Granting secure remote access to internal IT infrastructure
In a business environment, a multitude of users require administrative access to privileged systems for carrying out their day-to-day activities. Business users, IT users, developers remotely connect to privileged workstations, database servers, CI-CD pipelines and other mission critical resources. Additionally, many organizations employ remote or embedded contractors, third-party vendors or even outsource a part of their operations to third party teams who require remote access to corporate privileged systems. Sometimes, users require access to internet facing devices residing in demilitarized zones, where direct access isn’t possible, and a jump host is required to connect to those assets.
In all these cases, administrators need to carefully examine the nature of each access request and the role of the user and provide just enough privileges that enables the user perform the activity his job role entails. This practice helps in least privilege enforcement but manually vetting every access request and providing granular controls is almost impossible.
Launch remote connections to target devices without exposing passwords in plain text
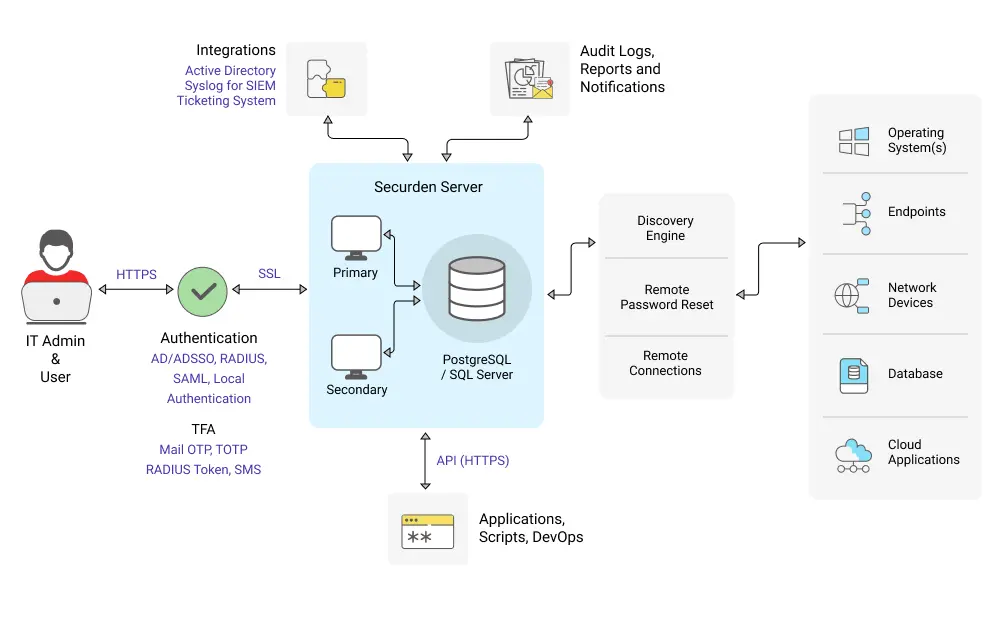
Securden allows end users launch remote connections to target systems without any direct connectivity between the end user machines and privileged assets. Administrators can define fine-grained policies as to ‘which’ users get ‘what’ levels of access, thereby avoiding privilege creep. Securden supports the following types of remote connections:
-
Native and web-based connections to Windows, Linux, and database servers
-
Browser based connections to web applications
-
Thick client applications via custom application launchers
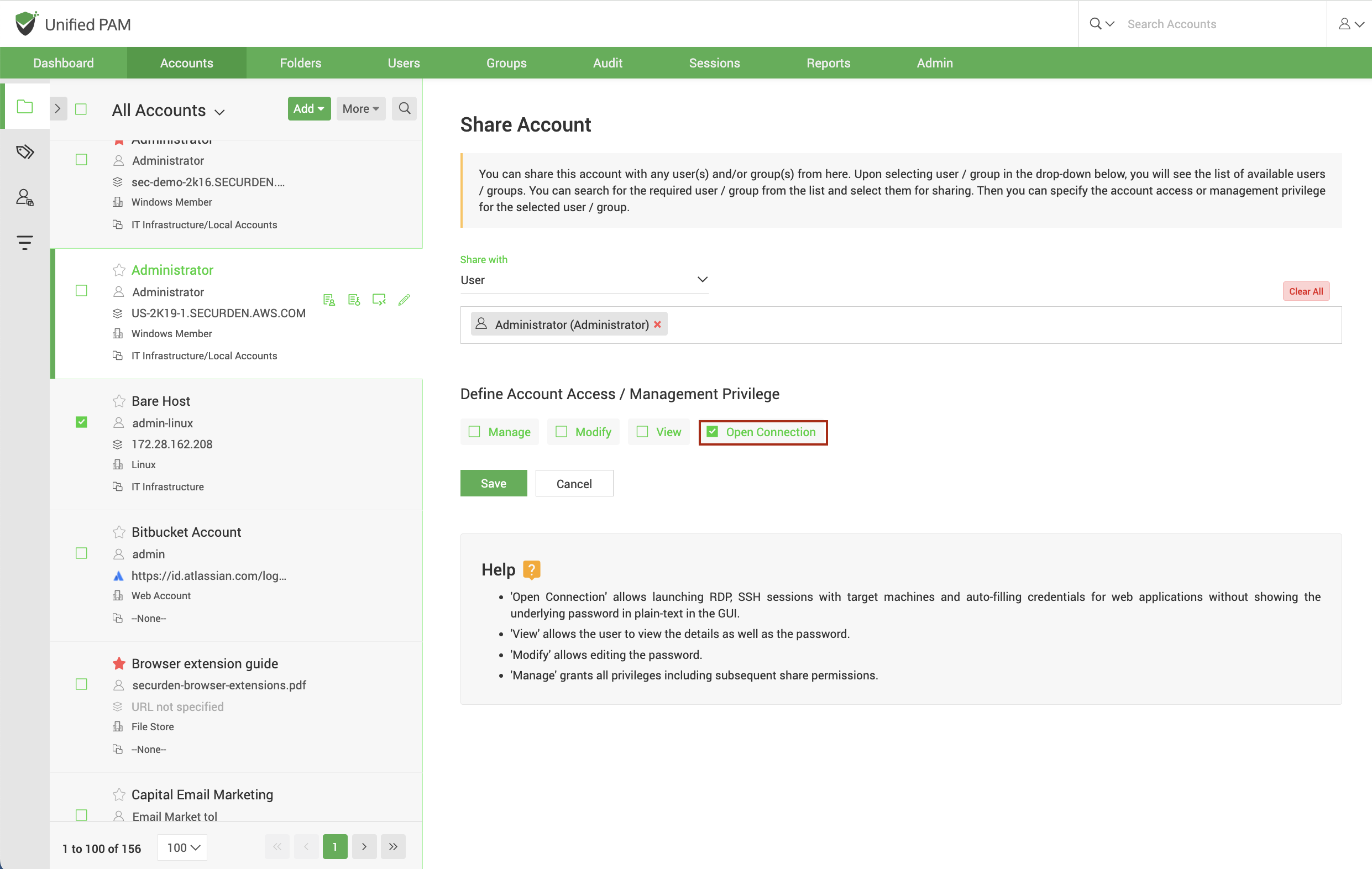
Securden allows administrators to add users and share accounts or devices to which remote connections need to be established with the following levels of privileges:
-
Open Connection – Allows users launch remote connection to target devices or applications through auto filling of credentials, without plain text password exposure in the GUI
-
View – Allows users view the account details and passwords
-
