Secure Remote Connections Using Remote Desktop Connection Manager (RDCMan)
To initiate remote connections to target remote devices via RDCMan, two connections are required: the first is from the client (end-user machines with RDCMan installed) to the jumphost, where Securden Session Manager (SSM) is installed. The second connection is from the jumphost to the remote server. Follow these steps to establish these connections.
- Configure the remote gateway and install Securden Session Manager (SSM) on the jumphost.
- Import users and assets from Active Directory.
- Map users to assets.
- Map domain accounts to assets.
- Configure account details in RDCMan.
1. Configure the remote gateway and install Securden Session Manager (SSM) on the jumphost
By default, the web-based remote connections (web-based SSH and web-based RDP) sessions launched from end user machines are tunneled through the Securden server, which acts as the gateway. There will not be any direct connectivity between the end user machines and the target device.
For enhanced security, you may route all remote operations originating from Securden through a single, dedicated gateway (instead of Securden server acting as the gateway). Once configured, Securden will route all operations, including remote connections, session recording, etc., through the gateway. Remote connections and session recording are managed by the Securden Session Manager (SSM), a component of the remote gateway. To know more about configuring remote gateway and installing session manager on the jumphost, refer here.
2. Import users and assets from Active Directory
Once the remote gateway is configured, you need to import users and assets from Active Directory, then map the necessary assets to users and domain accounts from which remote connections to the target devices will be initiated.
Refer here for the steps to import users from Active Directory.
Learn more about the privileged account discovery process here.
3. Map user to assets
