Running Discovery on Windows Servers¶
Prerequisites¶
To perform remote operations on Windows devices, you need to import your AD domain into Securden. This can be done separately or at the time of discovery. To connect to your domain, you must satisfy the following requirements.
-
Ports 389 (For Non-SSL) and port 636 (For SSL) must be open to Securden PAM.
-
AD Reachability – The active directory must remain connected to Securden PAM.
-
If the users are restricted from logging in from multiple computers, login permission should be allowed from the securden server also.
Securden scans the active directory in Windows servers to obtain the AD domain's OUs, Groups, and Computers. Along with them, the local admin accounts, domain accounts, and service accounts present on the servers are also obtained.
Once computers are discovered, Securden scans each device for the domain accounts used as service accounts to run services, scheduled tasks, and IIS App pools.
Accounts discovery is a two-step process. The very first step is to establish connectivity between Securden and the Active Directory. Then, the required OUs, groups, computers, and accounts can be selected and imported into Securden. The steps are explained in detail below.
Step1: Connecting to the Active Directory Domain¶
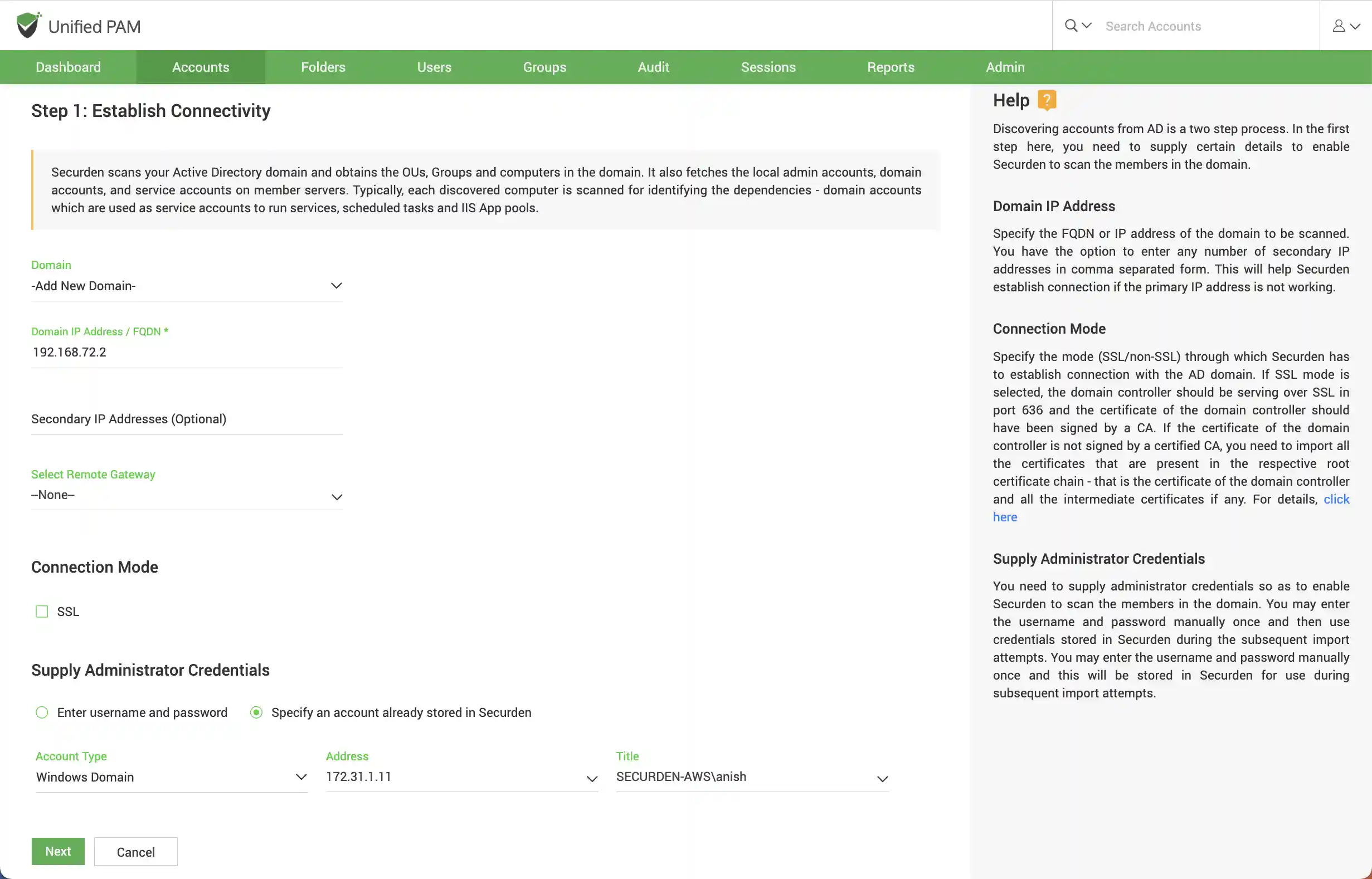
To establish connectivity between the computers and Securden, you need to furnish details of the Active Directory domain.
Navigate to Admin >> Integrations >> Active Directory >> Domains.
