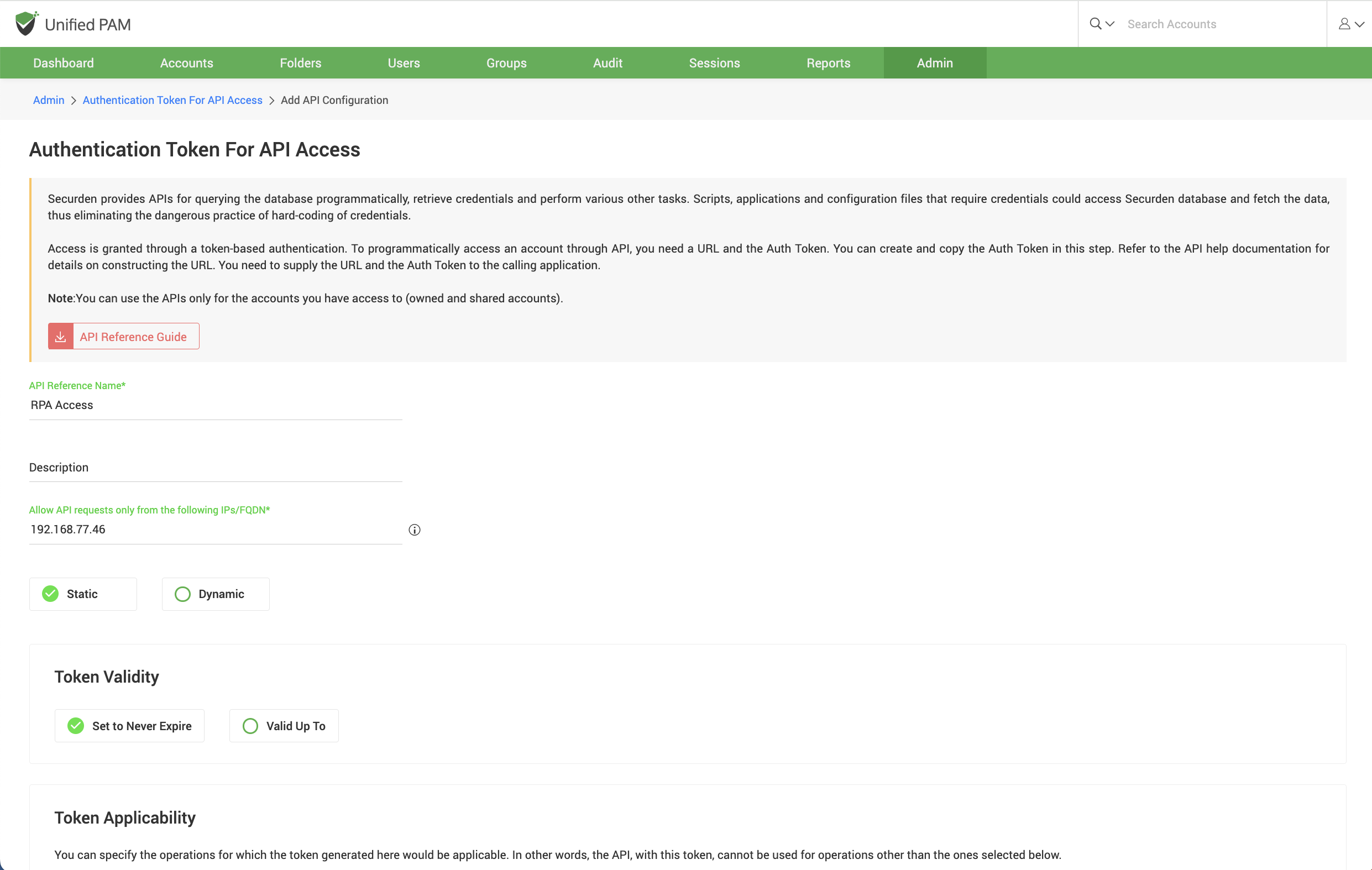
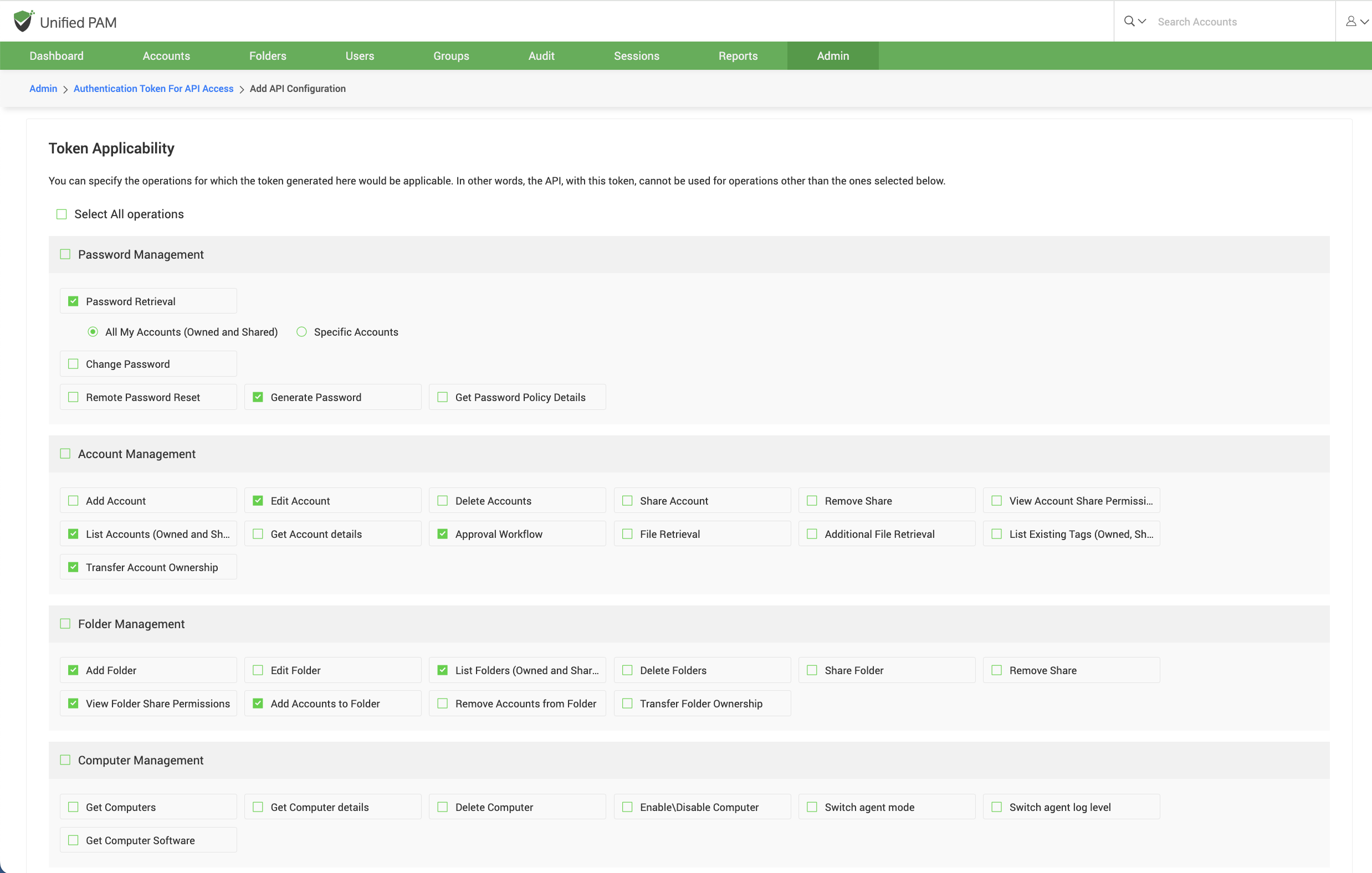
Token-based authentication and host restrictions: When an application tries to access the APIs, a time-limited token is generated. The applicati on is authenticated only if the request originates from a host device whose IP address is specified.
The password management operations automated through APIs are thoroughly audited and are available in the form of comprehensive audit trails.