You can allow your users to launch remote connections to specific resources using the AD account with which they have logged in to Securden. In addition, if the user has any accounts that are classified as 'Personal Domain Account' account type, the user can use those account names too to launch the connection. In this step, you can associate the IT assets with the users. This association permits them to launch the connection with the assets allotted.
Refer here for the detailed steps on user – asset association
4. Map domain accounts to assets
If any domain account is used to remotely connect to multiple IT assets, creating an association between the domain accounts and the list of IT assets it could connect to, becomes necessary.
Typically, an asset is associated with specific users/user groups and accounts/folders in Securden. That means, you will specify ‘who’ can launch a remote connection to ‘what’ asset using ‘which’ domain account.
Once the association is made, the asset will appear in the list of remote session launch options for the specific domain account for the specific users. You can create any number of such associations from this section.
Refer here for the detailed steps on domain accounts – asset associations:
5. Configure account details in RDCMan
After installing the RDCMan application on end-user machines, users must configure their domain and/or user credentials within the application to initiate connections. You can import account details by navigating to the 'File' section of the menu bar or you can manually enter them.
Once the details are imported, click on the ‘Connect to’ button present on the ‘Sessions’ menu or double-click on the imported IP number to launch connection. Here, you will have to configure the details and credentials of the jumphost device where SSM is configured.
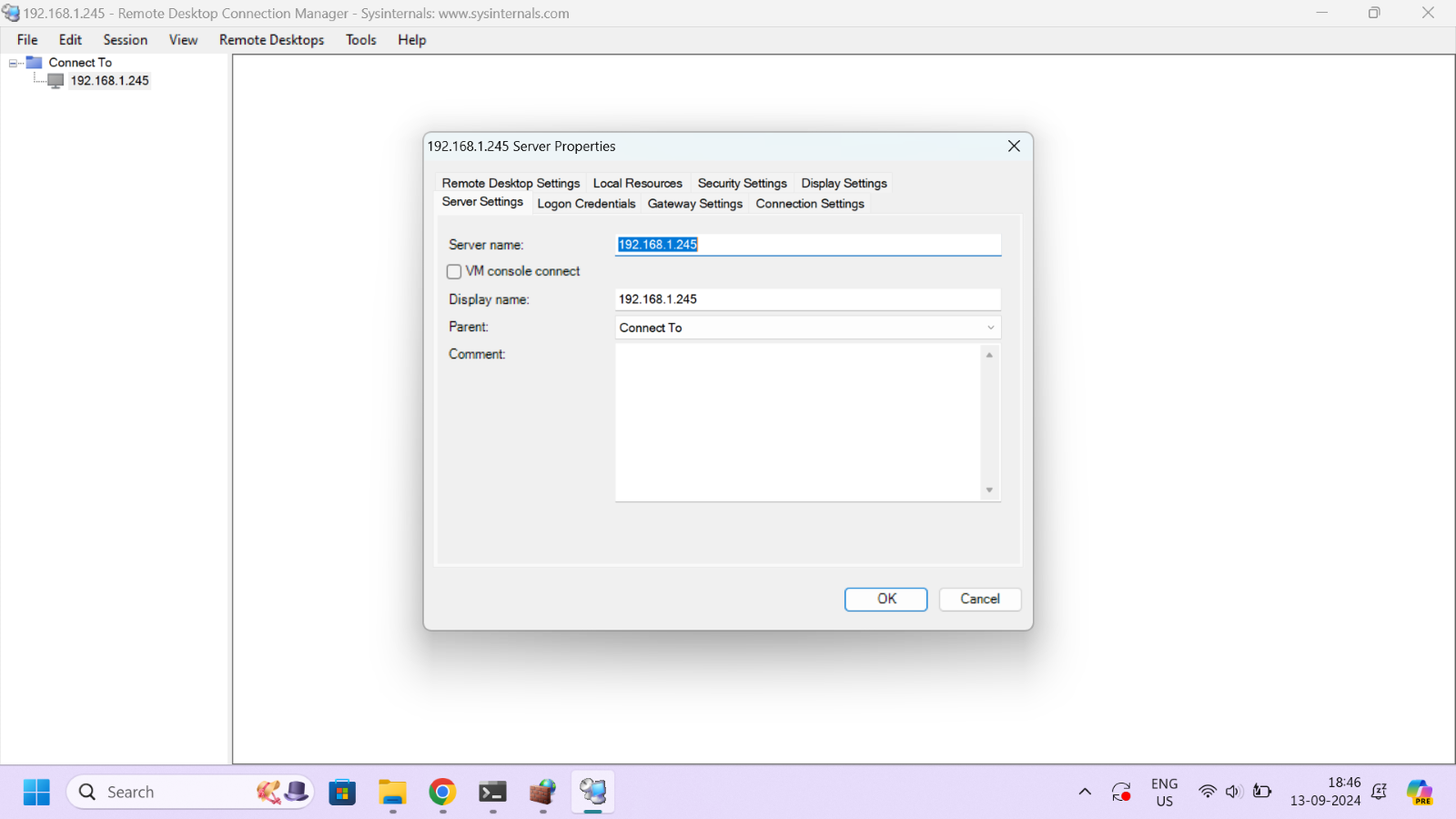
Right-click on the imported details to open the 'Server Properties' dialog box. Go to the 'Server Settings' tab and enter the IP address or FQDN of the jumphost with SSM installed in the 'Server Name' field. In the 'Display Name' field, enter the IP address or FQDN of the target machine you are connecting to.