FQDN/IP Address
To establish connectivity with the AD domain, you need to specify the FQDN/IP address of the domain. The FQDN/IP can be supplemented with secondary IP addresses to establish connectivity in cases where the primary addresses are not working.
Connection Mode
You can specify the mode of connection (SSL/Non-SSL) between Securden and the AD domain. If you select SSL mode, you need to ensure that the domain controller is serving over SSL in port 636. Additionally, the certificate of the domain controller should be signed by a certified CA. If the certificate is not signed by the CA, you can import all the certificates that are present in the root certificate chain (the certificate of domain controller and all the intermediate certificates if any).
Supply Administrator Credentials¶
You need to supply administrator credentials to enable Securden to scan the members in the domain. You may enter the username and password manually for the first time. The username and password specified will be stored in Securden for subsequent import attempts.
Note
AD domains can be added before running the accounts discovery process by using the AD integration option. To add the active directory domain, navigate to Admin >> Integrations >> Active Directory >> Domains.
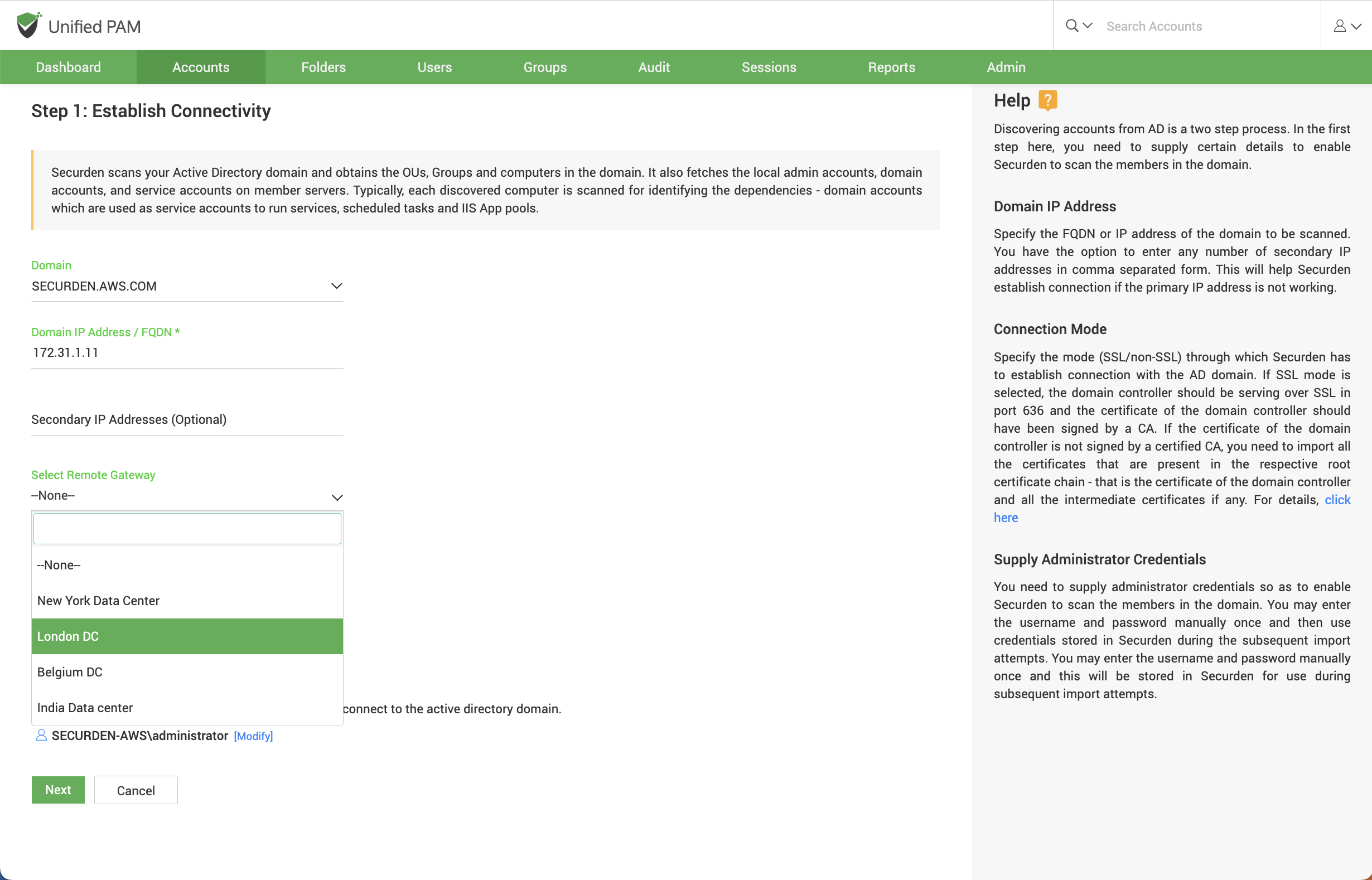
Connecting to AD Domains on Secondary Networks¶
If you have configured a distributed deployment setup in Securden using an API-based application server, you can explicitly run the discovery on the secondary network to scan for devices and databases and obtain the accounts from them.
To establish connectivity between Securden and the AD domain, you can follow the same steps as above. Additionally, while establishing connectivity, you need to route the connection through the remote gateway associated with the API-based application server.
You may select the required gateway from the drop-down menu as shown below.