Ephemeral Access¶
Securden Unified PAM allows users to launch connections to target systems within the organization’s IT environment via an ephemeral (temporary) user profile created at the time of connection initiation. This adds an additional layer of security to remote connections, effectively eliminating the risk associated with standing privileges.
Pre-configured for specific user and asset combinations, ephemeral user profiles are generated when a connection to the target asset is initiated. These profiles grant only the minimum privileges necessary for the user to perform their tasks on the target machine. Once the activity is complete, the account and any associated artifacts are deprovisioned and rendered obsolete.
Ephemeral access is particularly useful for third-party vendor and contractor access but can also be applied within the organization.
Here’s the sequence of steps you need to follow to enable ephemeral access in Securden Unified PAM.
- Modify Configuration Settings
- Enable Ephemeral Access
- Verify Remote Operation Credentials
Modify Configuration Settings¶
To authorize ephemeral user profile creation for a user-asset combination, you need to first enable certain configurations under Customization. To do this,
-
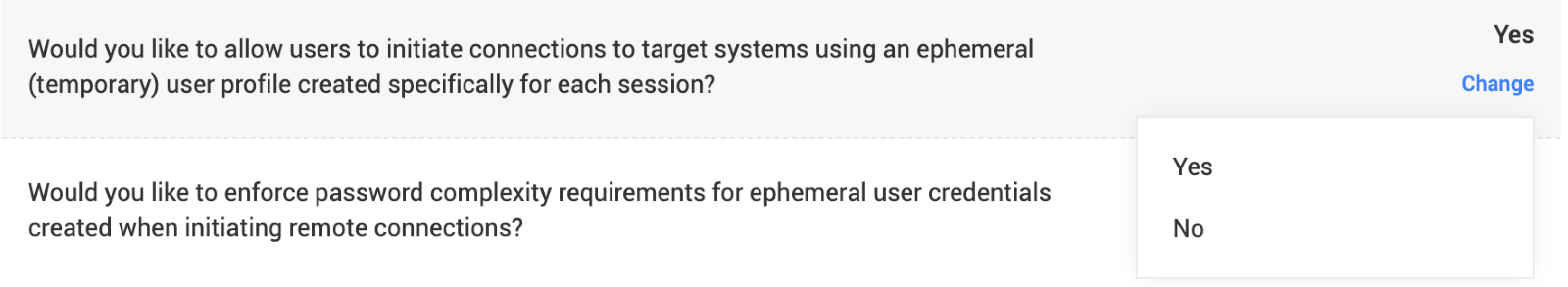
Navigate to Admin >> Customization >> Configurations in the Securden Unified PAM user interface.
-
In the window that opens, search (Ctrl+F or Cmd+F)
 for the configuration: “Would you like to allow users to initiate connections to target systems using an ephemeral (temporary) user profile created specifically for each session?”
for the configuration: “Would you like to allow users to initiate connections to target systems using an ephemeral (temporary) user profile created specifically for each session?”
-
Click Change and select Yes from the drop-down.
