Establishing ownership for privileged accounts
IT administrators find it a huge challenge to map ‘which’ users have access to ‘what’ credentials, and ‘how often’ these credentials are used. Job role is an important criterion for mapping but is not always the case. Sometimes, non-IT users also require access to privileged accounts like software developers wanting administrator rights to compile code or bind applications with other tools etc. Also, many a times, a lot of credentials get orphaned without any clear ownership. When users having access to privileged credentials leave the organization, the account gets locked if the ownership is not transferred to appropriate authorities.
Establish accountability and well-defined ownership for accounts and passwords
With Securden Unified PAM , IT administrators can define clear ownership for privileged accounts, which then can be shared with granular permissions to various users. This can be done using the Manage permissions under the Share option once the account is added. This way, no account is left orphaned or untracked.
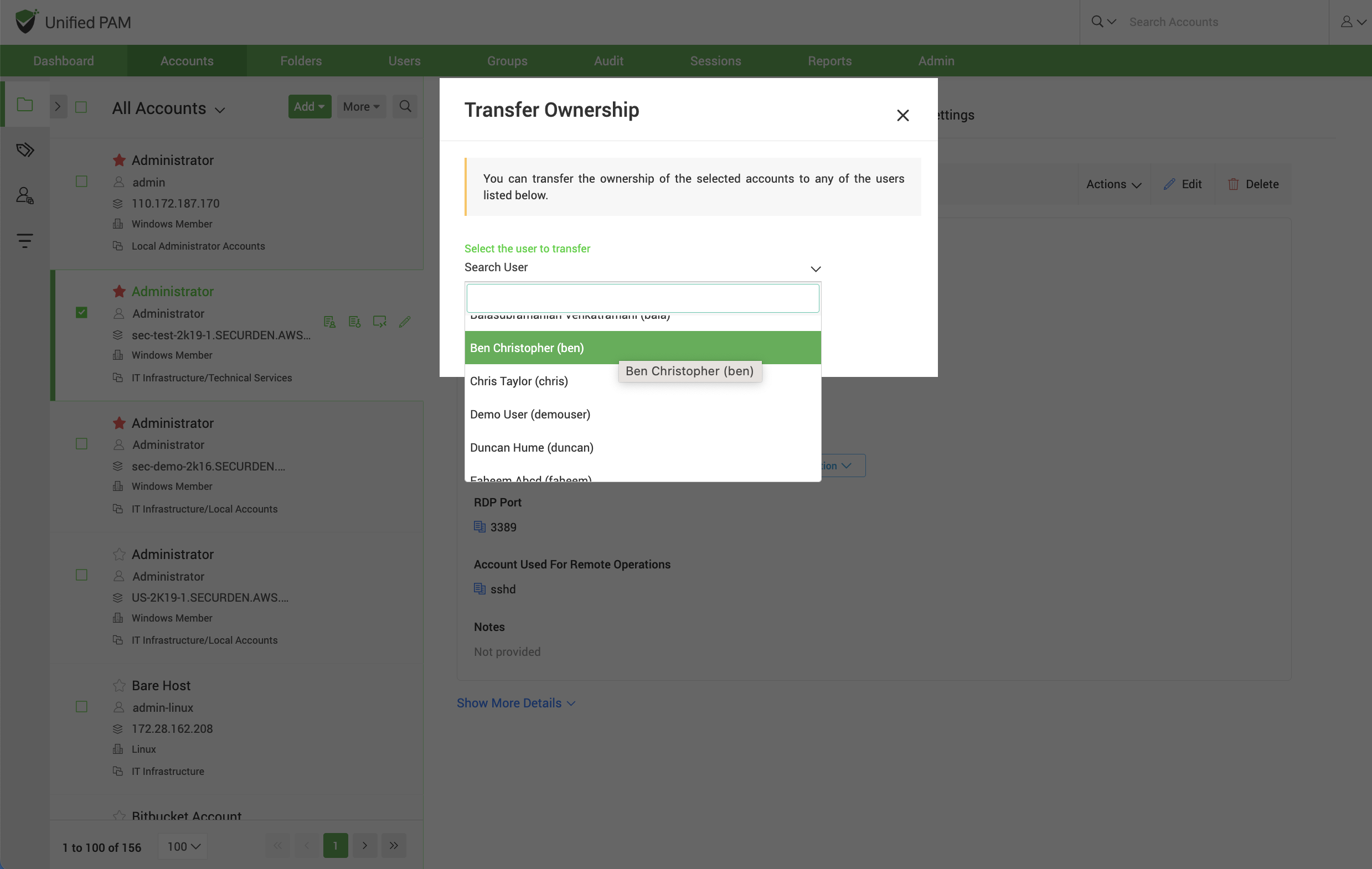
Also, Securden provides administrator the option to transfer ownership of privileged accounts when a privileged user leaves the organization. This can be done in a single click using the Transfer Ownership option. Securden also provides the facility to create clone accounts which inherit the same attributes and sharing permissions as that of the parent account.