Modify – Allows users view as well as change the credentials
-
Manage – Allows users view, change, and subsequently share the account with other users
For instance, if a contract employee working as part of the marketing team requesting access to CRM will be given Open connection permission where credentials will be masked and auto populated without being revealed in plain text. This way, he can carry out his day-to-day operations without knowing the credentials of the CRM account.
Configure jump hosts as gateways for resources in demilitarized zones
Many a times, users might require access to assets residing in de-militarized zones. Usually, devices facing the internet are segmented this way and cannot be reached directly. One or more jump host is configured, through which the users need to hop and authenticate before connecting to the target systems. This requires passwords to be entered at various stages, which is time consuming and opens up chances for security risks.
Securden secures and streamlines access to resources residing in de-militarized zones by allowing provisions to configure one or more jump hosts for target devices. The credentials are automatically fetched from Securden vault at each stage and the user is authenticated to the target machine, without having to manually enter the password. This workflow not only ensures security but saves a lot of time for users as all the levels of authentication happen in the background without any user intervention.
Provide one-click remote access without plain text password exposure
In today’s business scenario, contract employees and third-party vendors are an indispensable part of the organization workforce. Assume that a third-party technician is requesting access to a network device in your network for troubleshooting purposes. Giving away credentials in plain text is not a security best practice as it can create potential backdoors.
Securden allows internal and external users to launch connection to remote privileges systems without them entering the credentials through the Open Connection option. The password is automatically retrieved from Securden password vault and is automatically injected, and the user is able to access the target device in just a single click.