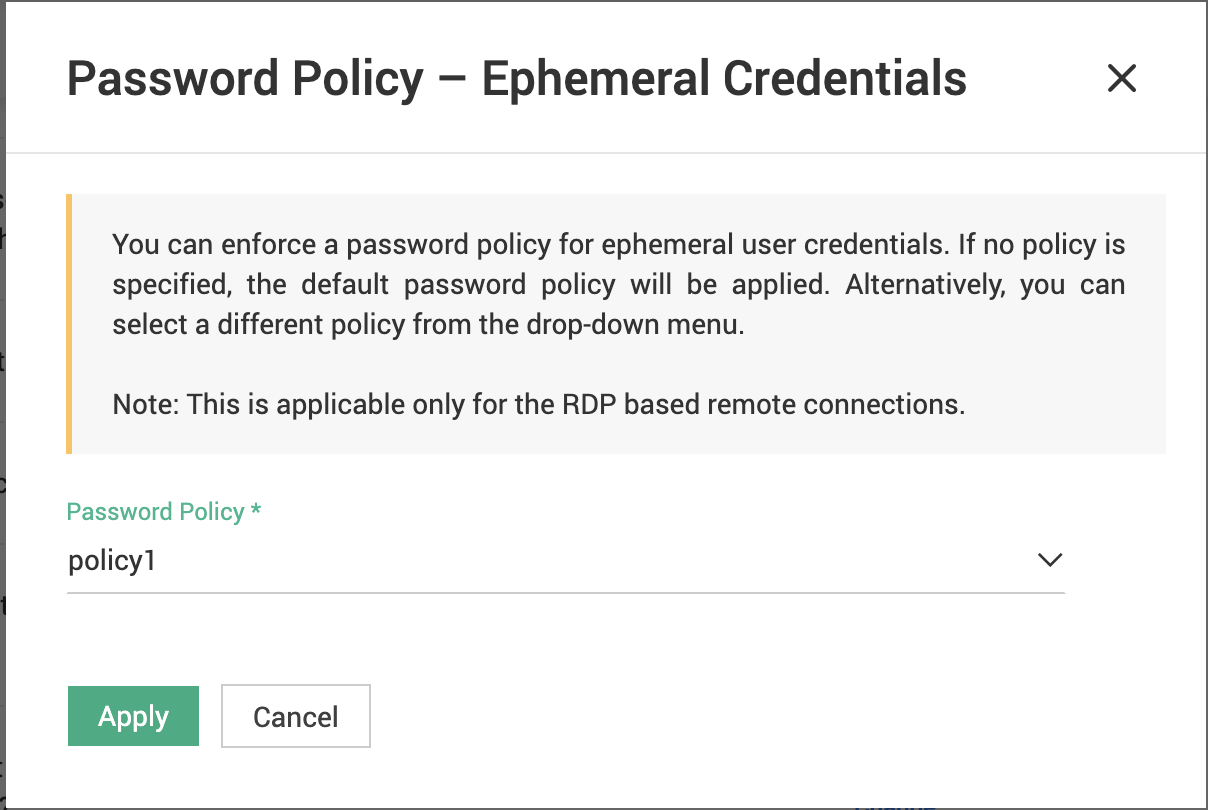
To set password policy for the ephemeral credentials created,
-
Search (Ctrl+F or Cmd+F) for the configuration:
“Would you like to enforce password complexity requirements for ephemeral user credentials created when initiating remote connections?”
-
Click Change and select the required password policy from the drop-down.
Note
If you don’t specify any password policy for ephemeral credentials, the default password policy will be applied.
Once the necessary configurations are applied, a success message will be displayed. The changes made to configurations are also captured as audit trails and can be found under the Audit tab.
Enable Ephemeral Access¶
To enable ephemeral access for specific user-asset combinations,
-
Navigate to Admin >> Remote Sessions and Recordings >> User – Assets / Applications Association
-
Click on the ‘edit icon’ beside the required user-asset mapping for which you want to enable ephemeral access.
-
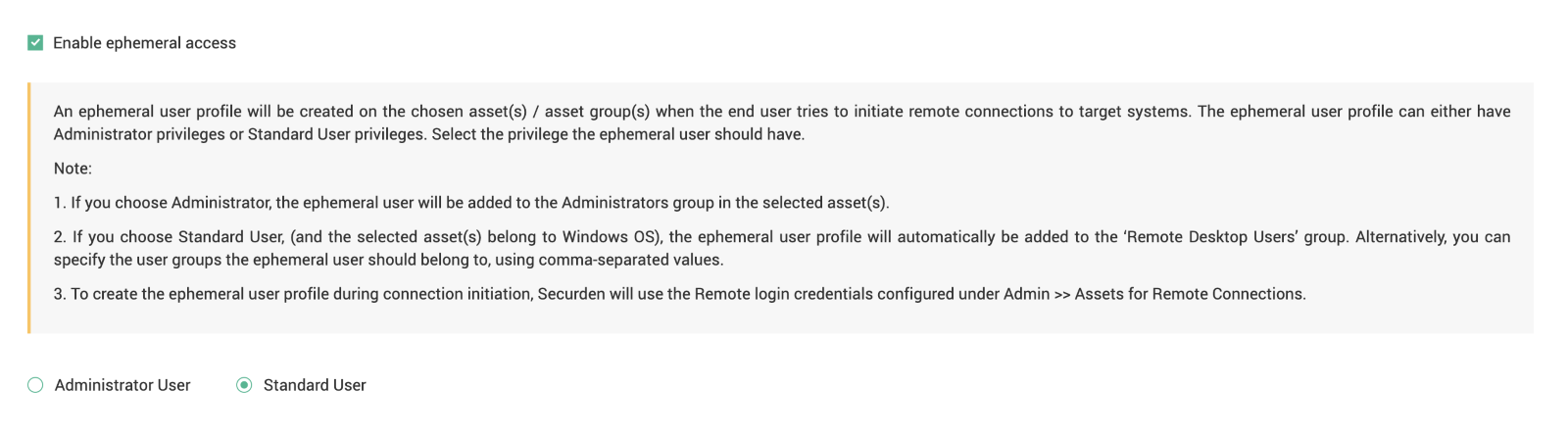
In the window that opens, select the checkbox Enable Ephemeral Access
-
You can choose to provide either administrator privileges or standard user privileges for the ephemeral user profile being created. Select the option required.