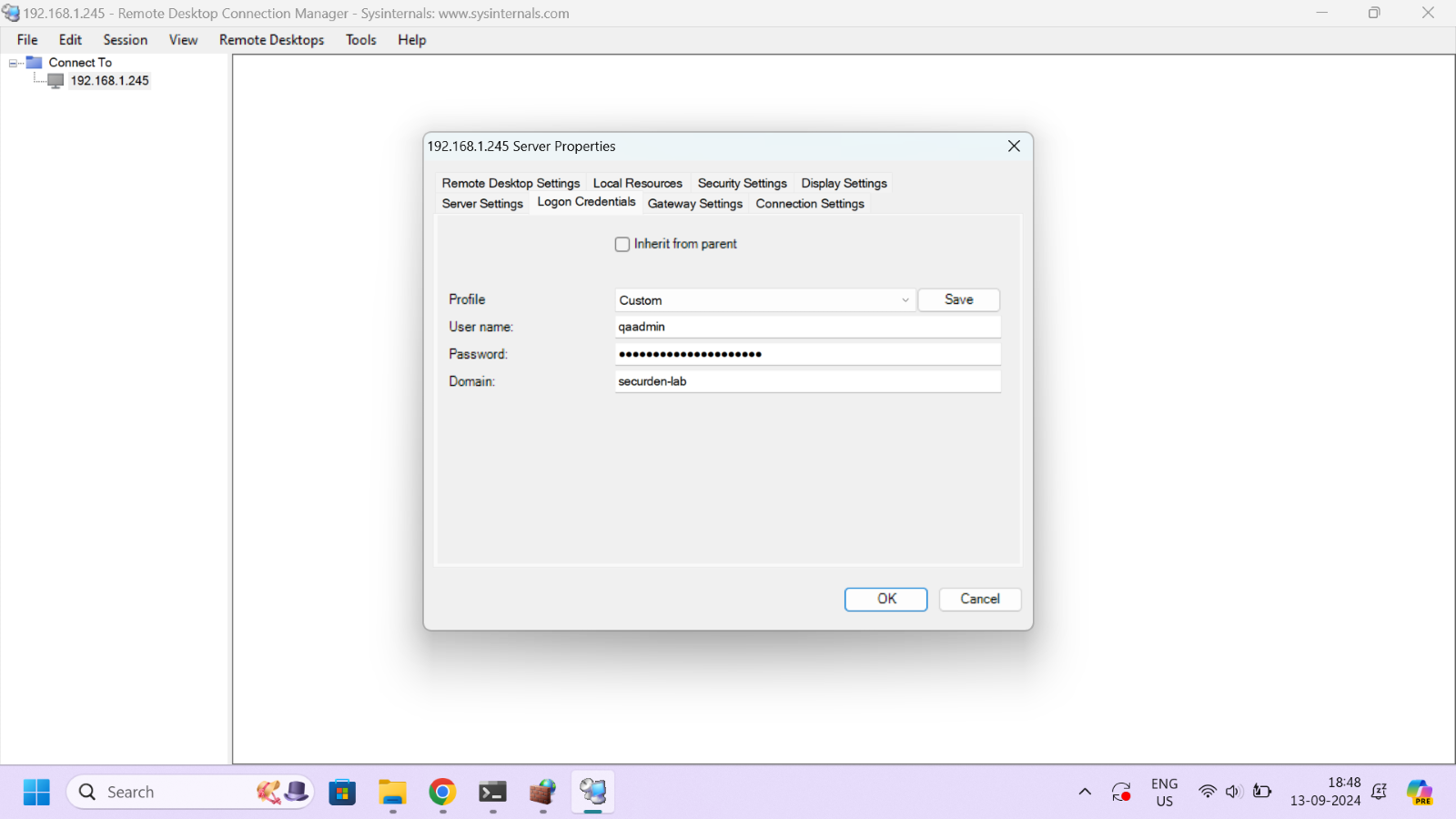
In the 'Logon Credentials' tab, enter the login credentials, including the username and password, for accessing the jumphost device with SSM installed. You can log in using the domain user’s credentials, who have been imported onto Securden. The user should have ownership or shared access to the account used for initiating the connection.
Navigate to the 'Connection Settings' tab in 'Server Properties' and enter a command string in the 'Start Program' field to initiate the connection. This command string plays a crucial role in establishing the connection.
The 'ssm' at the beginning of the command string is the executable that initiates the remote connection. The '/u' specifies the account, and if a domain is required, it should be entered before the account name. The '/v' denotes the asset identifier or FQDN of the account to which the connection is being established.
For instance, if you're initiating a connection using a domain account, the command format would be:
ssm /u Securden\Administrator /v 172.30.31.2.
If the connection is being established from the logged-in user’s account instead of a domain account, the command string should directly include only the asset identifier or FQDN. For example, the format would be: ssm /v WIN-IV6LRJ3VSPD.securden.com.
All remote sessions initiated through RDCMan are stored in the Unified PAM interface. You can view both 'Active Remote Sessions' and 'Recorded Sessions' under the 'Sessions' tab of the product.
