Lack of visibility over shared credential access
Many privileged accounts within the organization are shared accounts that are co-used by multiple employees. Most often, once the credentials are shared there’s no way to find out when, how often, and by whom these accounts are being used. Continuously monitoring the usage of privileged accounts and providing granular access permissions for users depending on their job role can help IT teams avoid privilege creep.
Manage privileged access by selectively sharing accounts and passwords to users and groups with granular permissions.
Securden Unified PAM helps IT administrators share privileged accounts and provide granular access permissions for users on the shared accounts based on their job roles and responsibilities. There are four permission levels with which an account can be shared:
-
Open connection – Allows launching remote connections to target devices through auto-filling of credentials and eliminating plain text password exposure.
-
View – Allows users to view the account details and password
-
Modify – Allows users edit the current password
-
Manage – Grants entire controls and acts like concurrent ownership
Share permissions can be assigned either to individual users or users in bulk. When a particular user is added to a user group, the same share permissions will be inherited. In the case of Active Directory users, this can be achieved via scheduled synchronization of Securden user groups with Active Directory user groups.
Assume that an account exhibits unusual activities – frequent logins or longer time spent with the account, or it’s being accessed by a user who no longer has any relevance to that account. On encountering with such suspicions, administrators can immediately revoke access to that particular user for that account and control further damage.
Least privilege for accounts shared at multiple levels
Assume that an account is shared to a user with a particular permission. But the user is also part of a group which has higher permissions to access the account. Here, a conflict occurs as to what level of permission should this particular user be granted.
Securden follows the principle of least privilege, which means when sharing occurs at multiple levels, by default, only minimum permissions are granted to the user. Higher levels of permissions inherited are automatically disregarded and these details are available in the form of reports. The administrators can then take corrective actions to elevate privileges if required.
Securely share privileged account credentials with third parties
Organizations commonly work with contractors, third-party vendors, and consultants who require access to privileged systems. Too much access restrictions can result in productivity issues, but at the same time lax security policies can affect your organizational security posture. The tasks carried out by various groups of third parties are different, and policies need to be defined in such a way it doesn’t hinder their day-to-day operations while keeping security intact.
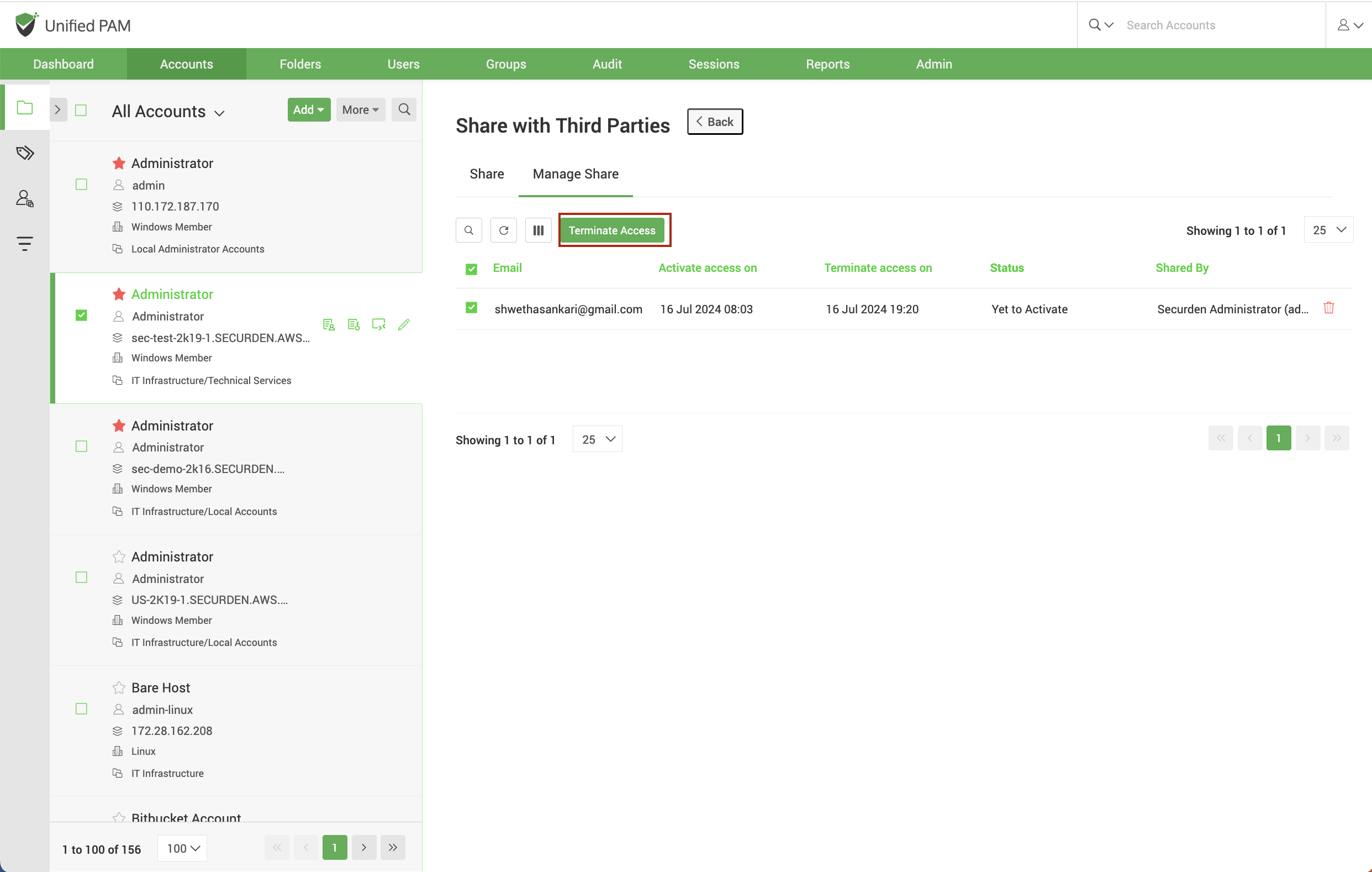
Securden provides options to securely share privileged accounts with third parties via email.
Select an account to be shared and click Share with Third parties. It prompts for the third-party recipient email ID. After entering the email ID, the access can be granted immediately or later during a different time frame using the Activate Later option. The access is automatically revoked once the stipulated time period ends. Securden also provides the option to automatically rotate passwords for accounts accessed by third parties after the time of access. In case you manually want to terminate access before the mentioned time, you can do so by choosing the shared account and navigating to Manage Share >> Terminate Access.
External users requesting access to privileged accounts will receive a hyperlink to their email IDs (in the format shown below). On clicking the link, the user is verified through an OTP (sent to his email ID). On successful verification, the user will get access to the account for that stipulated time window. Administrators can just provide access without revealing the passwords in plain text. Once the duration of access expires, the link becomes invalid, and access is automatically terminated for that particular user.