-
If you choose to grant standard user privileges, the new ephemeral user profile being created is added to the group ‘Remote Desktop Users’ users in the target asset by default. Alternatively, you can specify the user groups the ephemeral user should be added to, using comma-separated values in the text box below
-
Once you have added all the details, click Save.
When a user associated with the above user-asset pairing initiates a remote connection to the corresponding target asset, a new ephemeral profile is created on the target asset at the time of connection, following the criteria mentioned above.
Note
If you want to configure remote access for new user-asset combinations that don’t already exist in Securden, you need to first define the required user-asset/application mapping. To do this, refer to the step-by-step instructions mentioned here
Verify Remote Operation Credentials¶
To authorize ephemeral user profile creation on target assets during connection initiation, Securden Unified PAM requires sufficient privileges on the target asset to create a new account.
Securden uses the remote operation credentials specified for asset groups under Admin >> Assets for Remote Connections to create the new account. You need to verify if the remote operation credentials are valid for assets that are configured for ephemeral access.
Note
If you have already configured remote operation credentials before, you may skip this step.
To verify remote operation credentials,
-
Navigate to Admin >> Assets for Remote Connections
-
Choose the asset group(s) for which you have configured ephemeral access earlier.
-
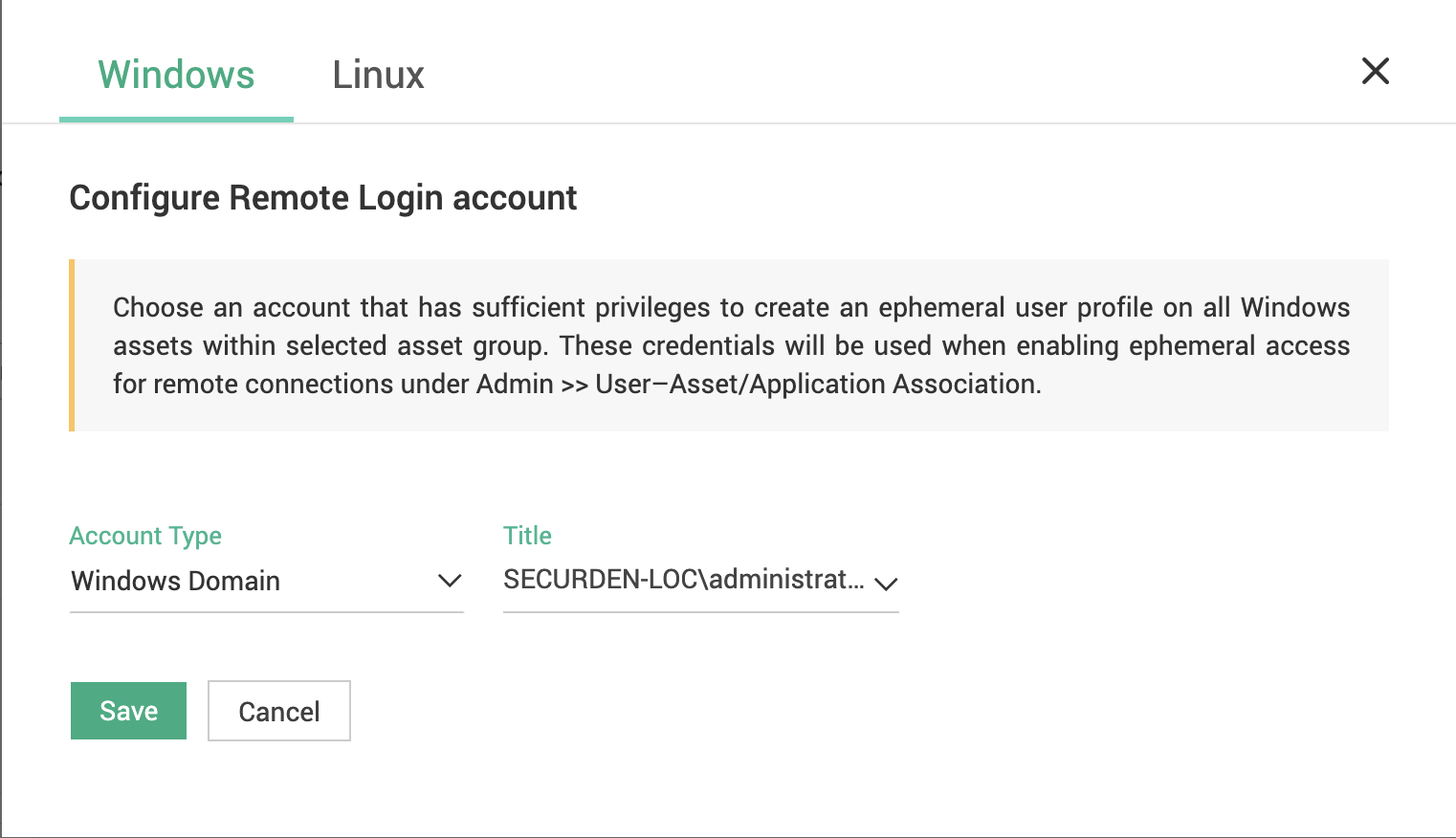
Click Remote Operation Credentials (
 ) icon beside the asset group.
) icon beside the asset group.
-
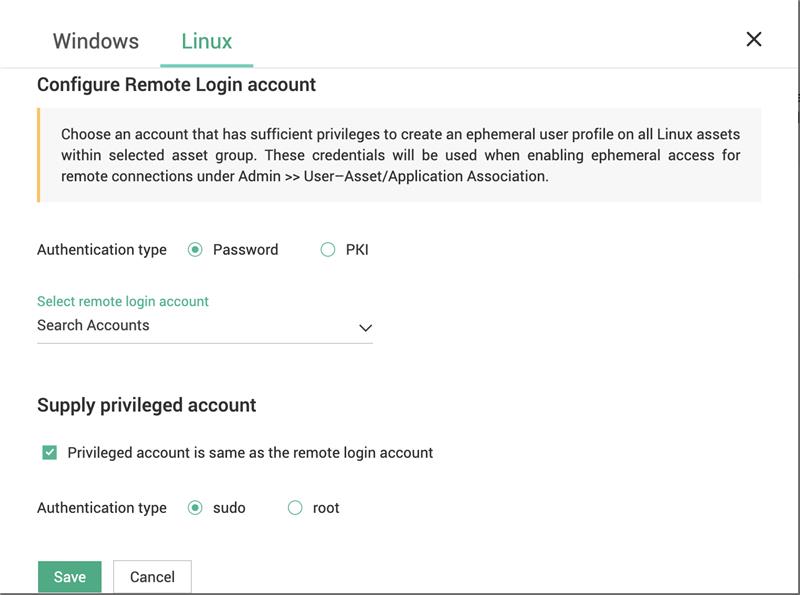
In the window that opens, choose an account that has sufficient privileges to create an ephemeral user profile on all assets within the selected asset group.
-
Repeat the same process for both Windows as well as Linux assets.
-
Once you’ve chosen the appropriate accounts, click Save. The configured account will be used to create ephemeral user profiles on target assets for applicable user-asset combinations.